May 26, 2014
Cybernews from the dark side – May 26, 2014
Greetings droogs!
It seems ages since I’ve touched upon a cyber-maliciousness topic on these here pages – what’s hot and what’s not, what’s in and out, and all that… You might even think we’re twiddling our thumbs here seeing as I stay shtum on topics relating to our raison d’être…
Well just let me reassure you that we are on top of EVERYTHING going on in the cyber-jungle; it’s just that we publish all the detailed information we have on dedicated techy news resources.
The only problem with that is very few folks actually read them! Maybe that’s understandable: the detail can get tiresome – especially to non-tech-heads. Not that that’s a reason not to publish it – far from it. However here on this blog, I don’t bog the reader down with too much tech. I just give you the most oddly curious, amusing and entertaining morsels of cybernews from around the world.
Sooo, what was curiously odd, entertaining and bizarre last week?…
“He hit me!” “He started it!”
The sparring between the USA and China about cyber-espionage has taken a new turn…
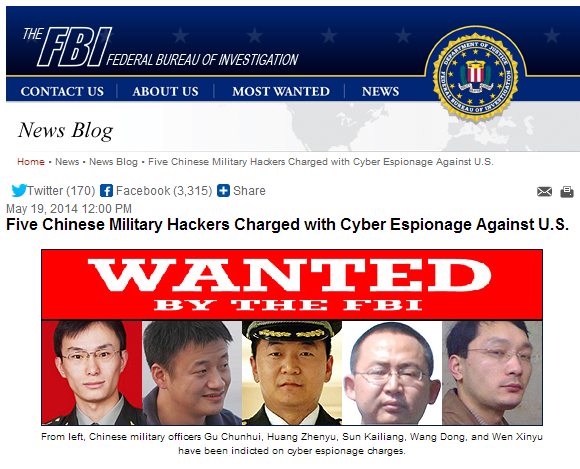
This time the Americans took their swipe with photographs and names of ‘guilty’ individuals: five Chinese military specialists have ended up on the latest classic Wild West-inspired FBI ‘Wanted’ poster for allegedly breaking into networks of US companies and stealing secrets.
How they came upon these particular individuals will remain a mystery. We’ve been explaining repeatedly how finding out who’s behind cyberattacks is a wholly imprecise science: it’s not only absurdly difficult to accurately attribute an attack to a certain country or secret service – it’s practically impossible to pinpoint a specific responsible individual.
All in all – another example of some seriously perplexing cyber-alchemy.
The Chinese, understandably, were quick to respond. But this toing and froing is hardly anything new. It’s been going on for a few years already. Here’s an example – of a volley going in the opposite direction. What’s clear is that (i) this is just the latest installment in a long ongoing campaign; and (ii) the campaign itself is only one piece in a complex jigsaw of global political face-off. Reminiscent of a Le Carré novel with China substituting CCCP.
Pass the word on passwords
Rarely a week passes without emphatic recommendations to users of this or that large web service to promptly change their passwords after hacker attacks and potential theft of customer databases. Due to the weekly frequency, such announcements lost long ago the ability to shock anyone too much, arousing interest neither in the media, nor of users themselves. But last week’s alert came not from just anyone, but no less than eBay, which has 148 million active accounts.
The problem with passwords has long been rather a headache for the Interneted population. You need scores of passwords, and if you have a different one for every account they can’t all be remembered. As a result we tend to use lame passwords (though it’s good to see at least some systems now indicate password strength upon registration), and we use them for all our accounts! Therefore, if you do get hacked, you have to change passwords for 20 or 30 or 40 or more different sites. Rather, should change them. Of course, not everyone actually gets round to doing this; therefore, the overall security level of the Internet is slowly but steadily falling.
There’s a simple solution: use a password manager. A password manager recommends a real strong password that you don’t have to remember – it automatically enters it for you on sites. And btw, we also have this cool service.
Where do you want to go today?
This isn’t really about malware and criminal hackers, and I won’t even comment on it – I’ll just drop a few hints.
In California they’ve approved rules for the use of driver-less cars on public roads. Though the rules are draconian, and for now they only apply only to manufacturers for testing, what’s clear is that cars traveling on roads without a driver behind the wheel looks set to soon become a reality and not just science fiction. Hmmm. I’ve just one question: what software will these robot cars use, and how will that software connect to the control center?
Utilities are like kids…
…They spend too much time online.
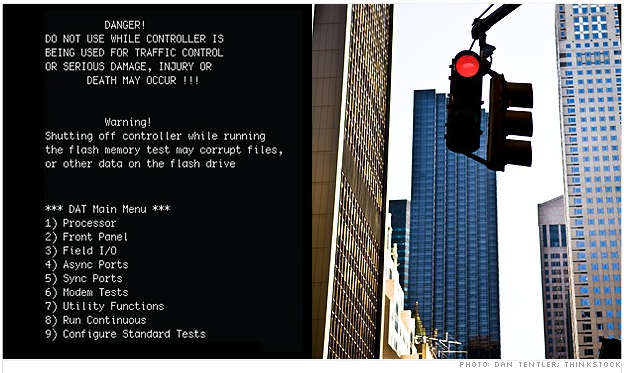
Ah, here we go again…: SCADA and cretinous critical infrastructure! Whenever I read anything from this cyber-front I get all apocalyptical in my head, and my nervous system automatically goes for some extended face palm. Last week came the news about an unnamed (but large) US public utility (water supply? Power supply? Airport?) being broken into. Who, why and what actually happened isn’t clear, but the how has be described in reasonable detail.
