September 21, 2015
September 17, 2015
Parade!
As if the Beijing temples and Summer Palace weren’t sufficient, we also managed to experience a full-blown state military parade right on Tiananmen Square!
One word: grandiose.
We got there early in the morning in fully festive spirit, as did other ticketholders – all 50,000 of them! Most had cameras, and many were decked out in full traditional national costume – including most of the children. Oh, and as I explained how in my previous Beijing post, there wasn’t a cloud to be seen anywhere over the capital.
Read on: spectators assembled, troops at the ready, let’s begin!…
September 17, 2015
A town called palace.
What else did we manage to see in and around the Chinese capital?…
Here’s one other thing – let’s say, the main course: the Summer Palace (Yiheyuan)…
September 17, 2015
KL lands in Milan.
Ciao all!
Just in case – I’m writing this from… Milano!
… Where we’ve just had the opening ceremony of our second Italian office! Eccellente!
Here it is from the inside:
September 16, 2015
Beijing temples.
Before last week, I’d made the grave mistake of thinking that in Beijing and its near surroundings there are just two main places worthy of attention – the Forbidden City and the Great Wall of China.
I couldn’t have been more wrong. It turns out there are loads of places totally in need of checking out, and I recommend everybody reading this to do so one day. I was lucky – this time in the capital I had quite a bit of free time on my hands between business engagements, and managed to fit in a whole five awesome tourist attractions. Among them: three Beijing temples and the Summer Palace, about which I shall now write a little, and show plenty of hi-res pics of…
Temple No. 1 – Beijing Dongyue.
One of the oldest temples of Beijing, it’s also one of the most tourist-less – making it, perhaps paradoxically, more appealing to tourists (like me). Highly recommended. If you’re ever in Beijing – you must get here.
September 14, 2015
Ninth round-the-world trip!
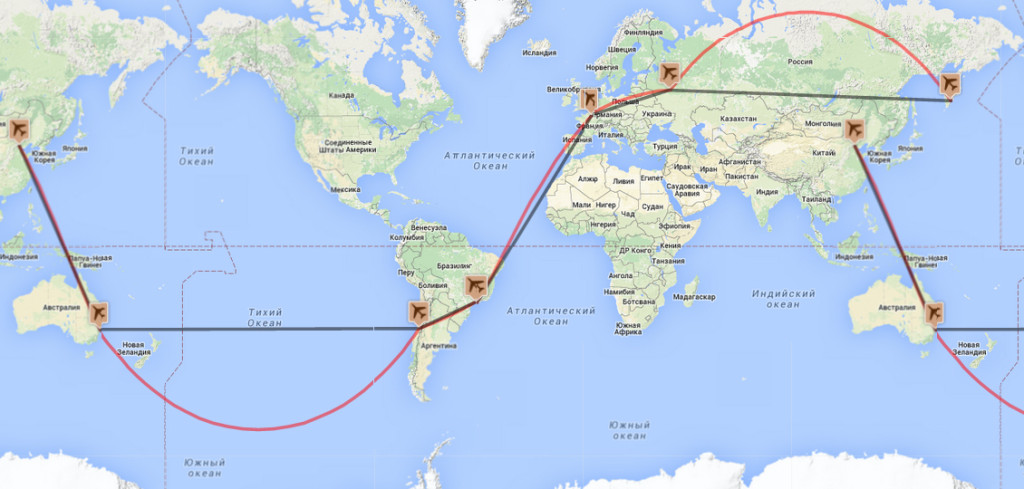
After a two-hour express connection in Sydney, and 12 hours up in air on the Santiago de Chile – Beijing route, we finally land. Phew! This completes my latest circumnavigation of our planet: 25+ hours in the air, 32 hours traveling door-to-door. A little tired, but never one to complain.
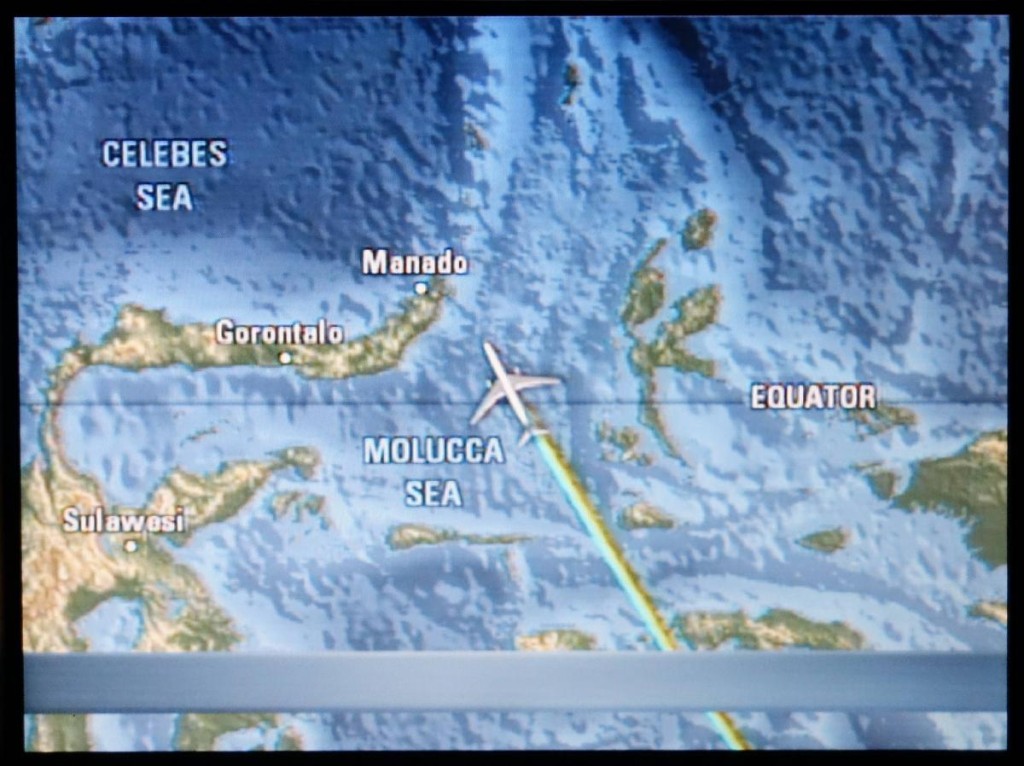 Our flight crossing the Equator
Our flight crossing the Equator
It turned out to be rather an exotic route in all, and not just because we flew past Antarctica: we crossed the Equator twice and half the trip was in the southern hemisphere. The route had a certain symmetry too it too (see the map below), and in all four continents (Asia, Europe, South America, Australasia) were visited. Oh, the main bit: this was my ninth round-the-worlder! Hurray!
