December 26, 2014
My 2014: A rush and a push and the land is ours and crisscrossed.
There are just a few days left of this year, so I’d better rush and push and go over 2014 in review, before I get on to congratulating everyone for having a super year and wishing all the best for a supreme 2015…
So what was what, where, why, how, eh, and all that…
Geographical firsts.
Three years ago I came up with a list of what I reckon are the ‘Top-100 Must-See Places in the World‘ – a list of what I consider are the most mind-blowing sights around the planet. I hadn’t been to all the listed places – many were still left to ‘do’. This keeps things interesting – at least for moi! – as I get to keep steadily adding checks against the still-to-do’s (normally while on business trips – can’t beat two birds with one stone and all :).
In 2014 – six new checks:
– Patagonia;
– Big Island, Hawaii (details here and here);
– Norwegian Fjords;
– The Kurils;
– The tunnels of Jerusalem;
– Kathmandu, Nepal.
So what else did I get to see this year that wouldn’t fit in the Top-100?
Four very impressive locations:
– The cliffs of Western Ireland (details here and here);
– The cliffs of Southern Portugal;
– Around and about Monaco;
– Mount Fuji – again.
The Irish cliffs are like totally worthy of inclusion in my Top-100; however, for them to be included some place would have to be removed. But what? No easy task…
Here are a few more curious events from the past year… mostly a lot closer to home than the exotic locations of most of the Top-100:
– Meeting Angela Merkel;
– Buying an elephant;
– Witnessing a launch of Soyuz at Baikonur;
– Experiencing weightlessness;
– Being on Japan’s main TV channel;
– Our office being named the ‘Best Office in Moscow, 2014’.
Brand EK.
I’ve been doing fairly intense KL-PR stuff for years already. This year it was as intensive as ever…
– 50+ ‘top-tier’ (PR/media jargon) live interviews;
– 40+ presentations;
– 30 press conferences;
– 3 photo sessions.
All the above figures and events give us the following auxiliary stats too:
– 95 flights, 375 hours in the air;
– 45 new cities (maybe a few more – some might have slipped through the net);
– 3 new countries: Kazakhstan, Nepal, Luxembourg.
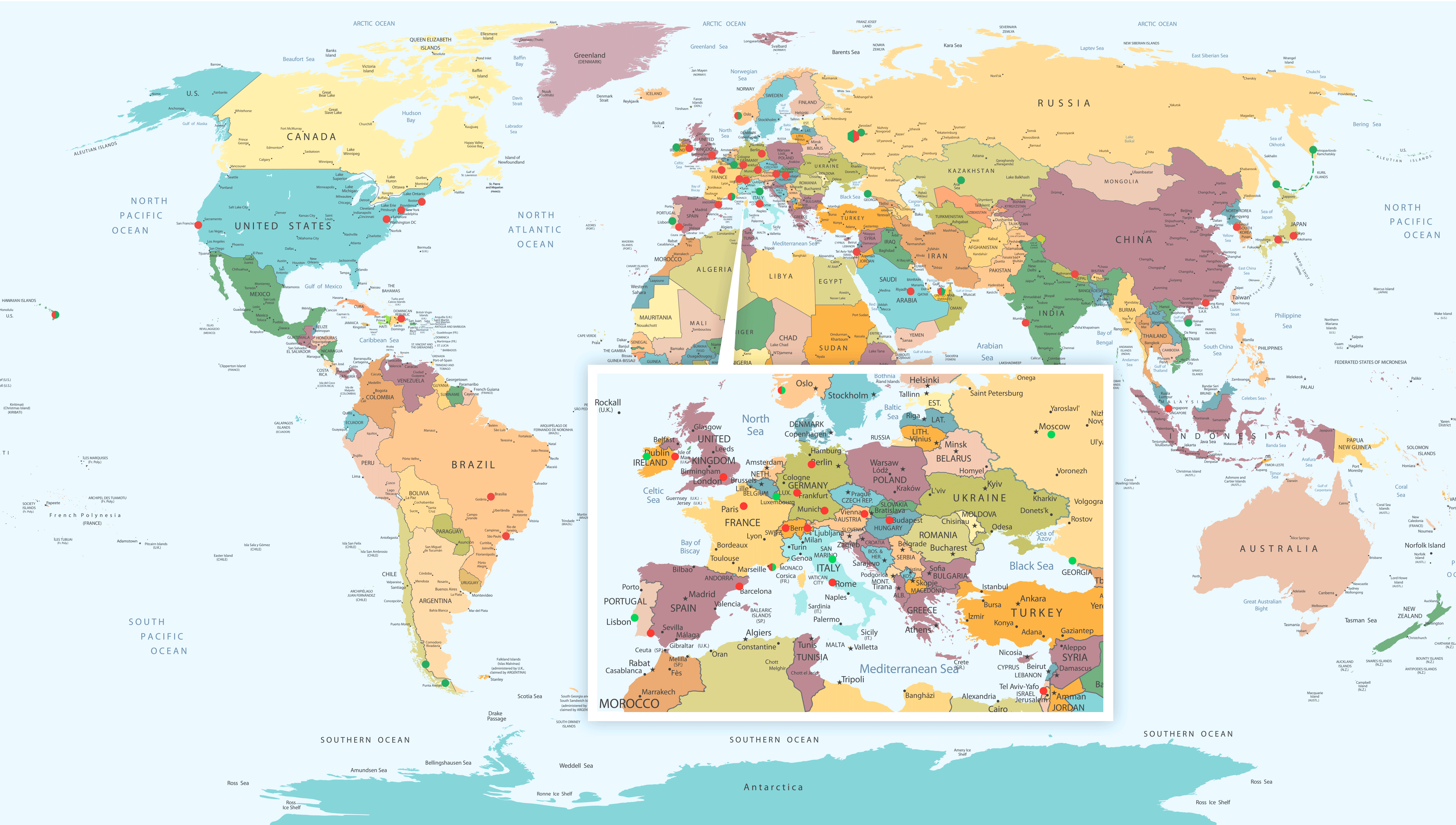
Transferring all the above onto a world map, we get the following. Red spots – business; green – tourism:
And here’s a rundown of the trajectory of my movements around the globe, as extracted from my scribbles in my trusty travelogue-notepad:
Moscow – London – Davos – Tel Aviv – Moscow. Punta Cana – Sao Paulo – Brazil – Punta Arenas – Riyadh – Rome – Hannover – Seoul – Sanya – Moscow. Baikonur. Washington – Boston – Hawaii – San Francisco – Moscow. London again. Tokyo. London, Monaco. Munich, Bergen, Hong Kong – Kathmandu – Mumbai – Geneva – Moscow. Petropavlovsk-Kamchatsky – Kuril Islands – Yuzhno–Sakhalinsk – Moscow. Washington – New York – Budapest – London – Tel Aviv – Paris – Moscow. Singapore – Jerusalem. Sochi. Wiesbaden – Luxembourg. Hong Kong – Tokyo – Osaka – Monaco – Dublin – Vienna – Moscow. Bologna – Venice – Barcelona – Faro – Lisbon – Moscow. Abu Dhabi, Star City.
And on that satisfying note folks, I shall sign off on the year. Thank you for your attention and patience! I wonder what next year’s travel-summary will look like. I think I’ll have to start taking it easier maybe – less non-stop marathon world-tours. Yeah, right!
Happy Boxing Day!
Cheers!