What’s the No. 1 most unpleasant pain in the xxx thorn in the side of the modern-day cyber-world in terms of damage, evil sophistication, and headline-grabbing the world over? Can you guess?…
Ah, the title of this post may have given it away, but yes, of course, it’s ransomware (aka cryptomalware, but I’ll stick with the simpler, less tongue-twisting, and professional term ‘ransomware’).
So: ransomware. Bad. How bad?…
Well, it’s actually so bad, and has been so consistently bad for years, so deeply embedded in all things digital, and has so overwhelmed so many large organizations (even indirectly being followed by human deaths), which (large organizations) have forked out so much money to pay ransoms for, that the world’s news media has become almost indifferent to it. It’s stopped being headline news, having been transformed into an every-day casual event. And that’s what’s most worrying of all: it means the cyber-scumbags (apologies for such a strong language, but it’s really the best way to describe these folks) are winning; cyber-extortion is becoming a seemingly inevitable reality of today’s digital world and it seems there’s nothing can be done about it.
And they’re winning for three reasons:
Third (I’ll start at the end): the ‘big boys’ are still playing their schoolyard geopolitical games, which blocks national cyber-polices exchanging operational information for coordinated searching, catching, arresting and charging of ransomware operators.
Second: users aren’t prepared – resilient – enough to respond to such attacks.
And first (most important): not all washing powders are the same anti-ransomware technologies are equally effective – by a long way.
Often, ‘on the tin’, anti-ransomware technologies featured in cybersecurity solutions are claimed to be effective. But in practice they don’t quite do exactly what it says on the tin, or – if they do, consistently. And what does this mean? That users are scandalously unprotected against very professional, technically sophisticated ransomware attacks.
But don’t just take my word for it. Check what the trusted German testing institute – AV-TEST – say. They’ve just published complex research on the ability of cybersecurity products to tackle ransomware. They paid no attention whatsover to marketing claims (à la ‘this deodorant is guaranteed to last for 48 hours’), and didn’t just use widely-know in-the-wild ransomware samples. They besieged several of the top cybersecurity solutions in real ‘battlefield’ conditions, firing at them all sorts of live-ammunition ransomware artillery that’s actually out there today. As mentioned, no in-the-wild samples, but those technically capable of weaponizing a ransomware attack. And what did they find? On the whole – something thoroughly shocking and scary:
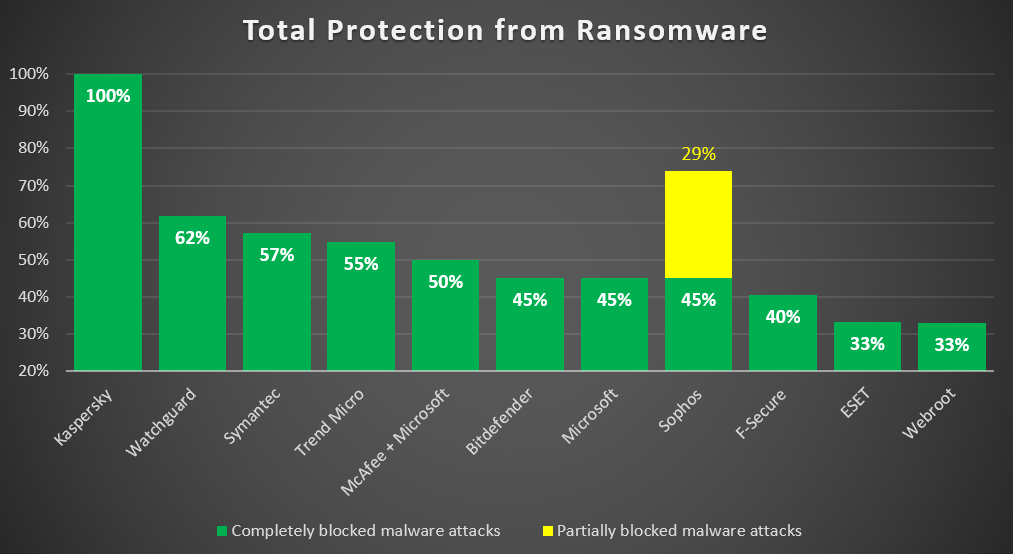
Read on…