May 29, 2020
The world’s cyber-pulse during the pandemic.
Among the most common questions I get asked during these tough times is how the cyber-epidemiological situation has changed. How has cybersecurity been affected in general by the mass move over to remote working (or not working, for the unlucky ones, but also sat at home all the time). And, more specifically, what new cunning tricks have the cyber-swine been coming up with, and what should folks do to stay protected from them?
Accordingly, let me summarize it all in this here blogpost…
As always, criminals – including cybercriminals – closely monitor and then adapt to changing conditions so as to maximize their criminal income. So when most of the world suddenly switches to practically a full-on stay-at-home regime (home working, home entertainment, home shopping, home social interaction, home everything, etc.!), the cybercriminal switches his/her tactics in response.
Now, for cybercriminals, the main thing they’ve been taking notice of is that most everyone while in lockdown has greatly increased the time they spend on the internet. This means a larger general ‘attack surface’ for their criminal deeds.
In particular, many of the folks now working from home, alas, aren’t provided with quality, reliable cyber-protection by their employers. This means there are now more opportunities for cybercriminals hacking into the corporate networks the employees are hooked up to, leading to potentially very rich criminal pickings for the bad guys.
So, of course, the bad guys are going after these rich pickings. We see this evidenced by the sharp increase in brute-force attacks on database servers and RDP (technology that allows, say, an employee, to get full access to their work computer – its files, desktop, everything – remotely, e.g., from home) ->
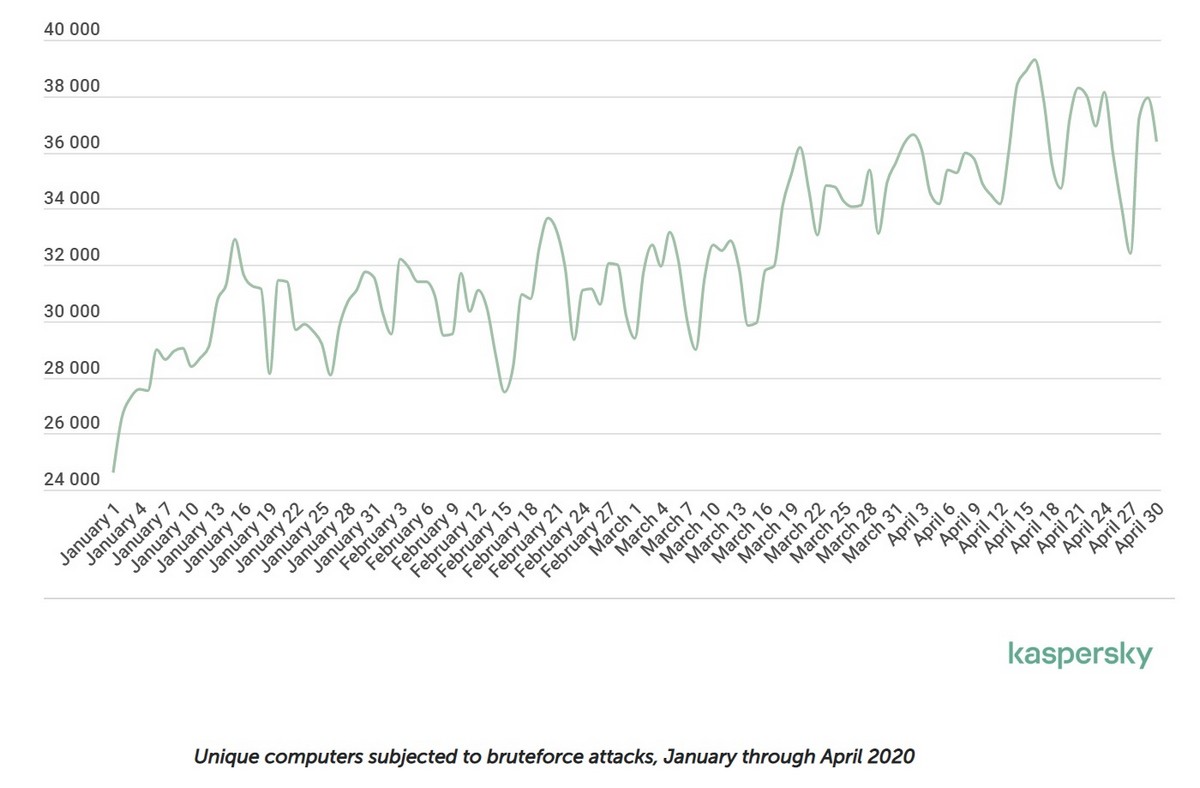
Brute-forced password combinations are used to break-and-enter corporate networks so that, for example, they can inject ransomware (most commonly Crusis, Cryakl, and Phobos malware) into them. From the beginning of the year the average daily number of unique users attacked with this technique being used increased by 23%. But if we look at the picture in absolute numbers we can see that the attacks have sky-rocketed, and such sudden increases were uniform practically across the whole world.
