Fighting injustice. It’s just what we do – and keep doing. And that includes fighting major, large-scale injustice…
For example, in 2017, we managed to reach an agreement with Microsoft that encouraged it to stop giving unfair advantages to its own antivirus product. Sure, Microsoft is a modern-day Goliath. But we’re a modern-day David! And we need to be. For someone has to stand up to the giants now and again when they start throwing their weight around unfairly. Not doing so would mean users wind up with less choice.
Then last year saw us having to don the boxing gloves again for another dispute – again on an antitrust issue, but this time with another Goliath: Apple. Fast forward nearly a year – and I have two bits of news for you on this…
But first – quick rewind: some background.
Early on – halcyon daze…
Back in 2008, on the back of its extraordinary successes with its iPhones, Apple opened its App Store. And to fill out its ‘shelves’, it invited independent developers to use it as a platform to sell their for-iOS software. Those independent developers jumped right in, bringing with them thousands of apps (fast-forward 12 years and there are now literally millions). Users all over the planet were happy with all that choice, both Apple and the independent developers made tidy profits, all was well, there was peace and harmony, and it looked like everyone would live happily ever after.
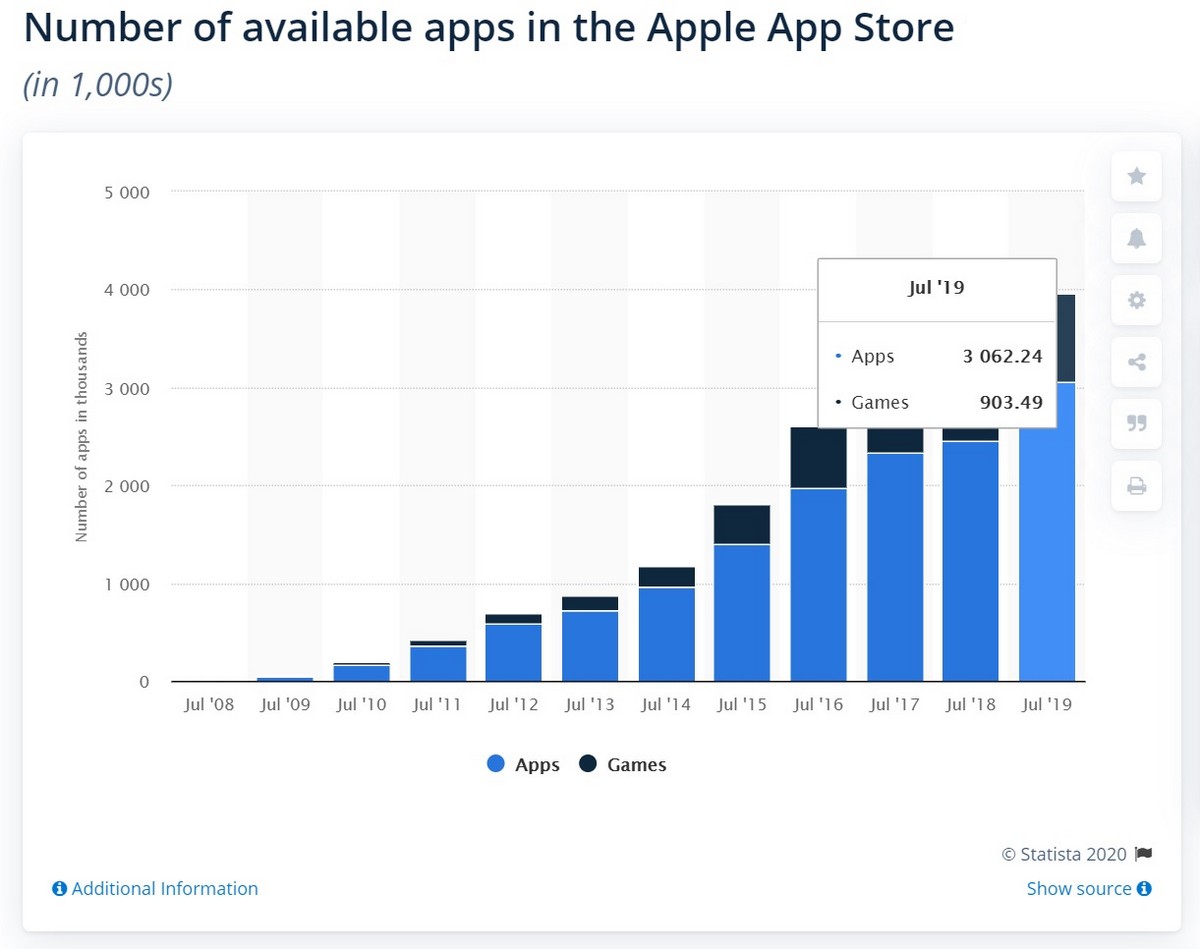
But… business is business. At the end of the day Apple exists – like all commercial companies – to make a profit first and foremost. So it started branching out a bit. It created other iThings, all sorts of services, and a lot more besides. Yet still Apple yearned for more. Which was when it turned its gaze toward the markets of iOS applications made by independent developers in its own App Store.
