March 20, 2013
Cjdthityyj ctrhtnyj/.*
As some of you may have guessed from the title – this post is about encryption!
Actually, about the new full-disk and file-level encryption that are featured in our new corporate product.
Let me warn you now from the outset – there’ll be quite a bit of specific tech terminology and information in this post. I have tried to make it as minimally heavy and dull as possible. However, if the business of encryption will never manage to wet your whistle just a little, well, you can simply sack the idea right now before you begin – and learn all about the touristic treasures of New Zealand, for example :).
Soooo. Encryption:
But before we start, you may be wondering why all of a sudden we decided to get involved in encryption in the first place when there are plenty of companies out there that already offer crypto solutions – including free ones, commercial ones, and shareware ones; and also proprietary and open source ones? Why indeed. Does the world really need another? Of course it does – if it takes encryption up to a wholly new level and combines multiple security features into one superior solution like no other. But I’m getting ahead of myself…
First, re-rewind, context, background, etc…
On these cyberpages I’ve already pored over the two main problems of corporate IT Security – (i) off-the-scale complexity and sophistication of IT systems, and (ii) the fact that the budgetary pockets for creating, adapting and maintaining such IT systems aren’t bottomless. In actual fact these problems apply not only to IT security, but IT on the whole. And if you dig deeper, you discover that they’re global problems.
Curiously, these two problems adhere strictly to the law of communicating vessels: an attempt to tackle the budgetary problem with non-budgetary means (for example, by installing free software) automatically raises the level of liquid across all vessels – that is, raises the complicatedness of the system, which comes back via a sinister Catch-22 to raise the total cost of the system.
So what’s the solution?
The solution is: going all-in-one. Protection from malware, spam, zero-days and other Internet evil; whitelisting, default deny, application control, mobile device management (MDM) and web traffic management, and last but not least – encryption; all these vital aspects of overall security controlled via a single systems management console; and all without the characteristic tradeoff between reliability and functionality.
Running through the whole system – underpinning it in fact – is encryption. The encryption of data is of course necessary for preventing access to data in case of loss or theft of any corporate – or for that matter, these days, private – kit. Incidentally, according to an interesting Intel investigation, every lost laptop costs a business on average around $50,000; the cost of the equipment makes up only 2% of this sum; the rest comes from damage caused by compromised data (so can you imagine just how much money you can save with encryption?!).
However, encryption plays other important security roles besides this obvious one. For example, encryption is right up there on the battle front in the fight against data leaks. It also strengthens full-fledged application control, helps separate personal and corporate data on mobile devices, and more besides. Accordingly, the encryption market has seen a marked shift from highly tailored to multifaceted solutions. And that includes, naturally, the new encryption features to be found in our new KESB.
Rightie. Now for the details of the encryption that’s sprouting up in our products – and how it’s better than what others have to offer…
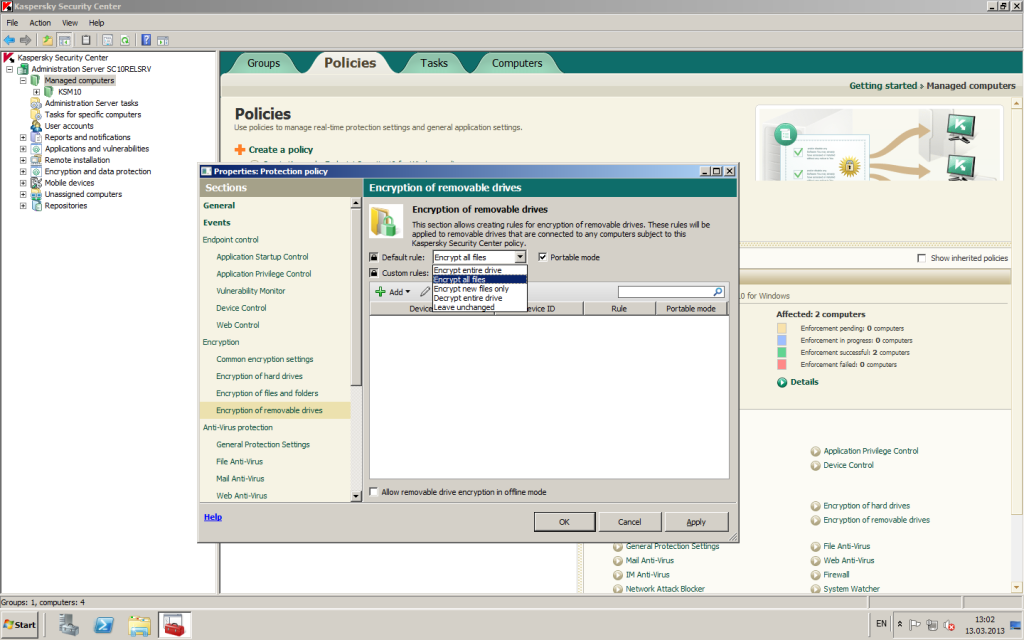
It just so happens that everyone has different ideas as to what they’d like to see in an encryption system, and that’s why we decided to cover them all. We’ve got two types of encryption on the menu: FDE (full disk encryption) and FLE (file level encryption), so everyone’s particular requirements can be accommodated just perfectly. Or you can have a bit of both; for example, using FLE for protecting office computers and FDE for laptops.