I hardly noticed. Round the world in 10 days! It all started in sunny Kamchatka, and finished in China: Petropavlovsk-Kamchatsky – Moscow – Paris – Sao-Paulo – Santiago – Sydney (connection) – Beijing. A resourceful friend helpfully marked the route out on a world map:
September 10, 2015
Kamchatka-2015: Snowy peaks, hot springs.
The second set of amazing must-sees to the south of Paratunka are the hot springs near Khodutka volcano. In fact they’re not just hot springs, they make up a whole hot lake. And not just a hot lake; it’s more of a scalding lake: the temperature of the water hovers around 43°C. Now, if you’ve a heart as strong as an athlete’s, you could take a dip, but you won’t really fancy doing a fast crawl or anything – far too parching. Shame. All the same, just sitting in the lake – still a thoroughly satisfying way of taking in all the surrounding scenery.
September 9, 2015
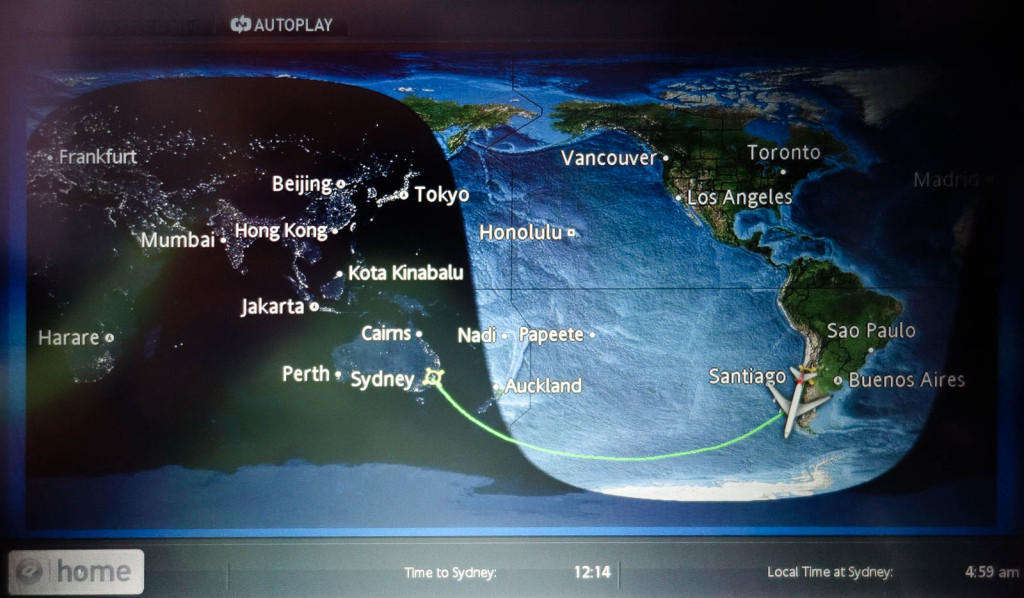
The Santiago–Sydney Antarctic ‘Smile’: QF28
Hola amigos!
Not long ago I flew one of the most unusual commercial air routes I’ve ever taken.
It was the Santiago–Sydney-route on Qantas QF28 in a Boeing 747. The route forms a smile shape as it curves downwards and flies past… Antarctica! It felt a bit eerie flying – for 14 hours! – over a part of the world where there happens to be absolutely nothing at all! No islands, no ships, no folks, no hamburger stands… the very definition of ‘godforsaken’! Even submarines don’t bother with these remote southern reaches. Curiously, there’s one thing that features relatively prominently here: deceased satellites! They have them fall out of orbit and give them a marine burial here, well out of the way so they do no harm to Homo sapiens.
“Cheese!”
September 8, 2015
Smoky Santiago.
Santiago (the capital of Chile) is situated in a valley between two mountain ranges. The bigger of the two is called the Andes. The other… I never did get round to finding out its name. Anyway, the reason I’m telling you this is that, by and large, the wind here tends to blow across these ridges – i.e., not down the valley – leaving the valley, and Santiago, thoroughly ventilation-less. This means there’s nothing to shift the thick smog that hangs over the valley. It looks, to be honest, disturbing. Imagine breathing that in all day and night, year after year. Yikes!
September 7, 2015
Dream airliner = Dreamliner.
It had to happen sooner or later.
What with the hundreds of flights I make in a year, with all sorts of different airlines, to and from all sorts of random cities, my getting aboard such a plane was sure to be sooner rather than later.
A dream flight. On a dream airliner – the Boeing 787 Dreamliner. Packed with the very latest technologies, a curvaceous ‘designer’ form, and improved comfort. I’d been patiently waiting for this moment quite a while. And then suddenly, unexpectedly, and totally by chance… it finally came to pass…