February 6, 2017
Humachine Intelligence Fighting Snow Shoes.
Of course, I’m bound to get a lot of spam in my inbox – probably more than most. Decades of giving out my business card left, right and center; our domain included on presentation slides, in publications and catalogs and so on. Then there’s my email address’s simplicity. Sometimes employees’ blown email addresses we ‘leave out in the cold’ as spam honeypots while setting up new, slightly amended email addresses for the employee. But we can’t have that for me now can we? No. Because – first – I need to keep track of precisely who the enemy is, and – second – I want to personally be able to monitor the quality of our antispam protection. And I also don’t mind a few extra laughs now and again.
Much like entomologists with their butterflies, I file all incoming spam in a separate folder, check out the verdicts, and determine tendencies and false positives, while I forward missed samples to our antispam lab.
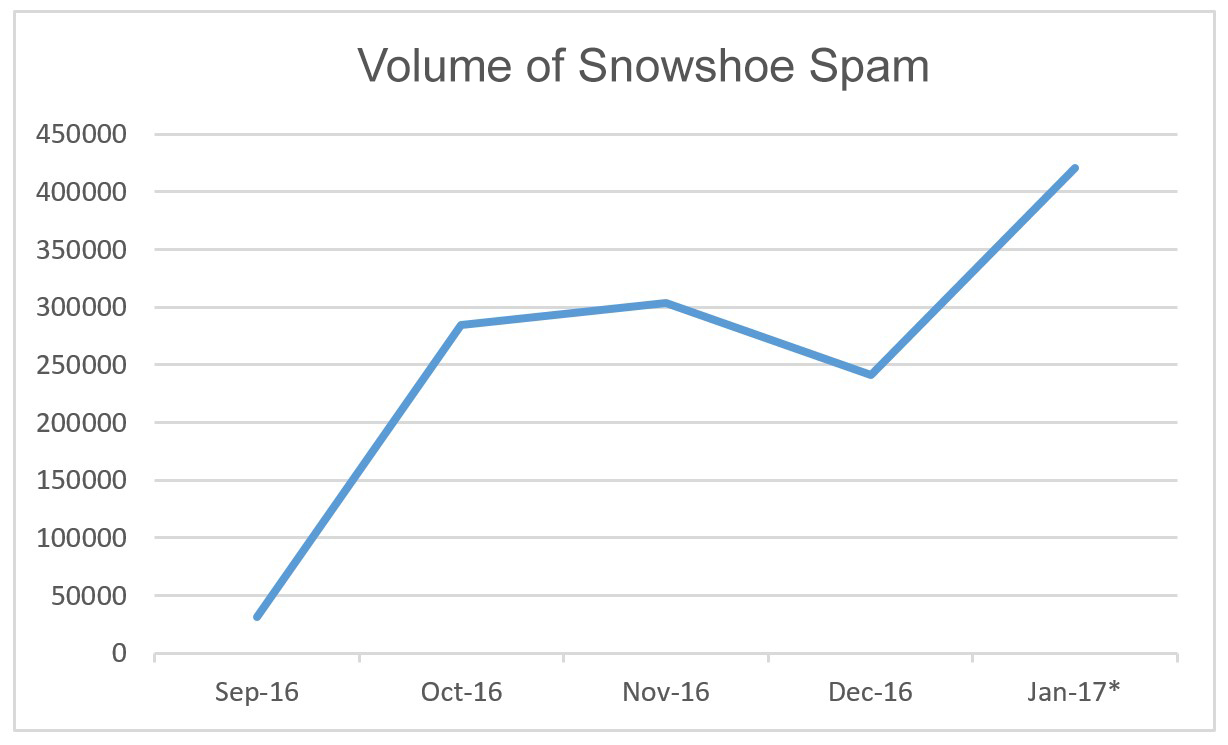
Curiously, since the beginning of the year the amount of spam has gone through the roof! And after studying its structure and style, it looks like most of it comes from one (1) source! Almost all the messages were in English (with just two in Japanese), and – main thing – 100% of this spam was detected by our products! I turned to our specialists… – and it was confirmed: it was a huge tsunami-like wave of a specific type of spam – snowshoe spam. This is unusual as normally around New Year spam activity falls in volume.
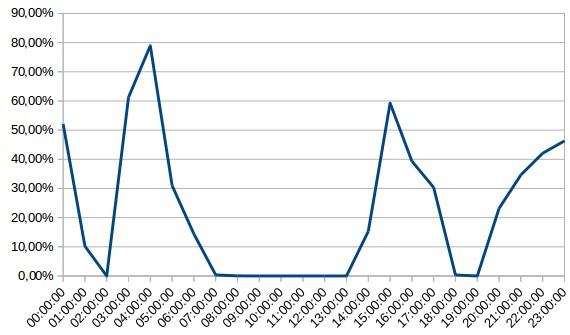
And here’s the data on how the share of snowshoe spam changed on the most active day – January 7 – in the inboxes of our corporate domain:
So just what is this snowshoe when it’s at home, and how can it be protected against?