Fast-forward to 2020.
I have a lot of respect for Apple. The company created a successful business model that’s much envied and much imitated. I neither envy nor imitate it, and I don’t agree fully with much of its policy (first and foremost – regarding cybersecurity), but that doesn’t mean I respect it any less (even though I personally don’t use any Apple products). We’ve been cooperating with Apple many years, in various areas, and until recently this was a partnership of equals.
Like tens of thousands of other independent developers, we create useful iOS apps – apps that increase the overall attractiveness of the platform. Together with Apple we had some profitable mobile business going on, but it was the users who benefitted most (as they were supplied with ever-more useful apps). Everyone had it good. Then, at the end of 2018, Apple announced its crusade against independent developers with the release of its Screen Time.
Competition is good, because competition works for the good of the user. In this case, more apps, better apps, more varied apps – more choice (and a developer not falling asleep at the top of the App Store listings)! But for competition to exist there needs to be a level playing field, i.e., fair rules. For everyone. Yet that level playing field – and competition with it – has been destroyed by Apple. Let me tell you how.
iStory that’s hard to believe.
Screen Time entered a mature market in which dozens of independent developers already operated. The App Store offered a great many apps providing parental controls, time management and other related tasks. And it’s here where the craziness begins.
Apple unexpectedly monopolized a wide range of critical functions, by simply turning them off for other developers!
So, like, how, for example, is a parental control app supposed to get by without configurable profiles, the ability to filter URL addresses, application control, and full fledged geolocation? That’s right: it can’t! But it can if it’s an Apple parental control app – for none of this critical functionality was limited in any of its own apps! It’s one rule for Apple’s apps, another for all the rest.
Now, of course, this audaciously odd-ball move was made under a smokescreen of ‘concerns’ about security and privacy; however (also ‘of course’) – these concerns were seen right through real quick to reveal their bogusness.
Next, Apple started banning developers from the App Store, delaying approval of new software builds, and rolling out new unacceptable requirements and conditions. Some apps were shut down, while others had their functionality restricted – rendering them useless. But some independent developers decided to fight back. Including us. Developers came together to form an association with the aim of working with Apple to try and secure fair rules for all, while some filed complaints with regional antitrust authorities and began a public campaign in the press and on social media.
Then, in June 2019, Apple looked like it had hit the brakes and even gone into reverse. However, actually, it was purely a tactical maneuver to feign an expression of goodwill, and which in no way helped solve the problem of equal rights for all – including Apple itself.
Then it released iOS 13… – with yet further restrictions to hit the ecosystem even harder!
