February 27, 2012
Halt! Who Goes There? Or Remedy #3.
Security people, sysadmins and, generally, all those who by virtue of their employment take loving care of corporate networks – all these people have plenty of headaches. Indeed, a veritable cornucopia of headaches. And, of course, the main source of trouble is… you guessed it, users. Tens, hundreds, even thousands of users (depending on your good fortune) who have problems 24/7. As for us, we try to help these ‘frontline soldiers’ get to grips with their headaches, using the full extent of our resources in our field of competence. Below, we discuss one very helpful remedy that fits this combat strategy to perfection.
There are, in fact, three separate remedies. But they all tackle one problem – keeping users under control. And there are helpful side effects – enforcing a centralized IT security policy, fool-proofing, and automating the ‘donkey work’. That’s right, I’m talking of three new features included in the new version of our corporate solution, Endpoint Security 8: application control, device control and web control. This post is about application control (or simply AC without the DC).
Most of the time it’s a struggle to keep computers clean. Users are given to downloading questionable “cool warez”, installing them, trying them out and forgetting all about them. As a result, in half a year the computer normally turns into an unmanageable software zoo, becoming unbelievably error-prone and slow. And, of course, the abovementioned “cool warez” can easily be virus-ridden, pirated, or at best counterproductive.
There are different ways of getting out of this predicament. Some companies wag their finger at users and strictly forbid them to install software on their computers (without actually enforcing a ban). Others simply make installing software impossible in one way or another. AC is, in fact, an elegant compromise between the two.
So how does it work?
Our AС has three main features:
- Restricting application startup
- Managing application privileges
- Checking applications for vulnerabilities
They are all shown in the “scary” diagram below:
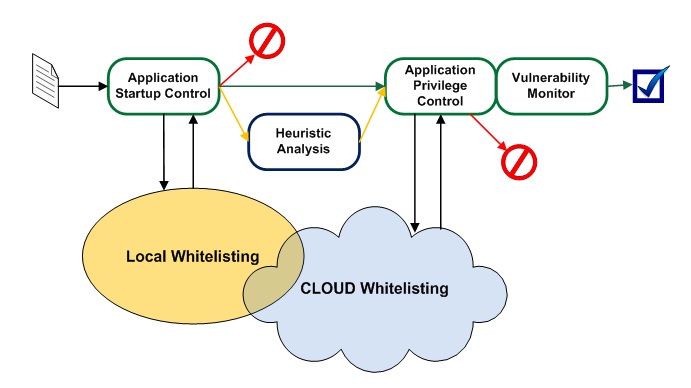
There’s nothing that scary about the diagram, of course… except maybe at first glance if you are not used to this sort of thing.
In practice, application control looks like this.
First, the sysadmin sets the rules for specific programs and program categories – what can be run, what can’t, and what to do with the rest (so-called “gray” software). You can set one rule for all, or apply different restrictions to different user groups. By the way, ‘out-of-the-box’ integration with Active Directory comes in handy in the latter case. There are also ready-made Default Allow (allow everything, block only what’s specified by admin) and Default Deny (block everything, allow only what’s specified by admin) scenarios. From experience, the latter is particularly popular.
To make creating rules easier, we have a complete cloud-based whitelisting database, which includes categorized information on 300+ million scanned and safe files (with around a million files added daily). According to a recent test, the database covers 94% of all corporate software. Indeed, why waste time finding out which games employees are playing? It’s much easier to ban the entire Games category. Even if they find some exotic game which isn’t already in the database, it can easily be added manually.
There’s one more interesting option – an automatic inventory of the software installed. Yup, that’s another magic button for you. A very popular feature, too, saving sysadmins loads of time and allowing them to make electrifying discoveries about villains, creeps and even rats :).
Once the software has been included in the inventory and categorized and the launching rules have been created, it’s time for a test run. This is called “rule testing mode”. By comparing rules with software inventory results, the system comes up with a report on what software will get messed up and who is likely to be making angry calls.
After this, the rules are centrally uploaded to all the protected computers on the network. As soon as a user tries to run some software, our product installed on the computer matches it against the database and follows a predefined rule.
It gets even more interesting than that though, for application startup control is by no means all our AC is capable of!
