February 26, 2013
MDM: Mobile Discipline Mastery.
You’ll no doubt concur with the following observation:
You see them everywhere: folks in elevators, coffee shops, subways, taxis, airports and airplanes, at concerts and parties, on sidewalks, and in darkened cinemas (dammit!), in fact, folks in just about any situation possible – you’ll always find some – no, lots – of them concentrating on, and/or tapping away at the touchscreens of, their smartphones and tablets. And let’s face it – you too do the same, right? (Apart from in the darkened cinema, of course :)
So just what is it these perennial smartphone tappers are up to? Gaming? IMing? Watching movies, or reading the news or an e-book?
All are possible. But more often than not I’ve been observing that at any given convenient moment, any time of day or night, and in any weather, lots of folks tend to be checking their work email and solving work tasks. Yep, on their own absurd-money smartphones! Outside business hours. Without coercion and with plenty of enthusiasm, or, at least, without grumbling :). I sometimes even see them sighing and unconscious pouts forming upon their lips in disappointment that no one’s writing to them!
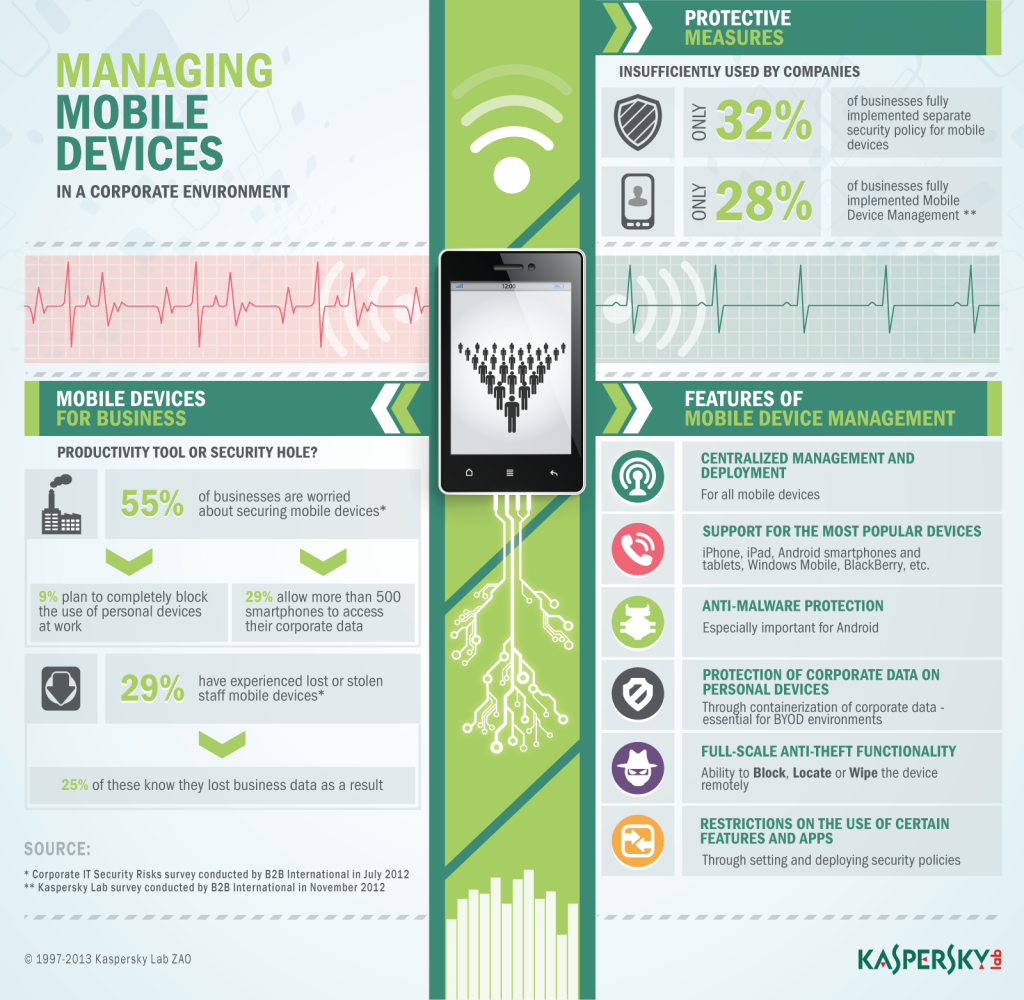
So why all this 24/7 “at the office, kinda”, all of a sudden? Maybe it’s a cunning virus that infects users’ brains directly from the screen? (Hmmm, that gives me an idea for April 1, 2013:) Or is it that the business management gurus have had it wrong all along re employee motivation? All that was needed in fact was to just connect pretty little glass devices armed with an Internet connection – bought by the employee I might add – to the corporate network! What could be simpler? And that’s exactly what’s been happening; here’s proof: according to Forrester 53% of employees use their own devices for work.