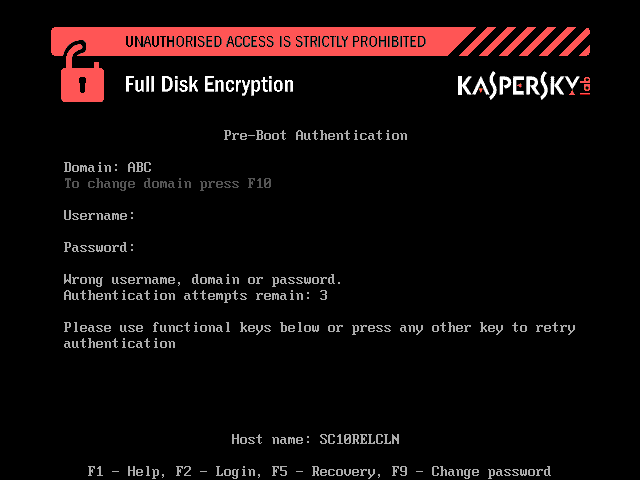
FDE, as its title suggests, encrypts absolutely everything on a medium, with authentication before loading the OS. And it’s here where we added another useful feature: by entering one’s login and password at this stage the user also automatically authenticates him/herself into the OS as well (big shout out to single sign-on).
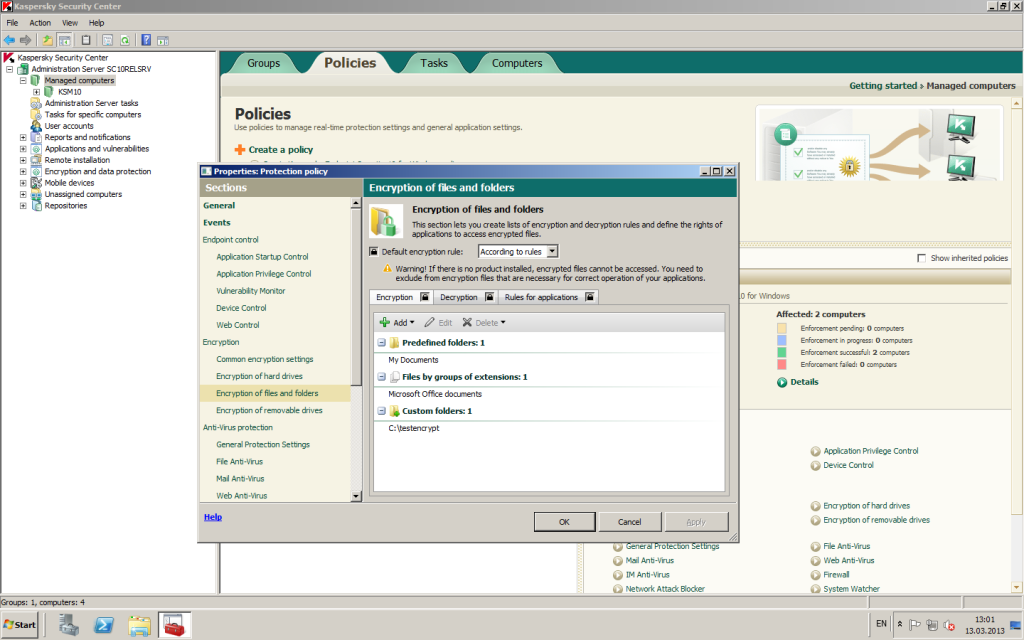
And FLE – this is of course encryption of separate files and folders.