Turns out the system was exposed to the Internet for ages, it was remote-controllable, it had no firewall, and the password was hopeless (and easily brute forced). This was one of the rare cases that came to the surface (normally these things are hushed up). How many other similar systems have been hacked and are waiting for the command from the dark ‘owner’ isn’t clear. What is clear is that there are oodles of such vulnerable devices in the world. Want proof? There’s even special search engine for seeking them out.
Jeeeez. Just do something people! At least disconnect this life supporting stuff from the Internet! Don’t wait till it’s too late. In fact, just what ARE you waiting for, exactly?
Hackers can reside anywhere – even on aircraft carriers
Oh my giddy aunt.
The head of the Team Digi7al hacker group ran its actions… from onboard the nuclear aircraft carrier USS Harry S. Truman! According to the official report the group was fairly amateurish and kinda just playing about, but still… the effrontery!
What’s most alarming is that the hacker turned out to be not a simple sailor with a mop and laptop with a perceived grievance or whatever, but the sysadmin of the ship! That is, very capable and no doubt with access to all sorts of secret stuff… Apparently he did hack into the ship’s systems too. Imagine what he could have gotten up to with all that software-controlled military hardware!!
The hacker gave himself away in the end as usual by some clumsy slackness – he started to post tweets from the official account of the group right from on board the ship. I can imagine the amazement of the agents when they found out where the tweets were coming from.
// Interesting, how did they ‘take’ him? Did they land early morning on deck, or was it a seaborne approach? Did they all wear sunglasses and forever hold their earpieces?…
For a bright future, don’t wear Blackshades
There was a rich harvest on the hacker fields last week by the FBI and friends. 90 arrests in 19 countries and, as the primary source promises – it’s all ‘to be continued’. All those arrested were mixed up in the development and use of the Blackshades Trojan – a cheap but scarily functional backdoor for cyber-surveillance, espionage, theft and other such nasties.
The ready-to-use Trojan became rather widely distributed on underground forums, where it could be bought for a few dozen dollars. How many were procured and are still out there isn’t clear. What is clear is that plenty we’re sold. Mega-plenty. And the mentioned arrests – they’re just the tip of the iceberg. What’s nice to know in this sorry tale is we’ve been detecting this Trojan for ages.
Thank you for not smoking – ganjer!
Overall, as all the above indicates, the official bodies fighting cybercrime have got their work cut out for them. But despite the development of a varied analytical anti-malware tool chest, improved international cooperation and other helpful actions, there’s still a serious shortfall in security workforce numbers.
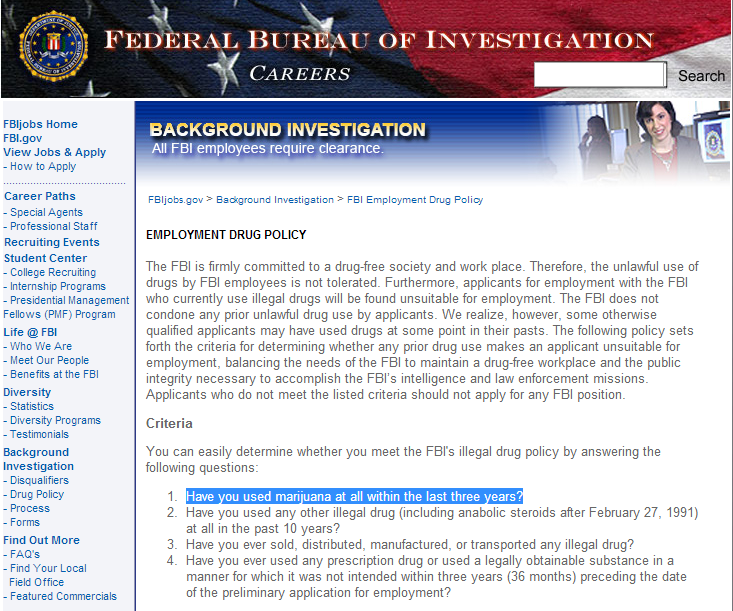
Government agencies in all sorts of ways attract and stimulate students to join the cybersecurity fold, but this still doesn’t solve the problems: IT fraud gangs form and get to work in the nick of time. And last week certain jokers highlighted another hindrance for the forces of cyber-good: FBI employees are categorically forbidden to smoke weed, and can’t even think of applying to the agency for employment if they’ve had just the cheekiest of tokes (remember – even presidents try it!) within the last three years!
So, as you can see, it was an interesting week for all things cybersecurity.
If you want to stay updated on security news without waiting for digests, I recommend regularly checking our these resources: Wired Threat Level, ArsTeсhnica, Threatpost, Krebs on Security, ZDNet, SecurityWeek, Dark Reading, and Schneier on Security.
That’s it for today folks. I think I’ll start updating you on OMG cybernews more regularly from now on…