September 12, 2013
K-LOVE & KISSES 2014 – PART 1.
Hip, hip, hurray! Yee ha! Woo hoo! The latest incarnation of KIS has landed – everywhere (almost)!
As per our long held tradition of launching new kit during the summer months – we’ve now managed to get KIS 2014 officially released in all the main regions of the world and in all the most widely spoken languages. For those interested in KIS itself, go here to download the new version. Upgrade guidelines are here.
And as is also becoming a bit of a tradition early fall, the time has come for me to tell you all what’s in this here new version…
First thing I can say: new stuff – there’s plenty of it. So much so that there’ll be several posts covering the key new features separately, as the low-down on all of them won’t fit into one bite-sized blogpost that won’t send you to sleep…
So, here we go… with post No. 1:
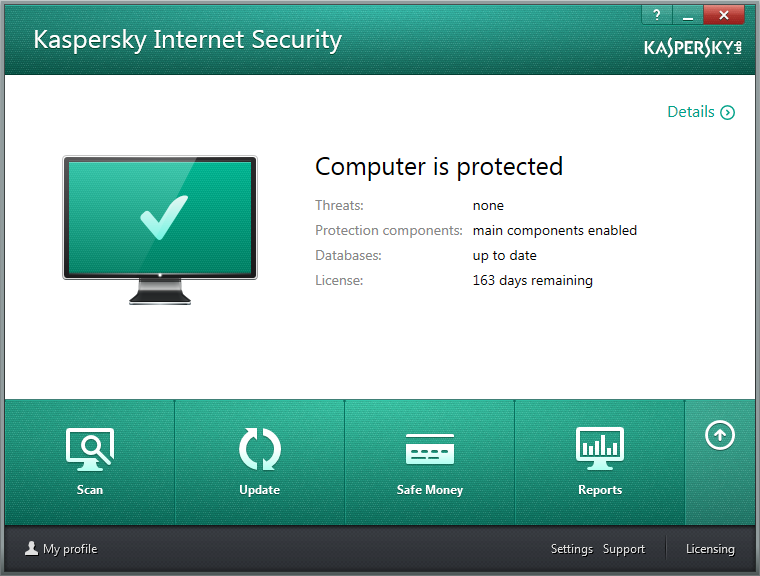
Basically, KIS 2014 packs yet more punch than its already punchy predecessor – KIS 2013 – which even without all this year’s additions was unlucky for no one. The protection provided is harder, better, faster, stronger. KIS has gone under the knife for a nip and tuck complete face-lift of its interface, and the logic of its main operations has been overhauled too.
There are new features to ensure secure online money operations (we’ve beefed up Safe Money); there are new features in Parental Control; there’s integrated protection against malicious blockers; and there are various new performance accelerators and optimizers to make the protection even more invisible and unobtrusive.
But the best feature of all in this version is what we put most effort into: providing protection from future threats, having added to the product – much to the chagrin of cyberswine – several specialized avant-garde technologies (none of which appears to be included in competitors’ products). No, we haven’t used a time machine; nor did we track down cyberpigs and do a Jack Bauer interrogation on them to get to know about their planned mischief. We shamanized, looked into the future, came up with rough calculations of the logic of the development of cyber-maliciousness, and transferred that logic into practice in our new technologies of preventative protection.
Among the preventative measures against future threats I’d like to emphasize the souped-up Automatic Exploit Prevention – two special technologies from our corporate solutions that have been adapted for our home products – ZETA Shield and Trusted Applications mode, plus a built-in proactive anti-blocker.
So how do all these fancy sounding features actually help in daily computer hygiene? Let me start by telling you first about Trusted Applications mode – the world’s first for such technology being featured in a home product providing complex security.
The typical modern-day comp that’s just been bought – it’s a bit like, er, the parcel in ‘pass the parcel’. Everyone has a go. Dad, mom, then maybe grandma and granddad, then the kids, and maybe also occasionally relatives and friends have a fiddle. And each and every one of them might install what he/she wants, visits the sites he/she likes, changes system settings, uses different messengers, and so on… And often this game of pass-the-parcel-comp takes place in one user profile – and without elementary protection.
So what do we get? You guessed it, a toxic brew of insanitariness. After just a few days of multiple users not observing basic comp hygiene, said comp turns into a hotbed of malignancy representing a threat to the users, the Internet, and society in general.
Now, of course, protection should have been there in the first place in the above example; but in the real world, often it just isn’t. And that’s why we’ve added Trusted Applications mode – to help cure such badly infected comps.
