May 31, 2012
Monthly Archives: May 2012
May 29, 2012
Business at the Edge of the World.
Australia. A huge territory, practically completely covered with desert, with thin inhabited zones along the coast. There are some populated areas inland, but not all that many.
The population of Australia is around 22 million (the 54th largest in the world); GDP is almost a trillion US$ (18th in the world – between Iran and Taiwan); and per capita income is US$40K (19th – between Austria and Kuwait) (source: CIA World Factbook).
May 25, 2012
The Dangers of Exploits and Zero-Days, and Their Prevention.
You don’t need to hear it from me that the Internet is a really interesting phenomenon, and mega-useful for all those who use it. But at the same time its openness and uncontrollability mean that a ton of unpleasantness can also await users – not only on dubious porno/warez sites, but also completely legitimate, goody-two-shoes, butter- wouldn’t-melt-in-mouth sites. And for several years already the Internet has been a firm fixture on the list of the main sources of cyber-infections: according to our figures, in 2012 33% of users have at least once been attacked via the web.
If you dig deeper into the structure of net-based unpleasantness, you always come across three principle categories of threats: Trojans, exploits, and malicious tools. According to data from our cloud-based KSN (video, details), the break-down is as follows:
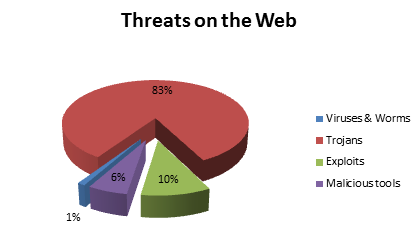
The ten-percenter in the above pie chart as you can see belongs to so-called exploits (their share will actually be greater in reality, since a lot of Trojans have a weakness for exploiting… exploits). Exploits are mostly exotic peculiarities to non-professionals – while a real headache for security specialists. Those of you more in the latter category than the former can go straight here. For the rest of you – a micro-lesson in exploits…
May 16, 2012
A 16-Hour Flight, and a Day that Never Was.
Yesterday I set myself a personal record – my longest plane journey: 8575 miles, in just under 16 hours. The route we took is the third longest in the world at the moment, but bizarrely enough it doesn’t make the top-ten longest in terms of time taken to fly. It’s probably due to the wind over the Pacific Ocean assisting the plane and saving time (and kerosene). Info on the longest air routes in the world is here.
May 11, 2012
The Bahamas: Barmy, Balmy, Not Palmy, & +1.
I’ve just added another entry to the list of countries I’ve been to – bringing my total now up to 69, or, if we include Antarctica (as an independent territory) – 70. So it’s a bit of a jubilee!
Hi all from sunny Nassau, the capital of the Bahamian Islands. Specifically, from the Atlantis resort on Paradise Island! Though I’d heard a lot about the Bahamas, and remember it in the James Bond film Thunderball, I’d never actually got round to getting myself there. Until now. Yes, today it’s me who’s in the coconut-palm, white-beach paradise.
May 6, 2012
The UK’s PR Disaster: Heathrow.
In Geneva we’d been told all sorts of horror stories about London’s Heathrow Airport recently having been turned into a nightmare of delays, huge lines and other horridness you’d normally expect from some backward banana republic, not the UK. Strange, I thought – just last week I was in England and all was OK at its main airport. Now? There’s just one word to describe it: chaos. Lines for both security and passport control were two hours long, and we hear they can get even longer. It’s so bad it resembles the hellhole that is New York’s JFK, or Moscow’s Sheremetevo about ten years back.
We were lucky – we weren’t heading for the UK. We were just connecting there. Thank goodness. Otherwise we’d have had to have joined in the fun. So here’s a warning to anyone going to the UK soon: be prepared. Make sure you’ve plenty to read, listen to, and/or watch on-the-go! I can’t imagine what’s going to happen here later this year when the Olympics start… I think getting to France first might be the best option – and coming through the Channel Tunnel!
May 5, 2012
Twice Around the World in 50 Days.
Bonjour, mes amis!
Over the next two months (a dozen days under, to be more precise), I’ll be on a non-stop ultramarathon-esque “avia-run” that’ll take me twice around the planet. In all it’ll take in around ten countries in four continents. Looking at our flight/event schedule, even I – the experienced on-the-roader that I am – got a bit overwhelmed/fearful for a few brief moments; but this quickly transformed into excitement (I’m like that) about this monster tour. I’ll be in every continent besides Africa, South America and Antarctica (the latter – the biggest shame to miss out; oh how I want to get back there!).
My route is as follows: Russia – Switzerland – Bahamas – Australia – Italy – Israel – UK – USA – China – Germany – Belgium – Russia. The airlines are already rubbing their hands with glee :) And I’m edging closer to my millionth air mile with Sky Team. I need to get there soon though, as T.T. is threatening starting using a private jet for these extended jaunts – and those miles of course wouldn’t go towards my million with the Sky Team :)
The KL guys and/or gals I go with on these lengthy forays understandably have a tough time keeping up with such intensity and tempo, so somewhere along the way I usually switch them round – kind of a support-rotation – so that it’s not too overwhelming and exhausting for them (T.T., peering over my shoulder while I’m writing this, interjects here: “and we need them alert, or not at all!!”).