Now let me point out how we’re better than the competition – in three chief ways:
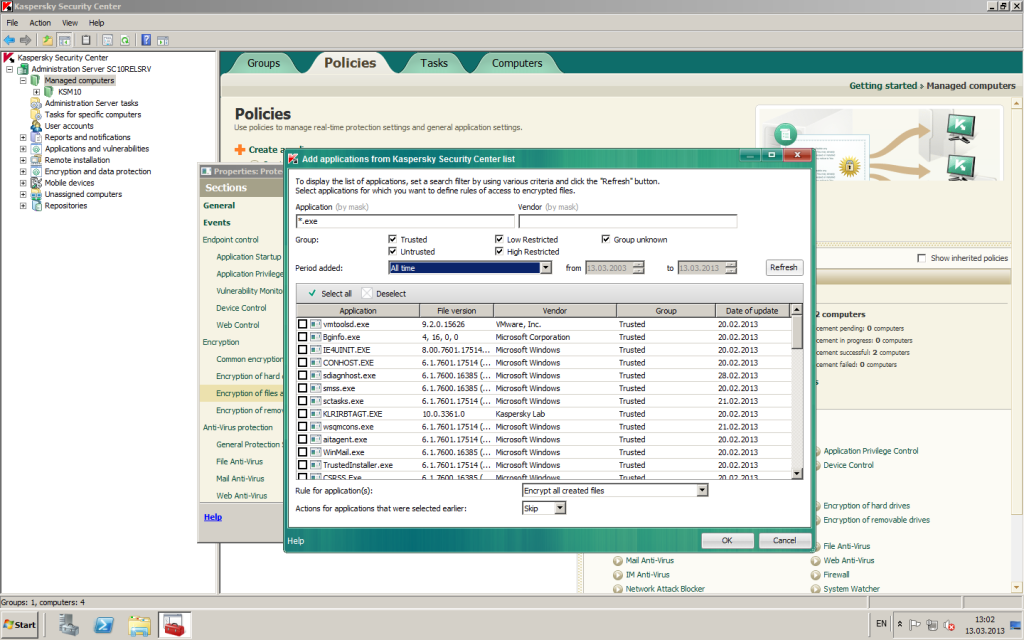
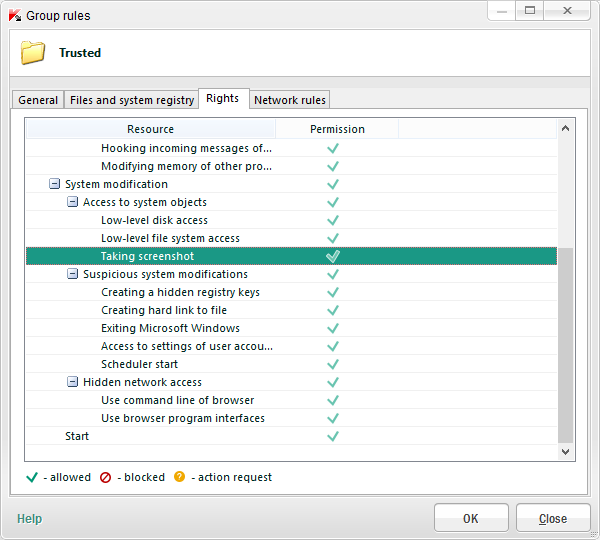
- Our encryption can be fine-tuned so that it encrypts only specific types of files (for example, .doc or .xls), but it can also encrypt all types of files created by specific applications – no matter their extension or location. Besides, you can take advantage of the integration of technologies and adjust specific encryption rules for each program using another integral part of our solution – application control.
Another practical example of the advantages of integration: data may be FLE-encrypted on a computer, but a gaping hole remains – the Print Screen function. With our application control it’s possible to block applications that can print the screen, while the sysadmin can simply disable the magic Prt Scr key in the system registry.
- Our encryption makes sure files stay encrypted when they move about a network. Many competitors protect data only locally, and upon their transfer over a network or copying to an external medium they get unlocked (I kid you not).