Seems a bit strange, but the fact is many people don’t mind using their personal mobile devices one bit for work purposes. But why? Why would they? Why should they?… Well, a lot of interesting theories do crop up regarding this, but I’m afraid they’re all outside the remit of this post. Still, it’s an interesting topic – have look on the net. To me though the main reason is the social-network-ization of the modern urban individual, which itself has of course been made possible by the underlying enabling technologies – social networks plus the total connectedness of smartphones and tablets. Corporate informational networks have been turned into another social network – a work one, where employees are in constant contact with the colleagues they know and even those they don’t. A social network at work! Anyway, like I say, the why’s and how’s of all this sure are interesting, and by no means simple – there’s plenty to think about… but like I said, that’s for another time and another place.
What is for today is informing – or reminding – you that this phenomenon is already so widespread that it’s been given an ‘official’ title: BYOD – Bring Your Own Device: using your own device for work tasks.
According to Forrester, “53% of employees use their own devices for work”. And Cisco’s come up with another interesting figure – 90% – which is how high it reckons mobile-generated traffic’s going to go in 2016. Strewth! But there’s really no need for citations here. Just think about your own overall shift to the mobile platform.
BYOD: four letters which in a few years have turned upside down the notions of: the organization of labor, motivation, corporate ethics, productivity, communications, leisure, and a lot more besides… and not forgetting of course one more notion – that of security.
For employers considering BYOD, they’ve got a simple choice to make: either to allow or to forbid employees using their own mobile devices for work, and this has direct implications for security: either to adapt security to the new BYOD situation, or to just lock it all down (reject BYOD outright), respectively. The latter route is of course the simplest, but comes with a lethal side-effect: lower productivity – caused by stuck-in-the-past tech-rigidity not permitting productivity-raising flexibility, plus the demotivation of those who’d prefer the flexibility and convenience of own-device-assisted jobs. The former route is tricky, prickly, and expensive… but still doable – and totally worthwhile.
There is an alternative of course – to hand out standard corporate smartphones, and to install thereon all the necessary security, protection and monitoring you’d ever need. But for that a company needs to dish out a great deal of the dough, and then there’d always be some employees not satisfied with such an employer-decided arrangement – those who don’t want to carry around with them two phones, etc., etc., moan, moan, moan… so rises in productivity and motivation may not occur anyway.
So, getting back to BYOD – let’s have a look at it from the point of view of my inner, totally paranoid system/security administrator:
First things first: an uncontrollable number of uncontrollable personal devices get connected to the corporate network – devices about which nothing is known (and unknowns and security are hardly good bed partners). Access is granted to these devices, but how it actually gets used – and possibly by whom – remains unknown.
Next thing: these devices contain a higgledy-piggledly mix of both personal and corporate data. As a rule users are not all that concerned about the security of sensitive corporate data (while employers sure are), often losing their devices or having them pinched with all sorts of catastrophic unexpected consequences. They also are frequently poorly acquainted with the principal rules of mobile hygiene, incorrectly configure their devices, and even commit critical security no-nos unwittingly.
Meanwhile, the cyberswine are always actively honing new vectors for targeted attacks on corporate networks via mobile devices.
Finally, the sys-admins don’t know what employees are doing with their devices – transferring what to whom, or receiving what from whom, etc., etc.
So though there are many obvious advantages to BYOD, plenty of questions arise at the same time…
For large organizations the number of connected personal devices can reach the tens of thousands. So how is it possible to bring some mobile discipline mastery to them all – to ultimately conduct a symphony that’s pleasant to the ear of the admins given the awful initial cacophony made by all those different, uncontrollable devices? How do you protect, monitor, and manage this pasticcio? Enter MDM – Mobile Device Management; rather – our MDM, naturally!