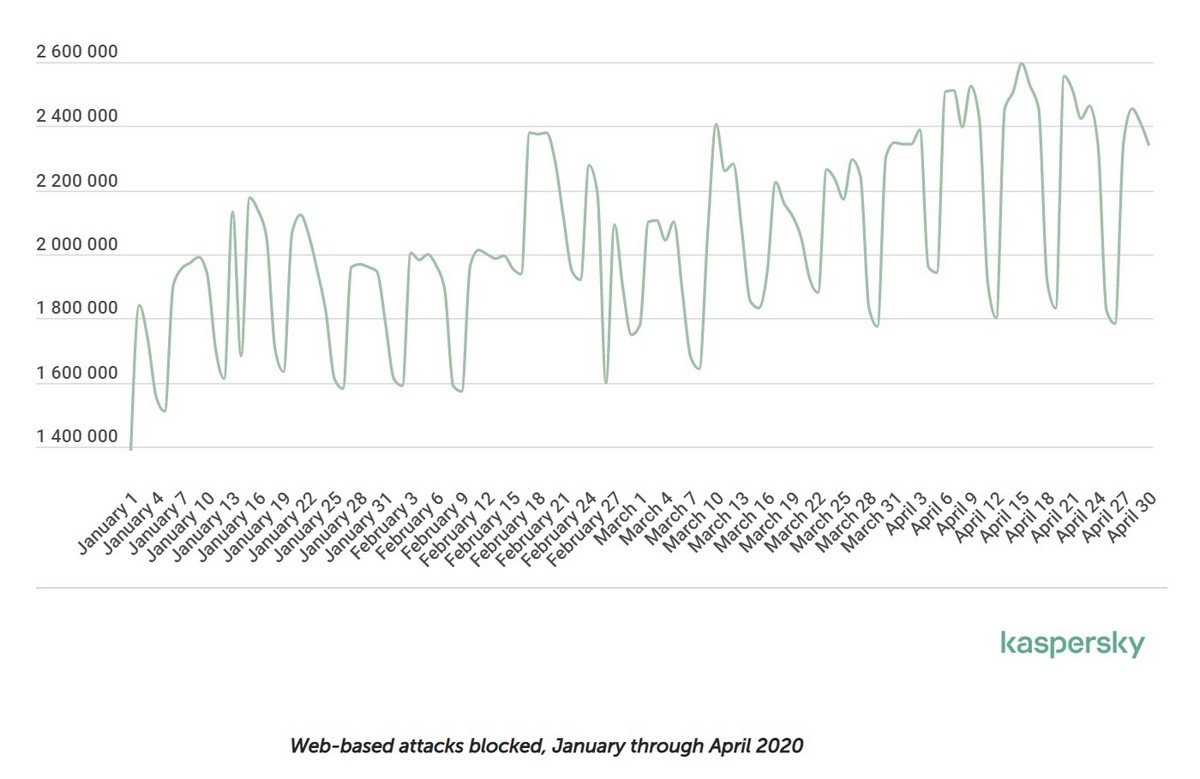
Another statistic highlighting this trend is the increase in the number of web-threats: up 25% in four months. And this has been fairly uniform across all categories. But perhaps the most curious/unusual of all has been the sharp rise in (i) the number of modifications of browser scripts that are attached to poorly-protected websites and that send the bad guys bank card details; and (ii) cookie stuffing attacks (hidden installation of cookie files having nothing to do with a visited site).
And finally, there’s been a rise, albeit it not a sharp one, of average daily triggerings of file antivirus (+8% since the beginning of the year). Malware scripts are mostly to blame for this (.js, .vbs) together with malicious shortcuts (they allow to quickly develop new malware by simply wrapping a PowerShell command string in a shortcut). Oh, and here’s an unexpected blast from the past: the reincarnation of the rather old polymorphic virus (oh yes!) Sality! Our products are detecting around 50,000 unique files infected by it every day.
But wait! There’s already been something similar: in February we clocked infections by an actual ‘virus’ – KBOT (yes, the nasty parasite-virus that injects malicious code into executable files: the first ‘living’ computer virus we’ve spotted in the wild for years). But we think it’s a bit too early to say if there’ll be a return to the era of viruses. Quantities of this type of ‘old-school’ malware are still negligible in the overall flow we see daily.
Overall, the increase in the share of new malware (out of all malware) in April was by 7.9%. Let me remind you that daily (!) we catch and add to our database more than 340,000 new (!) instances of malware! And in April that was up nearly 10%.
What’s curious is that in the first two weeks of May almost all the listed badness increases we’ve been detecting actually fell: average file antivirus triggering – -7.2%; web antivirus – -5.27%; and new malware – -31%. The only things on the up were brute-force attacks on database servers and RDP (+0.27%). I wonder why? The sun was out over the May holidays so the cyberscum took a few days off?! Let’s see if the trend continues for the rest of the month…
Summary
The cyber-epidemiological situation is following the expected route, and everything is under control here at K and on our users’ computers and devices and servers and networks.
All the same – I suggest everyone follows the main rule of cybersecurity – maintain cyber-hygiene! :) Most importantly – don’t click something that is being begged to be clicked (washing hands with soap after doing so won’t help); don’t install or launch this, that, and the other; use a VPN Service; use two-factor authentication, and always – including while working at home remotely – use good cyber-protection. And for how to work remotely not only safely but effectively – check out the tag on our blog.