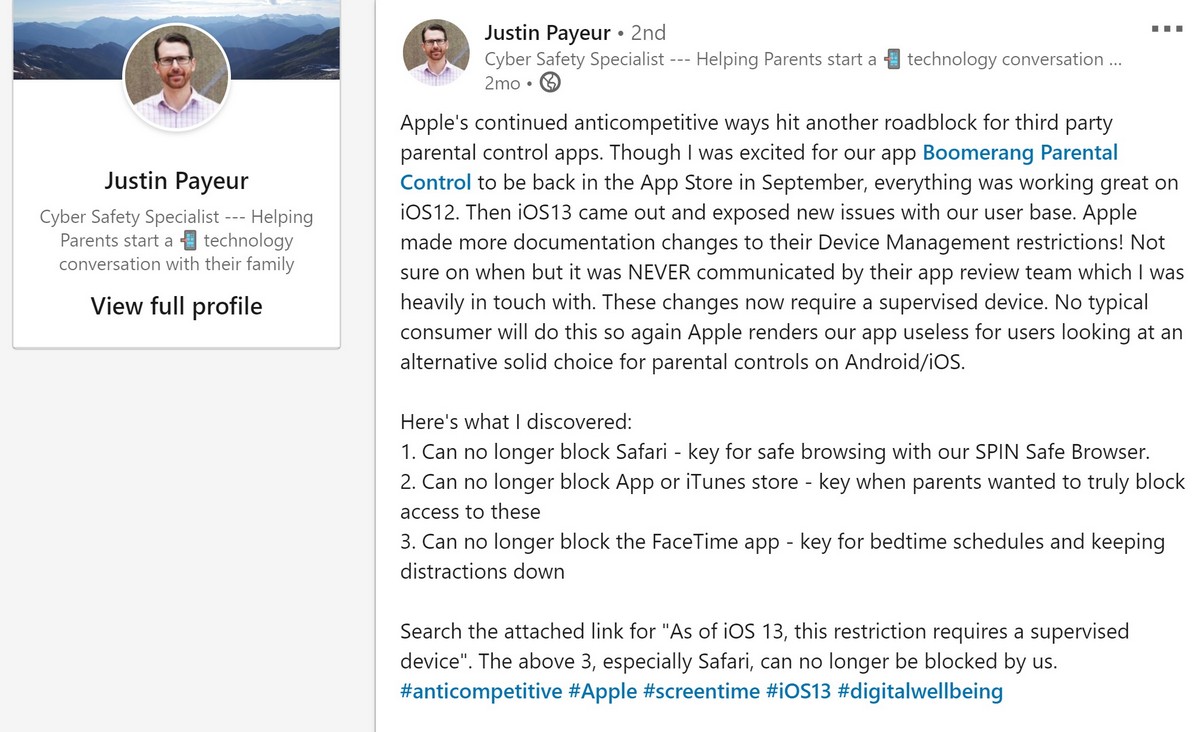
Let me give you an example of how the ‘innovations’ of iOS reflected on our parental control app Kaspersky Safe Kids.
First, Apple loads and activates Screen Time automatically on devices upon installation of the new version of the iOS – even if the user already has onboard a similar application. Don’t know about you, folks, but that, to me, doesn’t have much of a ring of ‘free competition’ to it. Looks more like just the opposite: with a ring of intrusion, aka thrusting, aka foisting, aka gatecrashing the party, i.e. – uninvited.
Second, new features on iOS 13 now permit a child to easily delete Safe Kids (i.e., a complete cancelling out of the very meaning of ‘parental control’), and also view websites via Safari (it has become impossible to hide it) instead of via the built-in safe browser that permits filtration of undesirable content. No, really folks!
Third, changes to the policy of accessing the geolocation of a device have taken away parents’ ability to track their child’s location! (No. I am not making this up. And all in the name of security – remember?!)

But wait – here’s what really takes the proverbial biscuit. Are you sitting down?…
All features that have become forbidden to independent developers remain completely ok and wholesome and accessible to… – ta-daa – Apple!
iAudaciousness on this scale simply couldn’t go unnoticed.
Encouragingly, the issue hasn’t gone unnoticed. It’s been resonating at the very highest legislative levels around the world. In the U.S. Senate it was suggested to forbid Apple and other large companies from placing their own apps in their own marketplaces, since they, by default, will create preferences for their own products.
In Russia antitrust proceedings have been initiated. In the EU they’re still at the pre-investigation phase. Indeed, slowly but surely the negative consequences of this lowering of competition are coming to the surface. Even from the user side – Screen Time is taking a lot of flak for its functionality shortcomings (even with its functional superiority given that its competitors have all had their functionality curtailed!). Some independent developers see the only way of getting round the issue to be to urge users to move over to Android if they want to keep their kids safe.
