March 14, 2014
Kentucky Fraud Kickin’.
The Internet and mobile devices and related gadgetry have brought so much incredibly useful stuff into our lives that sometimes it’s hard to imagine how on earth anyone managed without it before. You know, purchasing airline tickets and checking in, online shopping and banking, multi-device data sharing, keeping the kids occupied on the backseat of the car with a film on their tablets (in my youth you just sat there or played I Spy). But I digress, and so early on in this post…
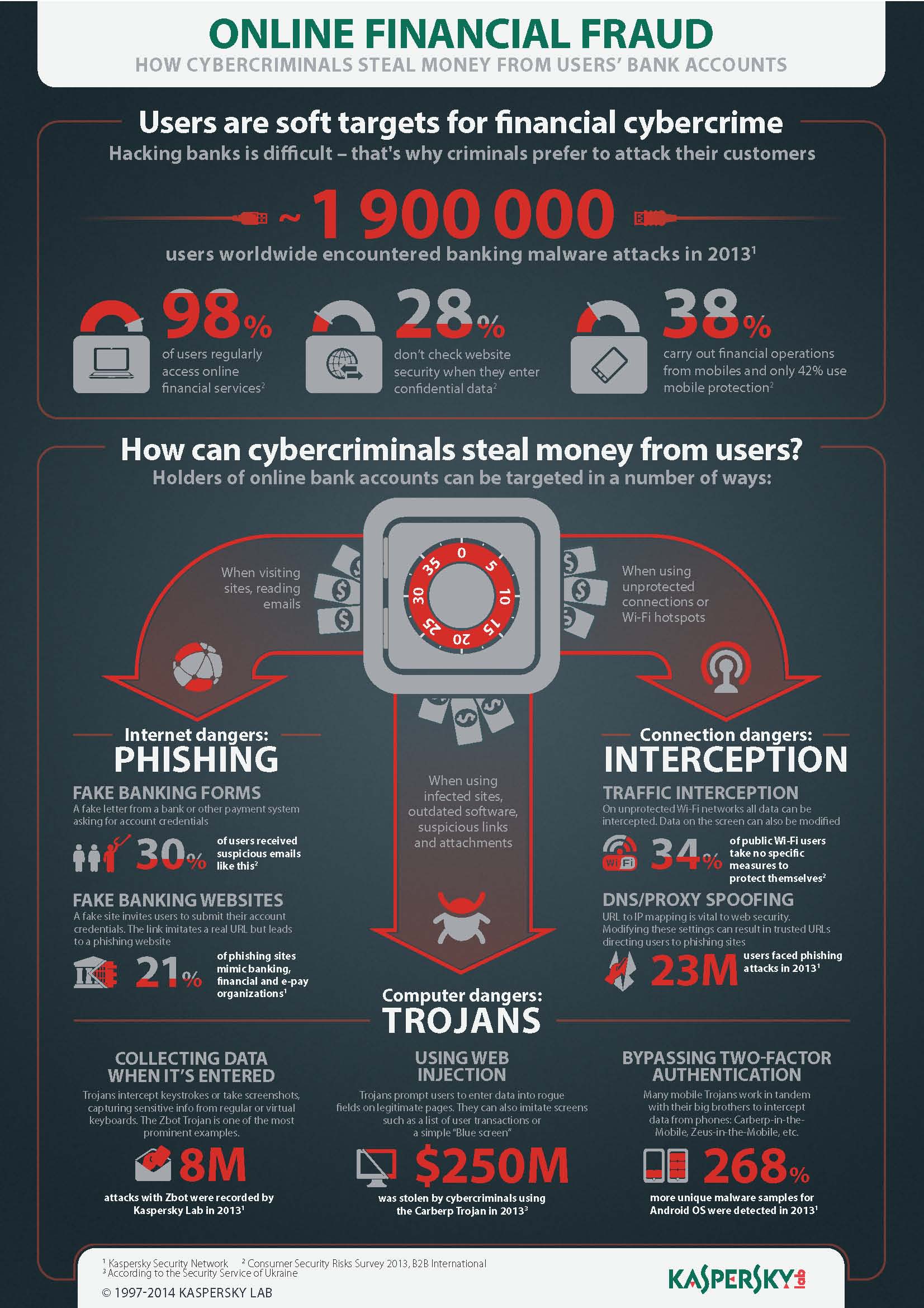
Alas, along with all the good and helpful stuff to make life easier, the Internet’s brought us other stuff – bad stuff that’s harmful and dangerous. Malware, spam, hard-to-trace cybercrims, cyberweapons, etc., etc. There’s also Internet fraud, which is what I’ll be writing about in this post, or – more to the point – how to combat it.
But let’s start with the basics: who suffers from Internet fraud?
Consumers? Well, yes, but not much compared with businesses: the brunt of the cost of online fraud is taken by banks, retailers, and in fact any online operators.
A few figures to illustrate the scope of Internet fraud:
- In 2012 in the United States alone, direct losses from online fraud came to $ 3.5 billion;
- Those losses were made up of about 24 million fraudulent online orders;
- Almost 70 million orders were cancelled due to suspicion of foul play.
All rather alarming.
In the meantime, are online operators generally taking any measures against fraud?
Of course they are. Plenty!