As promised, here I’ll be telling you in installments about the various innards of our new corporate product, and I can’t think of a more logical place to start than with MDM…
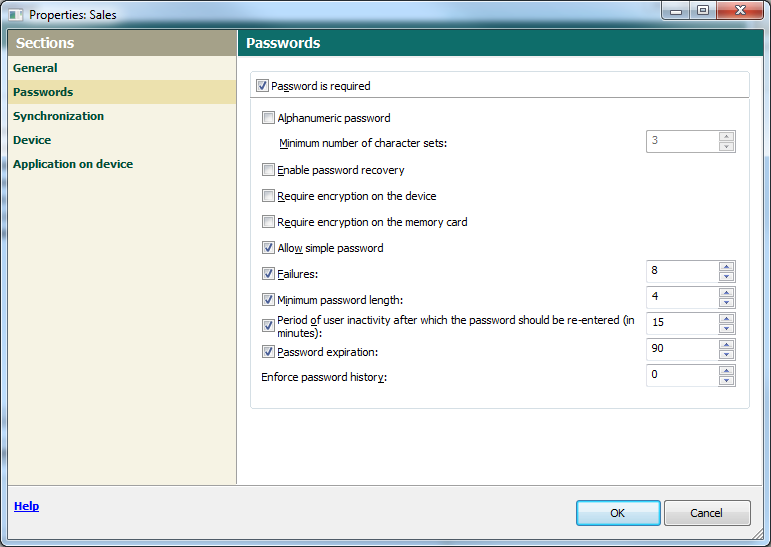
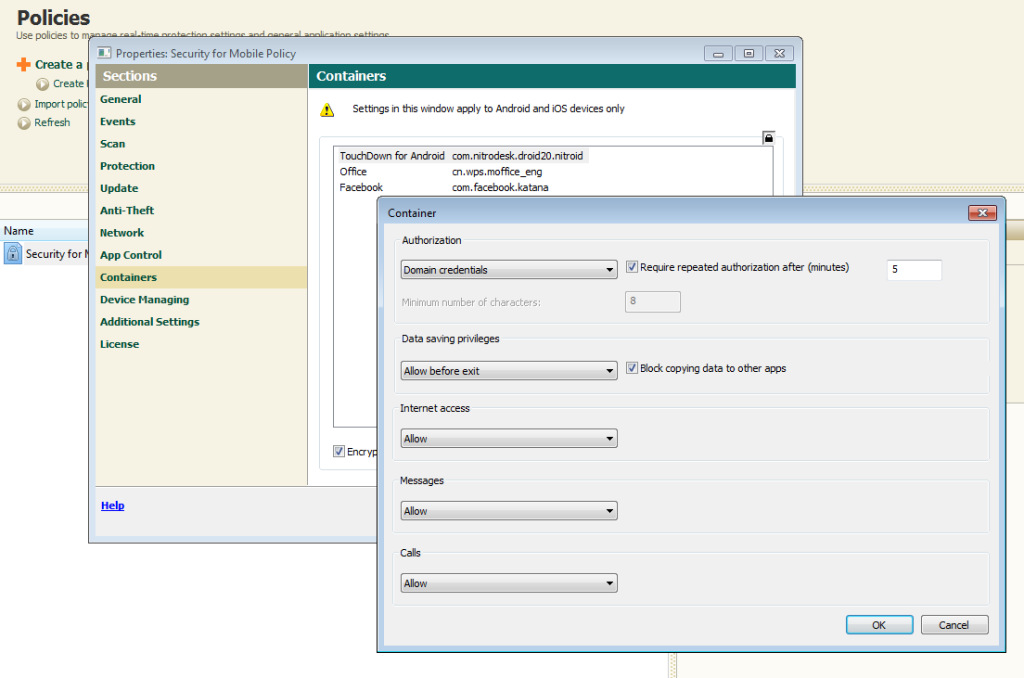
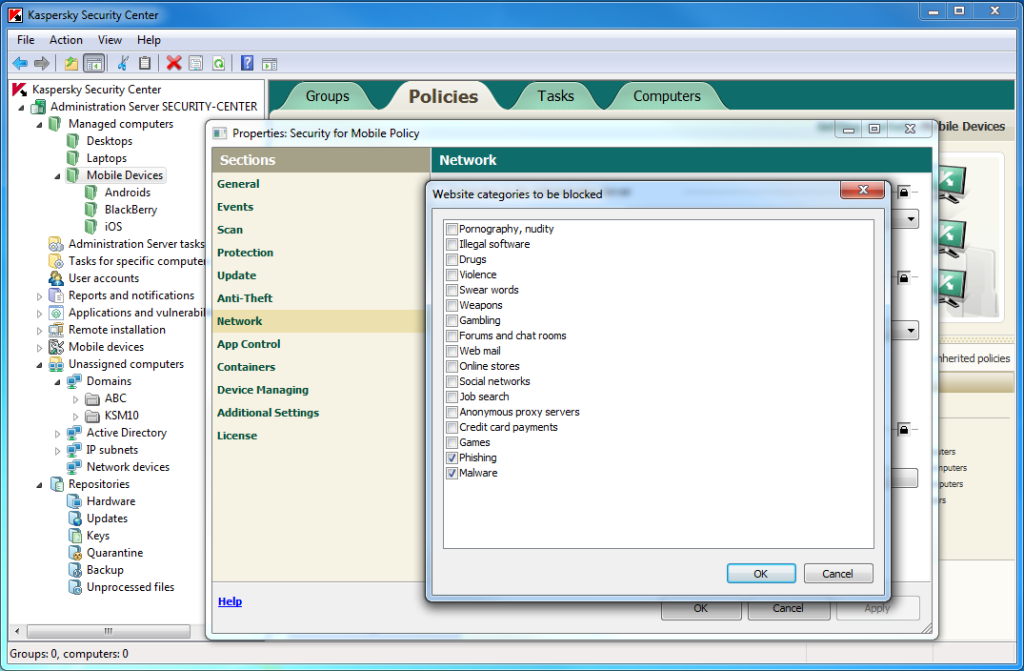
We’ve designed our MDM with a classic client-server architecture. A control server is connected to the corporate network, to which in turn are connected all the different mobile devices employees have – be they iOS, Windows Phone or Mobile, Android, Blackberry, or Symbian. All the functionality of Microsoft Exchange ActiveSync and Apple