December 8, 2011
Features You’d Normally Never Hear About – Part Three.
And so I continue with series on some of the lesser-known, fruitiest features to be found in our products. This time I’ll be concentrating on whitelisting – a completely different approach to malware protection, which at the moment is included in KIS, PURE, and the new generation of our corporate products.
So why did I choose this seemingly techie term that could frighten off a respectable non-overly-techie reader from the very beginning?
The answer is quite simple: in a way whitelisting is pretty much revolutionary for the industry – based on a totally new paradigm, which goes far beyond traditional pattern-based technology. As a result this a great opportunity for the anti-malware industry to be one step ahead in the battle with cyber-criminals, and for you – to be better protected against unknown threats. And in fact whitelisting is not that techie – see for yourself below!
So, what is whitelisting?
A list written in correction fluid? Such a thing may exist, erm, I guess. But no, KL’s whitelisting is something a little different.
The idea itself is actually not all that new, so I don’t know why Wikipedia refers to it as “emerging”. However, it is true that most anti-malware vendors have for some reason still not managed to implement it in their products. Oh well – live and let live; it’s up to them how good the protection they provide is, I guess. But I personally firmly believe that the industry should be more innovative to cope with the constantly increasing malicious activity. And whitelisting is something that really spearheads the battle against malware.
Anyway, the idea goes something like this.
Unlike with the traditional pattern method, which tries to find the bad things on your computer, whitelisting isn’t bothered about baddies at all; all it wants to do is to get to know and become friends with the goodies, i.e., safe files.
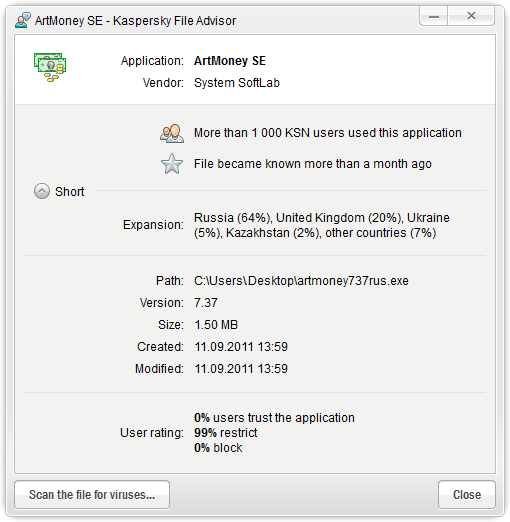
How can we be sure files are safe? Well, we test them all in our whitelist program and give them our seal of approval. And we’ve been pretty busy – there are presently in the database more than 300 million tested files.
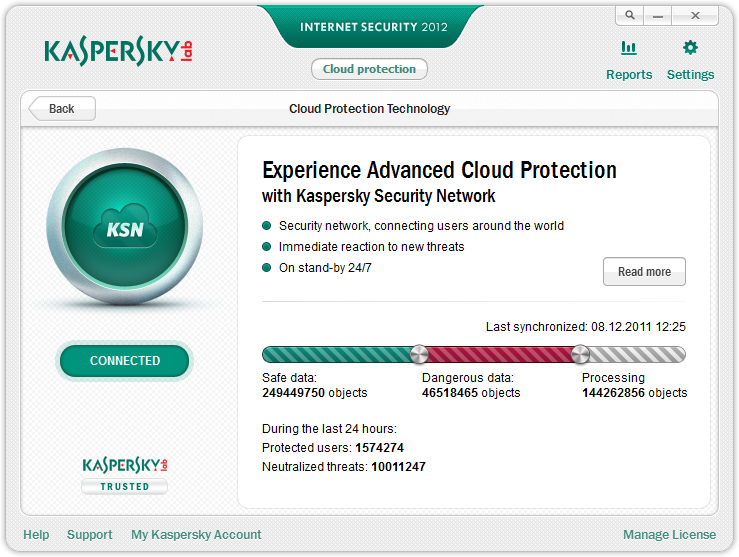
Depending on the settings, files that are not present in the whitelist directory can be automatically blocked (a very useful feature for the corporate environment), or flagged as suspicious and sent for additional checks by anti-virus components. Even if a check doesn’t return a positive result the files can be launched in the Safe Run isolated environment to provide extra protection against unknown malware. Alternatively you can right-click a file to get info on its reputation in our cloud-based KSN service (video, details); and this service is used quite a lot – it receives 400,000 file-checking requests per second!
So what’s all this for, you might ask, and why is it better than the traditional approach?
Well, protection of a computer with the pattern method means that we need to know about all the baddies. But these days we detect around 70,000 malware samples every day, and what it’s going to be like in years to come is anyone’s guess; but one thing’s for sure – it’s not going to get better. Besides, every instance of malware needs to be analyzed and entered into a database.
Of course, we’ve made great strides in terms of reaction times: thanks to KSN and the automation of the “conveyer” the average time between learning about new malware and releasing an update is just 40 seconds. But this is still 40 seconds too long; ok, maybe 39 seconds too long if I’m more realistic. Indeed, it represents a small but unpleasant nuance we are trying to improve.
Anyway – back to whitelisting: as mentioned, it couldn’t care less what the baddies look like. It just knows what is guaranteed to be clean. The baddies for once – at least with this particular feature – are given an easy time.
So whitelisting doesn’t really participate in the ongoing ‘arms race’ with malware. Instead, it kind of runs alongside doing its own thing. With cyber criminals releasing new malware all the time, users have at hand a file reputation service, which reliably informs what can be run with no worries, and what it might be better not to run.
And there’s another bonus from having this tag-along-er: whitelisting increases the performance of the anti-virus, since it doesn’t need to check files that are on the whitelist – they’ve already been checked. Among IT security professionals this approach is called “Default Deny” – first prohibit everything, then allow only the safe stuff. Very simple and it works perfectly!
We recently did some research and found that among home users whitelisting, alas, is not much known about. But it’s still early days yet. However, in large organizations whitelisting will very soon become one of the main supporting buttresses of corporate security policy.
For companies it’s simpler and safer to standardize the selection of software used, and for the rest to be either prohibited or to be flexibly controllable. An example would be to allow public instant messengers to be used only by senior managers, with the rest having to make do with just strictly business applications – not that I’d allow such bourgeois tendencies to creep in myself! After all, I find Skype a great way of communicating with colleagues – faster and more convenient than a phone call, so everyone in the company will benefit from instant messaging in their work too.
In the recently released Endpoint Protection 8 and Security Center 9 all the advantages of whitelisting and centralized management, categorization, rules, group policies, and, of course, control over application usage, is featured. You may then wonder why we need malware patterns at all – why not move over completely to whitelisting and be better off for it? This is a very good question. But to cut a long story short…
First, the whitelist doesn’t cover the full diversity of software. And sometimes we all need the flexibility to be able to run something unknown (incidentally, users can maintain their custom whitelists by adding specific software to the list of trusted applications). However, in these cases it’s a good idea to scan files with other technologies, and, just to be on the safe side, to have a look at how they behave with System Watcher. Second, to delete malware we still rely on good old patterns. Third, concerning protection, one should never rely on just one technology – that would be like a one-handed boxer.
As I’ve said many times before:
Protection needs to be multi-layered, and every layer needs to supplement and secure the others, providing maximum protection, productivity and convenience, regardless of the environment.
Put another way, you shouldn’t put all your eggs into one basket.
And finally, here’s a video with a popular explanation of the advantages of whitelisting:
More details about whitelisting you can find here.