First, application privilege control can be used to define the range of allowed actions for each application and for application categories. For example, it’s possible to block all attempts to establish an Internet connection for all software except officially allowed browsers and email clients; or block access to internal databases – client databases, partner databases, warehouse databases – for all software except dedicated programs that require such access.
Second, AC includes a yummy feature called Vulnerability Scan. Scanning is performed both on-the-fly, when launching an application, and when routinely creating an inventory. If “gaps” are detected, a sysadmin can block the software or install a patch. We get information on vulnerabilities from three sources: from our partners Secunia and Microsoft, plus from our own research. Vulnerability data is downloaded with other database updates.
Now, let’s have another look at that “scary” diagram.
You launch a program. The system checks its category. If it is on the blacklist (forbidden) then it is blocked from running. If the program is on the whitelist (allowed) the system proceeds to the next check. If the “gray list” is triggered (no data), additional heuristic analysis is performed and a decision is made based on its results. In the next step, the system monitors the program’s activity, and the program’s feature is blocked if it violates any ban. Then comes the last test – the vulnerability scan. Again, depending on the settings, the program can be blocked, “covered” with additional protection, or simply allowed to run. Bingo! No magic, just good old business logic being put to use.
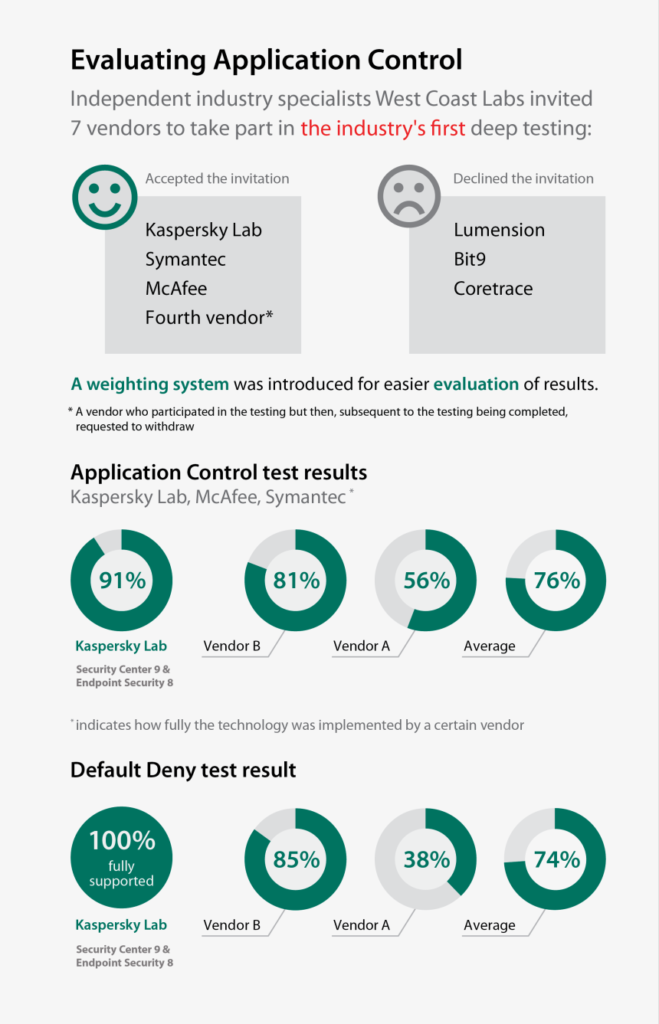
Application control is not really anything new, but it has only just started to appear in comprehensive all-in-one security solutions. Therefore, it makes sense that we don’t know much about the feature’s effectiveness yet. So far vendors have just been putting on airs about how cool their version of the feature is. But a few days ago, the results of the world’s first comparative test of this technology – carried out by West Coast Labs – were published:
[There are heaps more interesting infographics here]
// Yep, looks like the “Fourth vendor” was scared to death with their results.
I don’t think any commentary is necessary here. It looks like we are the only ones who are really investing in technology development, although everybody just loves to yell about it. In other words – three cheers for our R&D, product marketing and, most of all, whitelist lab!
Keep up the good work, guys!