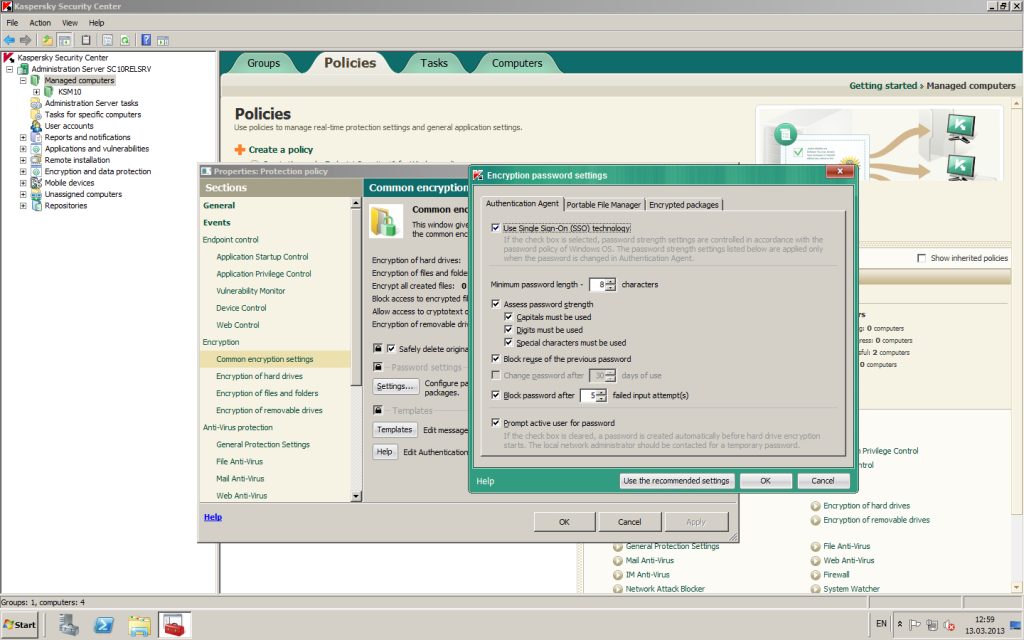
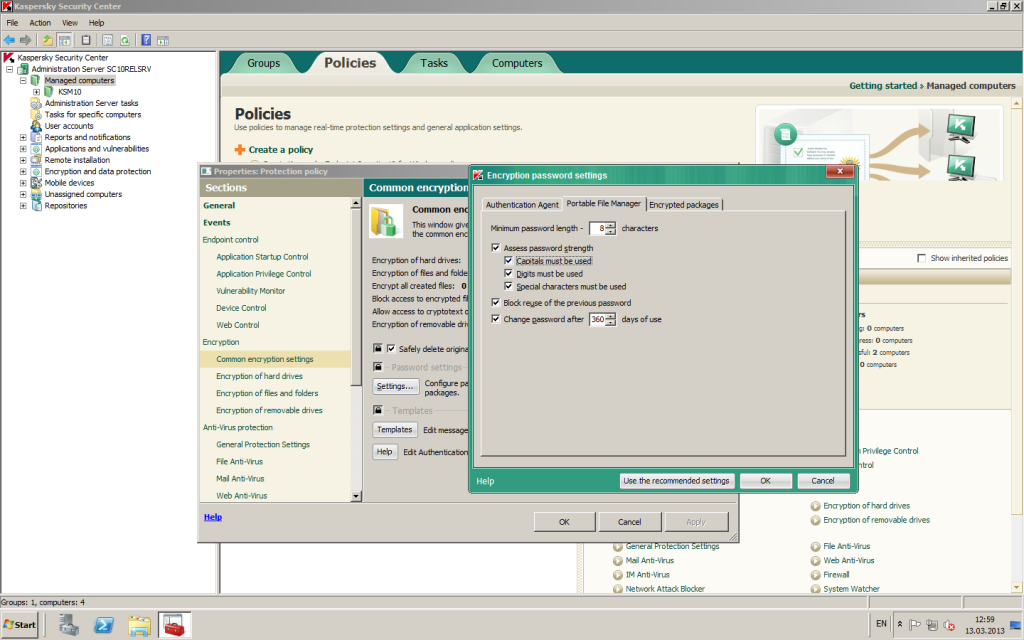
One more interesting feature – if using encrypted USB sticks, there’s a so-called portable mode, which allows authorized users to open files even on computers where our product isn’t present. For this there’s a special autonomous file manager – kind of like a mini-browser. To view files with the browser the user needs to enter his/her password; and it can’t be 12345 or something similarly insane, but one with a security degree greater than the minimum set by the sysadmin as per the respective corporate policy.