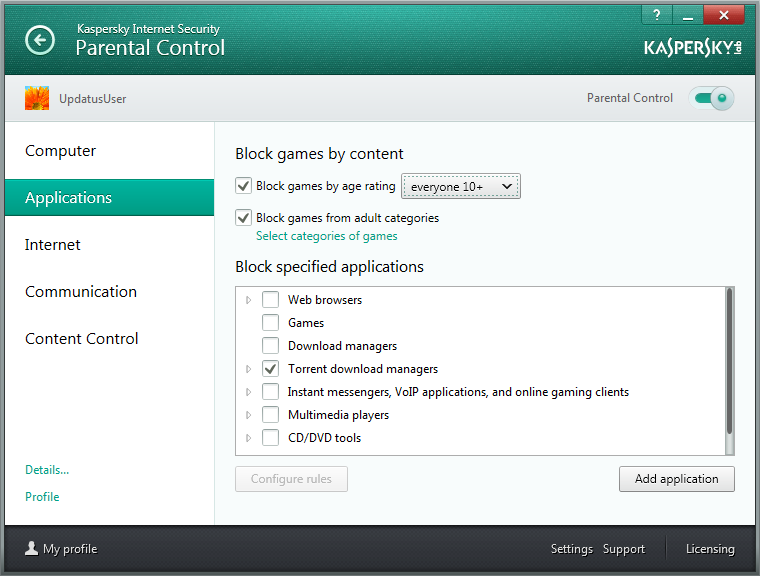
The idea of the technology is straightforward – to be able to control which programs can be launched, and which can’t. And this is put into practice as per the principle of ‘deny everything that’s not allowed’, AKA Default Deny.
The head of the family, who acts as the comp’s admin, has to decide on a list of allowed programs, with all the rest getting automatically blocked. And that really does mean everything – which of course will include any new bit of malware, unwanted toolbars and so on. Thus, the technology doesn’t get into the nitty-gritty of the antivirus realm, i.e., detecting malware and other undesirables; instead, it just ‘knows’ a few ‘good guys’ who are always on the guest list and always allowed entry to the club (comp), with the rest permanently on the black list – barred from entry, until the bouncer (admin) decides to personally give them a free-entry pass.
Trusted Applications mode complements all the other security features in KIS to strengthen the overall level of protection.
One example of this is how Trusted Applications mode interacts with Parental Control. This feature provides parents with a pleasant and much-needed feeling of security of protecting their offspring from adult content and general Internet overdosing. Of course, the likelihood will remain that children with their insatiable curiosity will nevertheless still sometimes come across some kind of bad file or infect the system via an ostensibly ‘correct content’ site; and besides, there’s always the chance that malware can come from 100% proper and decent sites too – should they be hacked and infected themselves. However, with Trusted Applications mode switched on the comp stays maximally Fort Knoxed against all the kids’ (and adults’!) (and the Internet’s!) shenanigans.
Trusted Applications mode has been transferred over to KIS 2014 from our corporate solutions (and not the other way round as normally occurs), where it’s been doing its stuff for two years already. In that time it’s come to be a real popular feature due to its common-sensical usefulness.
However, in its corporate incarnation it’s not all that suitable for home users. In home products you need lots of flexibility, and it needs to be smart enough not to pose too many annoying questions, to allow for typical home software environments and habits, and to operate as automatically and as quickly as possible, while at the same time providing the same level of protection as it’s chunkier corporate cousin. In short – secure and convenient.
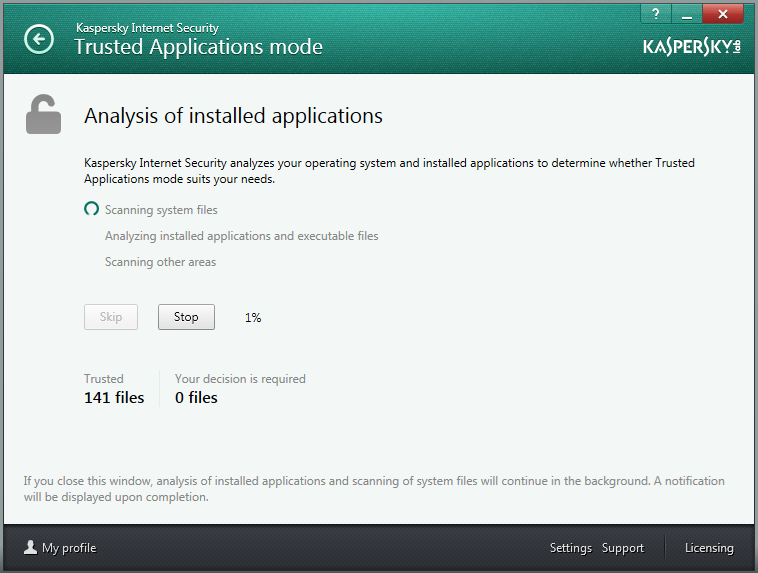
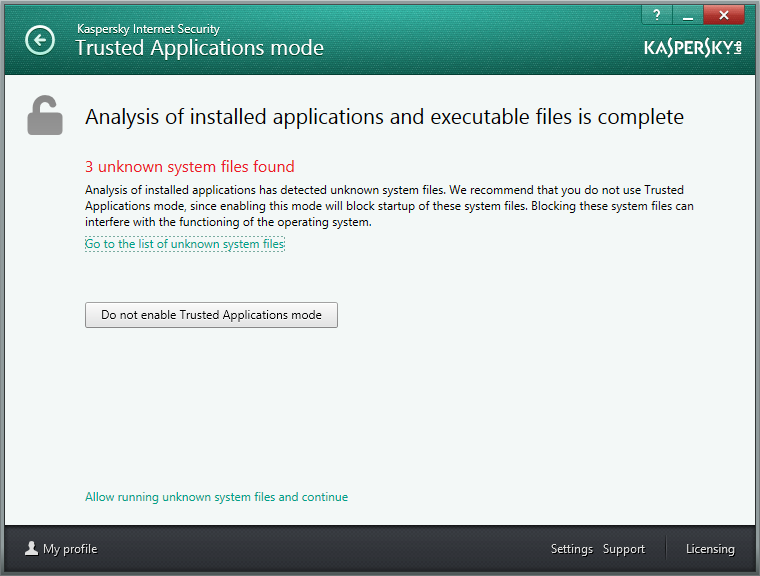
Another main difference between Trusted Applications mode in KIS 2014 and its corporate version is the real thorough prep that it does before it gets launched. By default, after installing the product the feature is turned off, so users have to take a decision as to what to allow and what not – so they’re not shocked by unusually strict behavior of KIS affecting the computer.
