May 2, 2017
At Last – Not All So Quiet on the Antitrust Front.
Last fall, in our domestic market we turned to the Federal Antimonopoly Service with a complaint against Microsoft regarding its anti-trust legislation violations.
Despite the long silence on the airwaves, the matter was in fact slowly but surely being addressed. And don’t pay any attention to inaccurate reports about not filing similar claims with the EU Commission: that was off the back of an interview I gave in Germany in which it looks like a fact or two went astray – perhaps lost in translation. We are definitely not planning on ‘temporarily backing off’ filing our competition complaint with the EU Commission.
And anyway, instead of reading reports it’s always better hearing it from the horse’s mouth, as they say… So here I am with real news and confirmed details and plans that I can share at the moment compromising neither ethical nor legal norms.
Ok. Let’s begin…
First off, as was expected, Microsoft disagrees with our claims. ‘We did not create conditions…’, ‘we have not infringed…’, and even: ‘we do not dominate…’ But facts are stubborn things, and despite the formal denials, Microsoft has, in fact, taken a few crucial steps toward rectifying the situation. And it looks like our actions might have helped encourage Microsoft to do so. Of course, there’s still more that needs to be done, but this is at least a good start toward ensuring that consumers have the chance to choose the best cybersecurity solution for them specifically.
It appears Microsoft took a two-pronged approach: (i) formal denials (which is logical); and (ii) specific (although small) practical steps to meet both users and independent software developers half-way.
I’ll leave out the formal denials here, but in this post I want to tell you a bit about those ‘practical steps’ that were recently taken by Microsoft. Let’s have a look at three notable examples thereof:
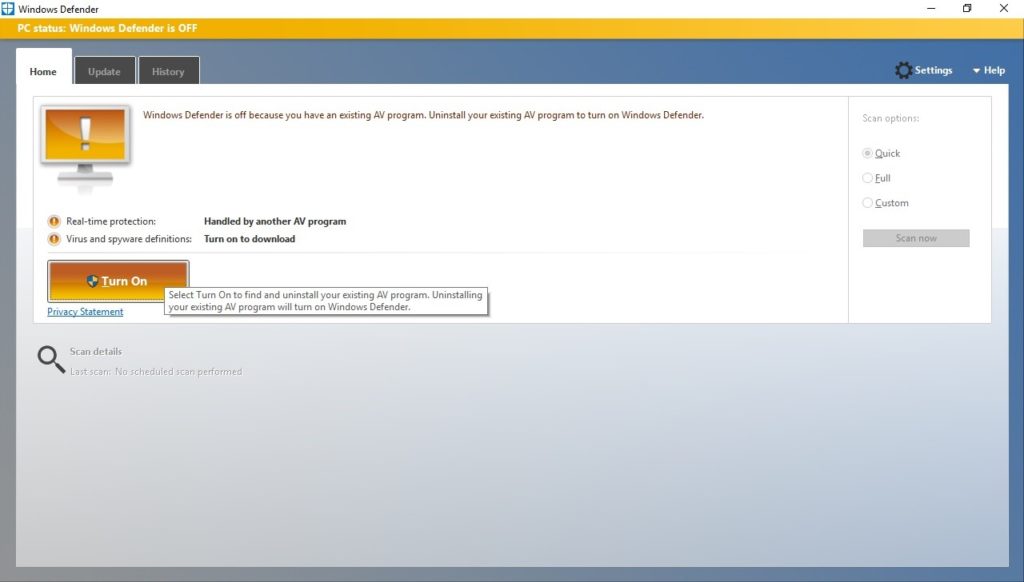
Example No. 1: The Alarming Windows Defender PC Status Page.
One of the claims we made against Microsoft regarded the misleading Windows Defender PC status page, pictured below:
The good news is that Microsoft has changed the previously displayed status page in a recent update, addressing several of the confusing and misleading elements we described.
So, what was the original status page for and what were our objections?