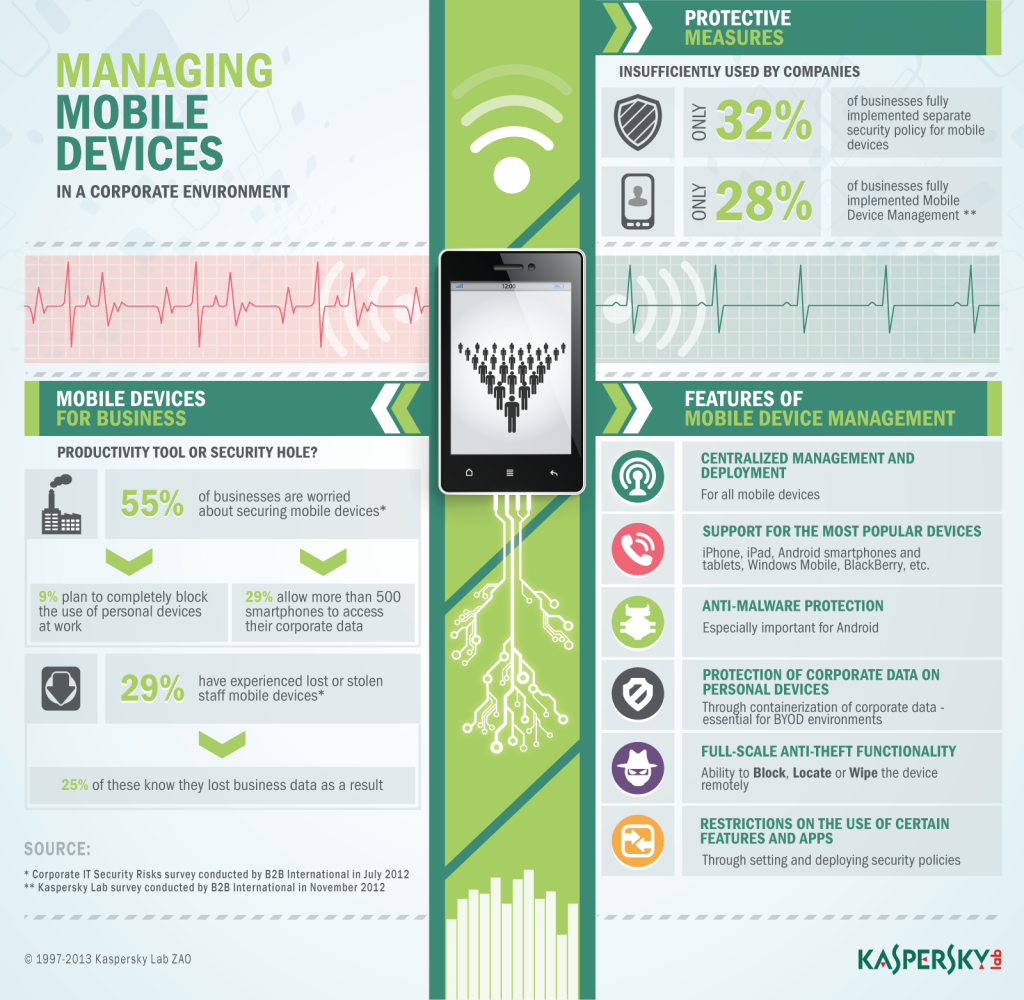
The system administrator – also sometimes affectionately known as the computer guy/girl – is a fairly well known figure at any company with more than a handful of employees. Stereotypes abound for sysadmins, and even sitcoms are made about the genre. But a lot of those are out-of-date and silly generalizations (my sysadmin @ HQ is neat and well-groomed – verging on the Hipster, with long blond fringe and side parting!)
So, really, just who is the sysadmin?
Right. All of us – computer users – are divided into three categories in terms of the answer to this question. To the first category, a sysadmin is an angry bearded devil, a computer whiz(ard), and a shaman – all rolled into one. The second category also attributes to sysadmins certain otherworldly traits, but strictly positive ones worthy of repeated bows plus a small gift on every worthy holiday (especially Sysadmin Day). Then there’s the third category of computer users – who don’t take either of these two views of sysadmins; these folks understand they’re just normal folks like the rest of us. And this third category includes the sysadmins themselves!
The shamanic work of sysadmins is eternally interesting: assembling brand new shiny kit, connecting it up with cables (or without them), and also commanding control over mice and keyboards – sometimes from thousands of miles away – and installing or reconfiguring software on a comp from the comfort of their own workplace. However, at the same time the work is hard, incredibly accountable, and, alas, in part thankless.
First of all there are the hundreds or thousands of users who all need to be kept happy – most of them clever-Dicks! Then there are the ever-increasing numbers and types of computers and other newfangled devices – all of which need attention and care. And of course there’s the jungle of software, cables and routers, problems with security… And to top it all off there are the ever-present budgetary constraints and dissatisfaction of the management and users. So it should come as no surprise that only sysadmins with iron psyches and healthy, cynical attitudes to life are the only ones who can cope with the job!
Perhaps the biggest headache for sysadmins is how to physically manage all the tasks under their remit. Installing Office here, correcting a setting in Outlook there, connecting a new comp in the neighboring building, and then getting through another 48 tasks scattered all over the office(s) is all going to result in nothing other than sysadmin burnout! Enter systems management to ease the burden…
The majority of routine operations for controlling a network can either be fully automated, or at least performed remotely, without excessive movement about the office. Upgrade an OS on a comp? Install an application? Check what software is installed on the chief accountant’s laptop? Update antivirus and scan a computer for vulnerabilities? Prolong a license? Correct some pesky setting that’s preventing a program from working as it should? All that and a lot more the sysadmin can do today without leaving his/her room with the help of the same systems management. And just think of the improved productivity of labor and lowering of costs! And how much simpler the life of the sysadmin becomes!
In the early 2000s a control system for the security of a network appeared in our products. It formed a teeny-weeny (but oh-so important) part of systems management, responsible for the monitoring of protected workstations, installation and updating of antivirus, and so on.
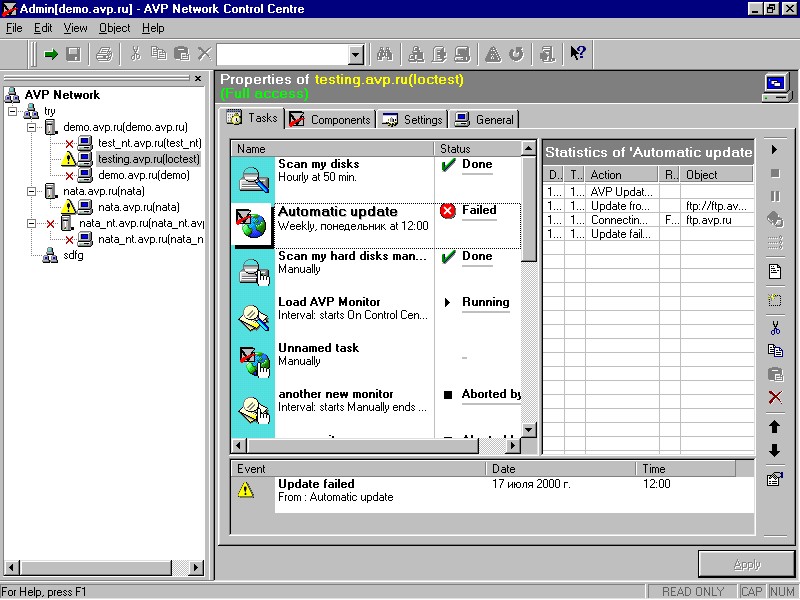
More: 10 years later…