And now for that news I said I’d be telling you…
I’m not sure yet if it’s good news or not, but at least some movement must be a good thing – and we’ve been trying to fight for equal opportunities for everyone. This spring, the Federal Antimonopoly Service of Russia will deliver its verdict on our claim regarding the abuse by Apple of its dominant position and the creation of unlawful competitive advantages for Screen Time. Almost all arguments and evidence in the proceedings have already been given and submitted. For us it’s been a very long, complex process (details – here), which has taken up much time, effort and money energy. But we’ve explained our position well, and I have Hope that the decision will be in our favor. Fingers crossed…
When Jobs was in charge – there was nothing like this.
Do you know what this crusade of Apple’s against independent developers gets me thinking about? A fight of the iOS ecosystem against the App Store ecosystem! The former gradually absorbs the juiciest, most profitable markets of the latter. And it looks all the more unsavory given that it is thanks to the App Store that the iOS platform has risen to now make up the basis of the business of the company. Without it, Apple would have had just another failed project – the kind of which there have been many in the history of the IT business.
It all reminds me a little of the infamous letter of Steve Jobs that announced the ‘holy war‘ against Google; in particular one sentence within it: ‘Tie all our products together, so we further lock customers into our ecosystem’.
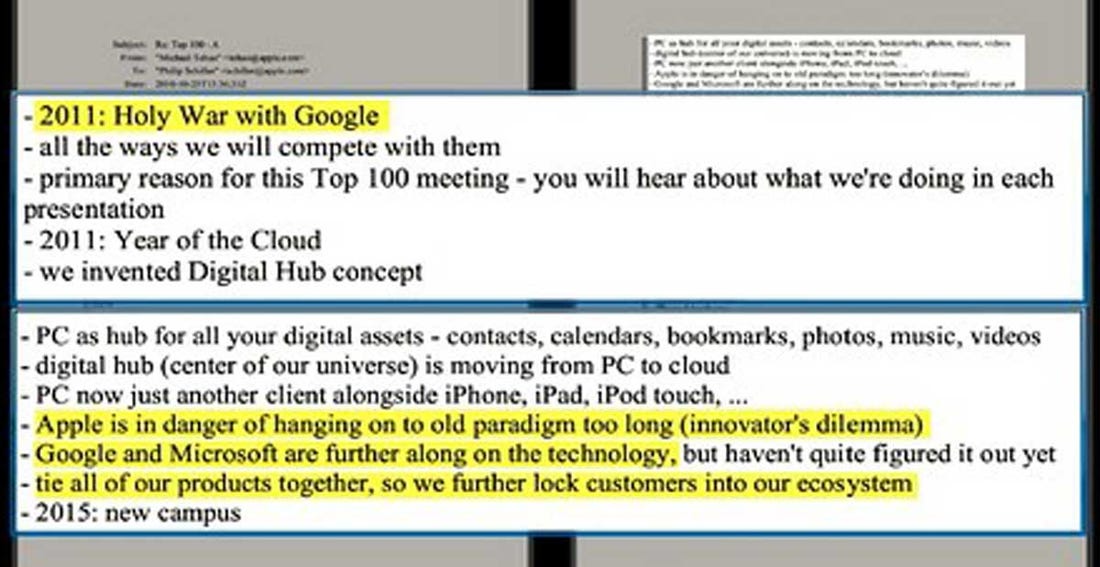
Probably only Mr. Jobs himself knows exactly what he meant by that. But though he was originally against third-party apps for the iPhone (he later changed his mind), I’ve no doubt whatsoever that among his greatest expectations were those he vested in independent developers: to have their inspiration and resources help create for Apple the best ecosystem. And one thing’s for sure, Jobs wouldn’t have allowed Apple to transform itself into a self-important dictator and turn on the very developers that helped it and subject them to out-and-out discrimination.
I’ve already said this above, but I’ll say it again: I respect Apple. And I have a feeling that there are no issues in our relations we can’t resolve. Apple could opt for a sensible compromise and reconsider the unfair rules of the game. This would make its platform even stronger by permitting independent developers to supply to it full-fledged apps so as to serve the needs of its millions of users optimally.
Finally, please support us in this struggle to secure your right to choose exactly what you want, not what one large corporation decides is best for you. And stay tuned. I’ll be back with news re the FAS’s verdict once it arrives…