MDM is supported – which is mega-handy as with them administrators can determine the strength of passwords on connected devices, enforce encryption processes, block the use of cameras, and a lot, lot more…
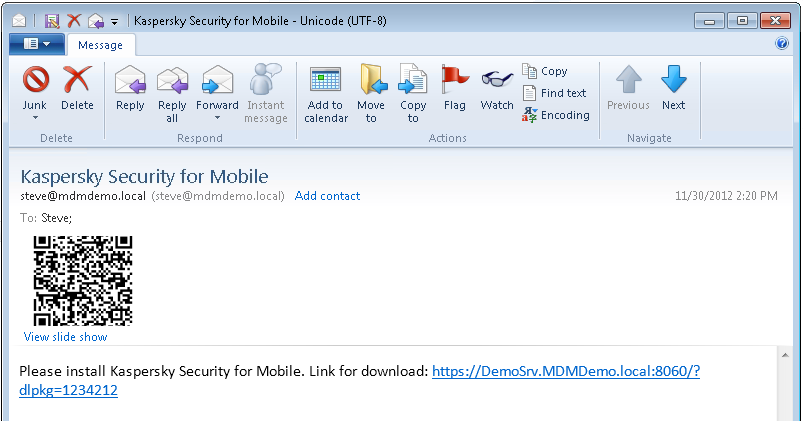
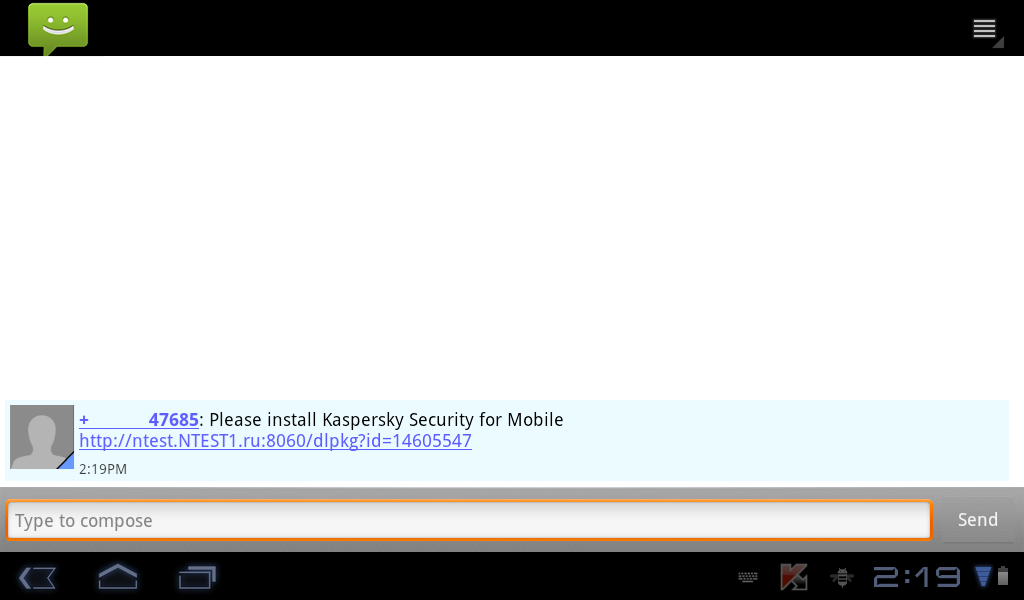
Devices are connected in three ways: via a QR code, an SMS text, or a direct link in an email. No manual input of long links is needed on devices, and there’s no need to visit your allocated computer guy. An employee simply needs to get to the right cyberaddress, and his/her device is automatically connected to the control server. Piece of cake.