- Now there’s the possibility of limiting access to encrypted data for specific applications. For example, to block the sending of encrypted files via Skype, while maintaining Skype’s main functionality. And if someone tries to save or transfer confidential files via a public cloud service like Dropbox (which has been known to be hacked), then they’ll be saved/transferred in encrypted form automatically.
Both FDE and FLE work behind-the-scenes; that is, they work in the background and perform encryption/decryption of data on the fly, requiring neither intervention, confirmations, nor other things like “press any key”. In other words, upon an attempt to write anything to disk, our agent quietly intercepts the operation, encrypts the data and puts them in the right place. The algorithm used is the industry gold standard – 256-bit key AES, which can be hacked – for a mere $1.5 trillion, with four terawatts of electrical energy (more than the USA’s consumption in a year), and using all the computing power, er, there is in the whole world!
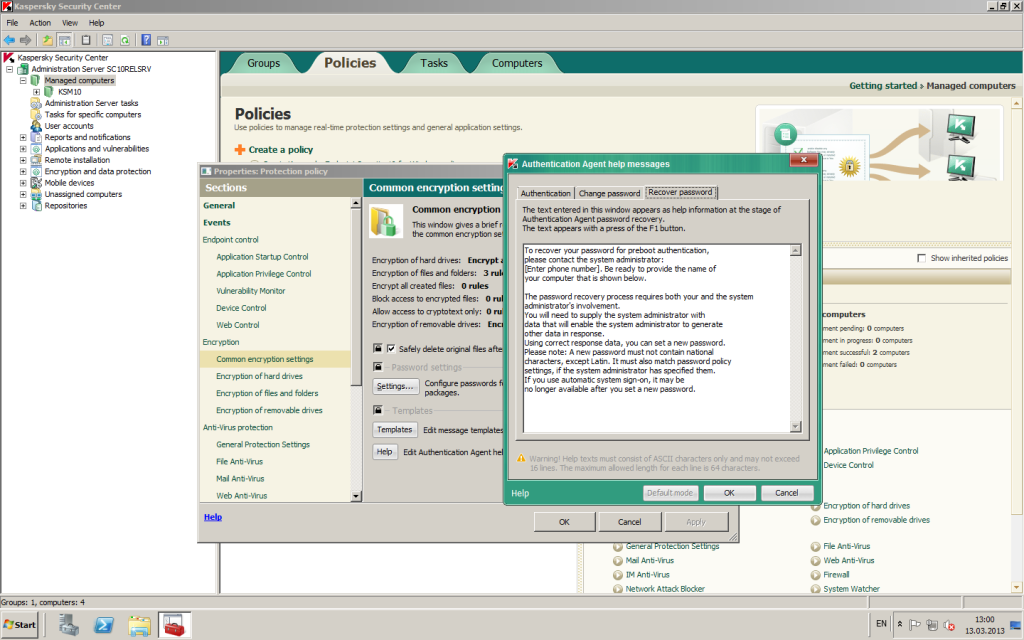
Of course, malfunctions can occur – be they software, hardware, or human ones, but for them there’s a suitable resource of last resort. The sysadmin has at his/her disposal a restore disk with a special utility that can decrypt data. User forgetfulness after the summer holidays can easily be cured with challenge-response authentication. While if that forgetfulness suddenly turns out to be more intentional and malicious than benign, encrypted data can be accessed via admin accounts.
All three of the above – and the rest – are pulled off with no confusing mish-mash of local agents, control systems or policies. All functions of encryption (as with other protective functions) are contained in one application, managed from a single console, and comply with a single security policy.
So, how come we managed to secure such an encrypto-tech coup here, while others couldn’t?
It’s all quite simple really: we don’t run about the industry buying up other security vendors with the aim of conveniently skipping the process of development. No, no. With such an approach foul-ups always inevitably occur, as do corporate incompatibilities. No, we’ve done it all ourselves, from the ground up. The result is our being first in coming up with encry-p(ro)tection as part and parcel of an all-encompassing complex solution, with its implementation, internal integration among different technologies, flexibility, and scalability all turning out to be a head taller than the competition. Oh yes!
Briefly – about plans for the future:
Currently encryption works only on Windows workstations. In future versions we’ll adapt it for Windows servers as well as for Linux and Mac machines. We’ll also add support for smart cards and tokens for entry upon loading the OS, extra methods for restoring access to data (secret questions), keeping files encryptied when they travel via email, and lots more besides.
More detail about encryption: in our corporate brochure, or on this site.
* PS: who guessed what’s written in the title of this post?