March 5, 2015
Guatemala – what a gala (of color). Part 1.
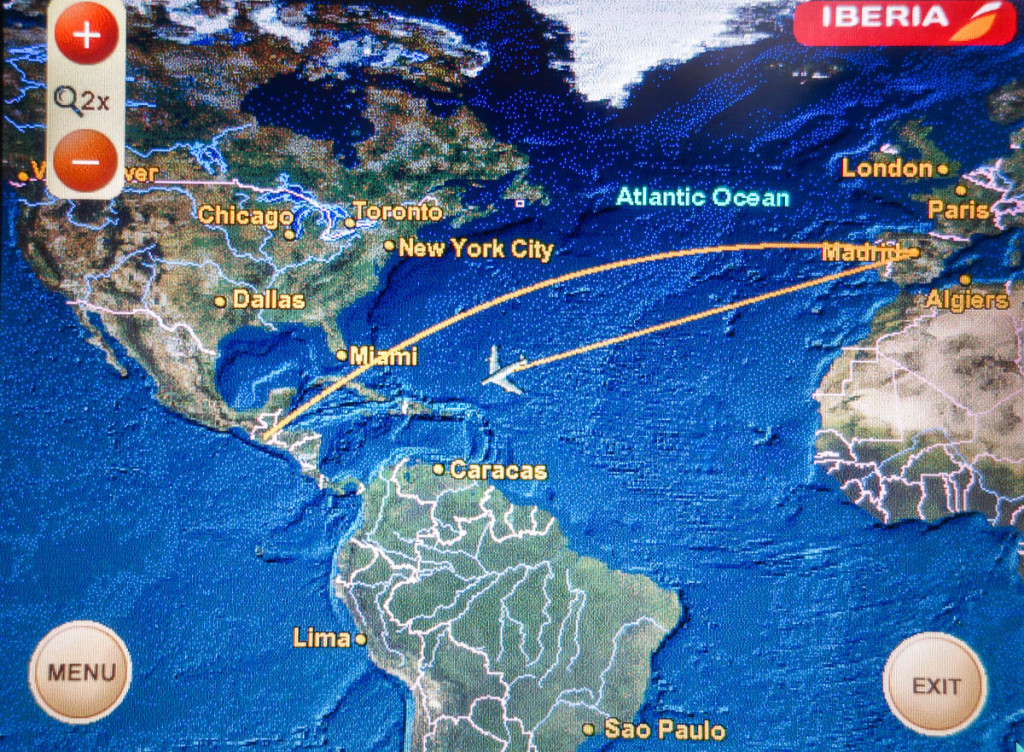
Which airline to choose to get from Madrid to Guatemala was a no-brainer: practically the only airline to fly direct is Iberia. It’s like, why would we fly with a connection – heaven forbid a North American one? :)
So off we popped, direct to Central America…
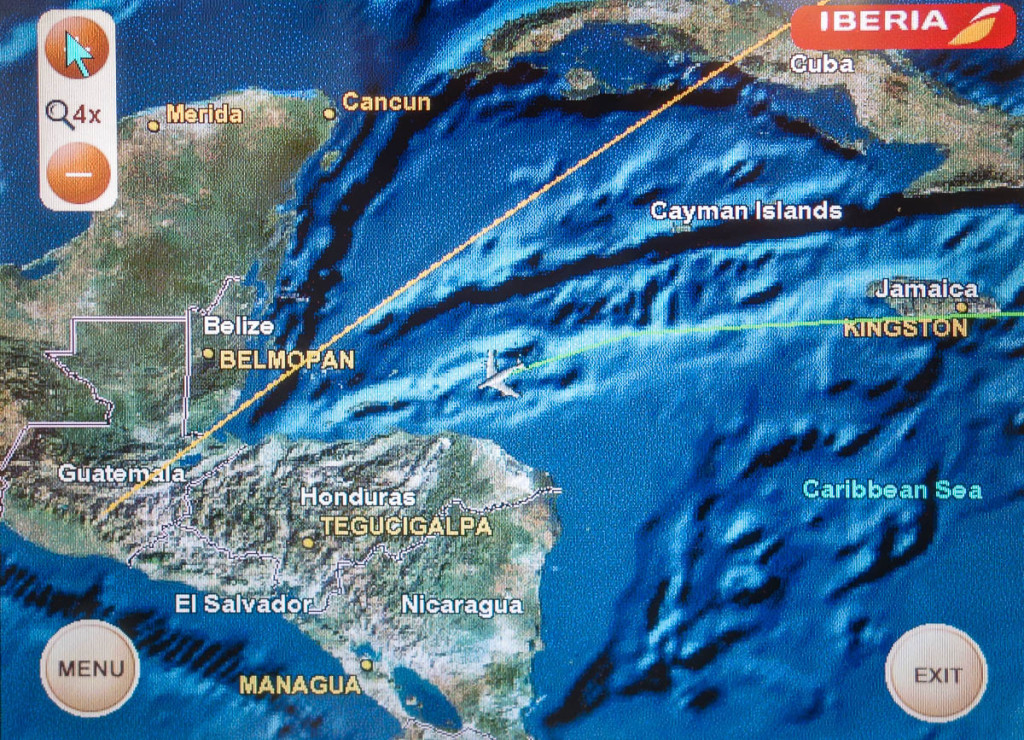
The first bit of land on the other side of the Atlantic was Haitian (I think), and then came Jamaica. Over the mainland we flew over Honduras, and next up was our country of destination – Guatemala.
Incidentally, Honduras – why’s it called Honduras? You can find out here. It appears there are two alternative versions. The first starts:
In Spanish, the word “honduras” means “deep waters” or “depths”. It is a peculiar name for a country, but there is also a peculiar story behind how our country got this name.
 You have reached your destination
You have reached your destination
Not everyone (who lives outside Central America maybe) is able to point out Guatemala on a world map. Not everyone knows it’s in Central America even – many think it’s in South America. But no, Guatemala is the quintessential Central American country – the most central Central American country, in fact.
It sits neatly between Honduras, Salvador, Belize and Mexico. Firther to the south there’s also Nicaragua, Costa Rica, Panama, and then Columbia and Ecuador.
I flew over this nest of cuckoos curiosity a while back. Unfortunately that was at nighttime so I saw nothing at all of it. This time things were different:
 Volcanism on the horizon. My cup of tea
Volcanism on the horizon. My cup of tea
 A Fuji competitor!
A Fuji competitor!
Turns out there are 33 volcanoes here, three of which, I’m told ‘represent a threat’. That makes sense: this part of the world’s seen plenty of volcanic activity in its time, some of it very sad. For example, in the sixteenth century Agua destroyed the first capital of the country; and in 1965 Pacaya blew its top violently and has been erupting constantly ever since.
And right now Fuego‘s causing all sorts of problems for the locals. And on the first night after we arrived there was even an earthquake! I missed it as I was in a jetlag-compensating deep sleep. Not sure if that was a good or bad thing.
We went for a walk up Pacaya while in Guatemala; not to the top – it’s smoking like a bar steward right now up there – but around the old crater near it. Impressive. So impressive in fact that it warrants a post of its own. I wasn’t expecting that there’d be a lot to report back on from here – I was proved wrong!
All the photos are here.
Back soon folks!…