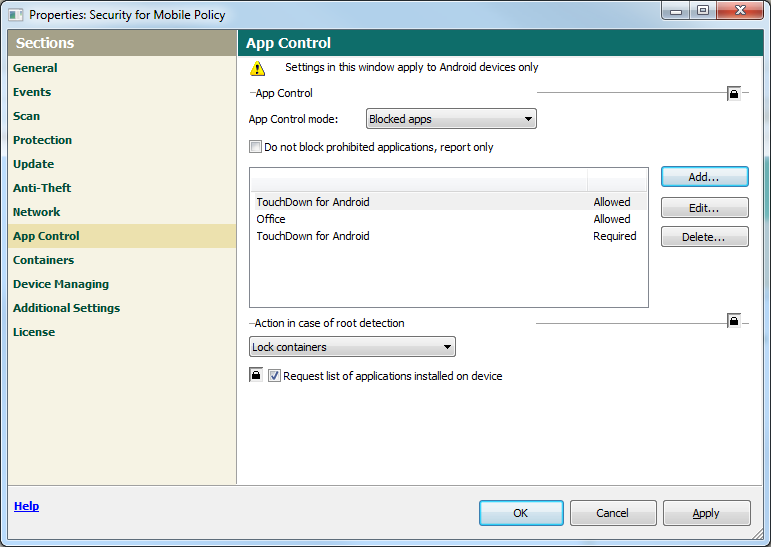
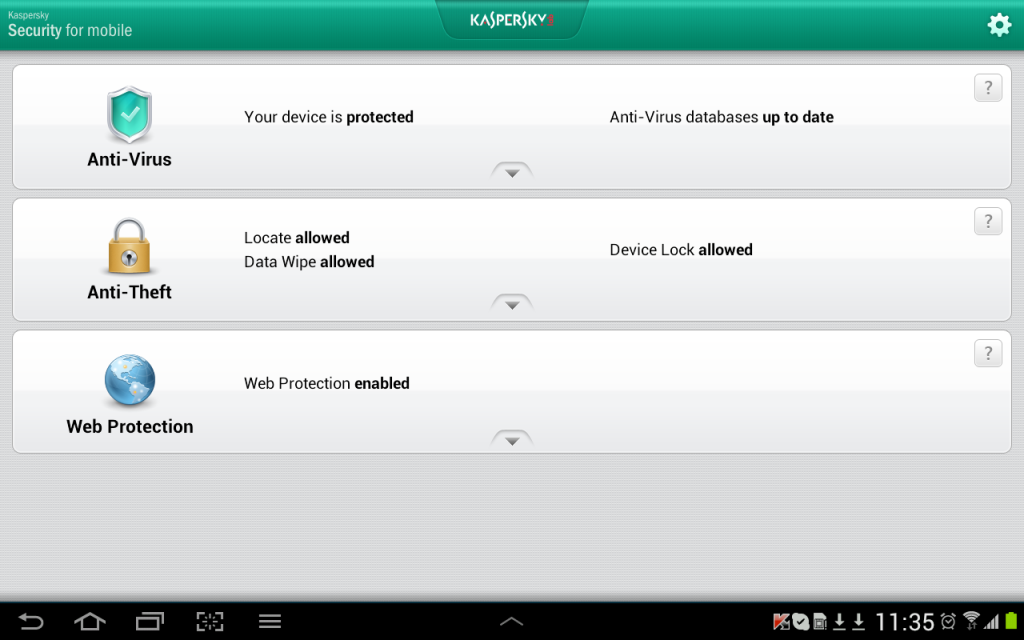
Once a device is connected to the control server the administrator gets an array of real useful features to manage and protect the device. Examples: the initial configuration of the system, installation of profiles for mobile corporate email, policies enforcement, installation and updating of software, deletion of incompatible/undesirable programs, software inventory, monitoring and preventing attempts at rooting and jailbreaking, and much more besides.