The first time round the globe I’ll be doing with K.A. (who’s that? It’ll come to light soon). This is her first go at a month of constantly changing time zones, climates, airlines, hotels, and food and drink, plus impression overload. She’ll be fine. She’s a real trooper.
Right now we’re in Geneva – the our first stop on our trip. Here’s the view from the office where we had a very important meeting with some very important folks:
May 4, 2012
Beer and Broadcasts in Brussels.
Dag everyone!
In-between London and Moscow last week we managed to fit in a flying visit to Brussels, which didn’t even last a day, just 20 hours. Naturally, the first thing we did was make a beeline for the nearest bar for some Belgian beer. Oh yes – real nice. I believe Belgian beer to be one of the best in the world.
 I’ve a real talent for photography. Beers, bulldog, and… JUICE?
I’ve a real talent for photography. Beers, bulldog, and… JUICE?
Belgium is of course also famous for its chocolate, a peeing boy, and the Atomium, among other things. But on this trip all that was passed by; my schedule, as per tradition, was crammed full. Its highlight took place inside the European Commission building, where I secured myself a +1 to my list of live broadcasts I’ve been on on international TV channels. The new addition – on Euronews – now complements BBC World News, CNN, Bloomberg, Sky News, Russia Today, and a number of others.
May 3, 2012
Infosec: Interestingsec.
Infosecurity Europe, to give it its full title, is the largest European exhibition for the IT security industry. The yearly event is referred to by just about everyone as “Infosec”.
This isn’t just any old IT security exhibition, of which there are now quite a few. It’s really quite a unique one since despite the worldwide tendency for such events to be as dull as dishwater (one example of which is CeBIT). Infosec is actually very interesting and a lot of fun.
May 2, 2012
In Updates We Trust.
Remember my recent post on Application Control?
Well, after its publication I was flooded with all sorts of e-mails with comments thereon. Of particular interest were several cynical messages claiming something like, “The application control idea is sooo simple, there’s no need for any highfalutin special “Application Control” feature. It can be dealt with on-the-fly as applications are installed and updated.”
Yeah, right. The devil’s always in the details, my cynical friends! Try it on the fly – and you’ll only fail. To get application control done properly – with by far the best results – you need three things besides that “it’s easy” attitude: lots of time, lots of resources, and lots of work going into implementation of a practical solution. Let me show you why they’re needed…
On the surface, it’s true, it could seem Application Control was a cakewalk to develop. We create a domain, populate it with users, establish a policy of limited access to programs, create an MD5 database of trusted/forbidden applications, and that appears to be it. But “appears” here is exactly the right word: the first time some software updates itself (and ooohhh how software today loves to update itself often – you noticed?) the sysadmin has to write the database all over again! And only when that’s completed will the updated programs work. Can you imagine the number of angry calls and e-mails in the meantime? The number of irate bosses? And so it would continue, with every update into the future…
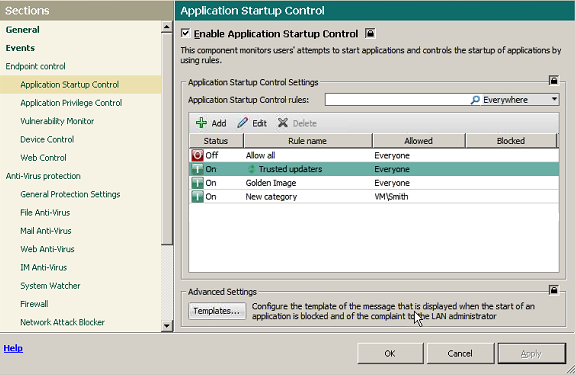
To the rescue here comes running a mostly unnoticeable but mega-useful feature of our Application Control – the Trusted Updater. It not only (1) automatically updates installed programs while simultaneously bringing the database of trusted software up to date, it also (2) keeps track of inheritances of “powers of attorney” attracted to the updating process. The former is fairly straightforward and clear, I think. The second… let me explain it a bit.
Let’s take an example. While performing an update, some software launches, let’s say, a browser (for example in order to show the user’s agreement), and transfers to it its access rights. But what happens when the update is completed? Are you twigging what I’m getting at here?… Yes – in some products the browser keeps the inherited rights until it’s restarted! So until then it could perform an action that is actually forbidden according to the security policy – for example, to download something from the Internet, and, more importantly – to run it. What’s more, the browser gets the ability to call on other programs and give them the enhanced rights of the updater. Oht-Oh!
Turns out a single update could bring down the whole security system through incorrect access rights’ management during the update process. Scariest of all is that this isn’t a bug, it’s a feature!
Anyway, back to our Trusted Updater. What it does is take full control over the update: as soon as the process has finished, it restores the rights back to what they were before the update – for the whole chain of affected programs. Another handy trick is its knowing beforehand which updaters can be trusted – there’s a special category for them in our Whitelist database. And should a sysadmin want to, he or she can add other updaters to this category with minimal effort but with a good addition to the level of the network’s overall protection from all sorts of sly backdoors.
More: The four scenarios of implementing for controlling software updates…