During this pre-launch prep KIS automatically takes an inventory of all used programs, DLLs and scripts using our Dynamic Whitelisting. The user then has a look at the prepared inventory, enters any corrections (if any personal wishes for software classification are needed), presses ‘OK’, and starts using the comp with a new, much higher level of protection – in a fully ‘checked and trusted’ environment.
Despite the fact that we have the world’s only certified trusted software database, and also the fact that it is one of the biggest such databases in the world (in tests it was shown to know about 94% of all legitimate software out there, which totals today more than 850 million programs) – there’s always something (e.g., the 6%) we’ll have missed. But that’s bound to happen, as new software appears constantly, as do updated versions and patches, and so on. All this new software gets instantly distributed right around the world via the WWW – and all of it may also deserve ‘trusted’ status, but we just haven’t got round to it as, well, we aren’t Superman. But have no fear, for at this juncture in kicks another feature of Trusted Applications mode – Trusted Domains.
With Trusted Domains, we conduct a kind of accounting of websites that offer downloadable software (developers and file collections), each of which sites has a rating of the level of trust. If a site hasn’t been known to distribute malware, it’s given a high rating and all new software from it is automatically classified as trusted (further analysis by our Whitelisting Lab may change that verdict later).
We also solved the problem posed by program modules that constantly update. Instead of having our analysts check each new file, a method is used for ‘inheriting’ trusted objects, i.e., a trusted chain of applications. For example, if a trusted program launches its update, that update automatically inherits trusted status. This adds to overall system flexibility, adaptability and autonomy. Nice.
And just one more small, but no less tasty, characteristic of this mode…
Let’s say we trust a certain application, but then unexpectedly a vulnerability gets discovered through which cyberscum start pumping some nasty malware. Or a digital certificate gets stolen from a developer and the respective software is being used to surreptitiously feed users some kind of backdoor.
Well, with KL (naturally) there’s no need to worry at all. We’ve already thought – long and hard – of those possible scenarios. KIS 2014 has a Security Corridor. This is a set of typical actions that are sufficient for programs’ basic operations – and we don’t allow even trusted programs to go outside the limits of such a corridor. For example, why would a simple text editor suddenly need to inject code into the system processes or to load a driver? That would clearly be outside the Security Corridor; therefore – not allowed.
After having read all the above, you might wonder why the various signature methods, blacklists and other security features are needed in KIS. You could easily think that Trusted Applications mode by itself provides ideal protection for a comp. After all, it’s not afraid of future threats, demands a minimal amount of resources, and is sufficiently autonomous. And another thing… why is it that other developers do whitelisting either really modestly or not at all?
Well, as to that last question – others aren’t big into whitelisting because the tech involved requires huge investments – both initially and throughout the whole long process of development. For example, we’ve several dozen experts – software developers and malware analysts and others – working on this project. We even have a dedicated Whitelisting Lab and a special partner program with third party developers who submit their software to our database. Plus it all requires complex technical and business infrastructure, which also demands constant attention and investment.
And back to your possibly wondering why other security features might not be needed besides Trusted Applications mode… Well, I’ve already talked about the economics of cyber-attacks here. Our task is to create a degree of total protection (at as many different levels and in as many effective ways as possible), the financial cost of overcoming of which is as high as possible. After all, unconquerable protection doesn’t exist. There exists only a calculation of the cost of getting through defenses. Thus, all together – Trusted Applications mode + traditional security features = a lot better than just traditional security features. Even if some cyberbaddie has enough brains and wherewithal to get over the first level of our protection, further on new obstacles await him.
That’s it for your first installment about KIS 2014. To be continued!…