Herewith, more detail on three of the most important features:
Separated data encryption. This is perhaps best described via a real life example. You come home, and on tired-out auto-pilot you put your tablet on the hall table and proceed to the kitchen for some serious feasting. While getting stuck into the main course your offspring decides to get hold of it (your tablet, not your main course) and do all sorts of thoroughly inappropriate mischievousness therewith (like chatting via corporate IM or tweeting from the business account). Oops. And this is where containerization comes speeding to the rescue – separating corporate data from personal data on the device. Data in a container can be encrypted, access thereto limited, and even remotely deleted (for example, when an employee leaves the company), while personal data stays untouched.
Application Control. The company can create an internal corporate app store where trusted mobile apps can be acquired. Apps can also be sent to users via links or QR codes, getting rid of the need for an administrator to go to (non-admin rights holding) users and install them manually. And upon an employee leaving the company – these apps can be deleted remotely. The result: automization of the life cycle of business applications, protection of sensitive corporate data, and (again!) admins’ burden being significantly lightened.
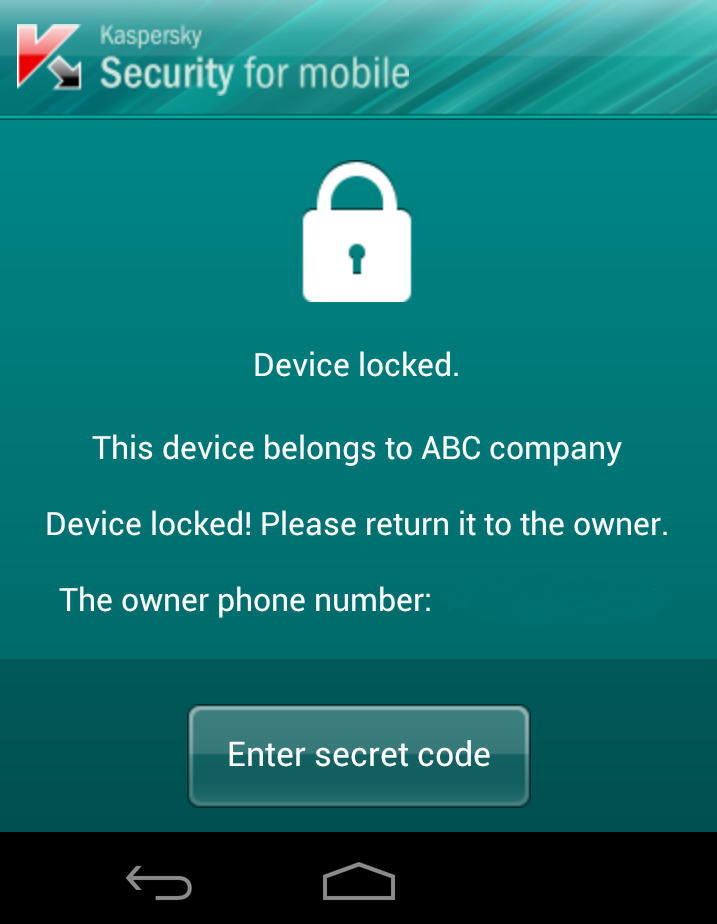
Additional protection. Besides traditional antivirus, proactive and cloud protection, there’s also forced mobile device encryption, secure web browsing, and a full suite of antitheft functionality including data deletion, location tracking, and covert photo’ing (which works even after the SIM card has been changed).
Key here is that all these MDM trappings are managed via our Security Center. This represents another great advantage, since from a single console it’s possible to control not only the protection of mobile devices, but also the whole network, including anti-malware, Application Control, encryption, etc., etc. on workstations, servers, virtual machines, and so on.
So you’ll have got the picture by now. BOYD needs to be carefully thought through from the security standpoint; that is, properly integrated into the corporate IT infrastructure. And as I’ve just explained, that task is now easily solvable.
More interesting stuff about MDM can be found in the datasheet.