February 6, 2017
Humachine Intelligence Fighting Snow Shoes.
Of course, I’m bound to get a lot of spam in my inbox – probably more than most. Decades of giving out my business card left, right and center; our domain included on presentation slides, in publications and catalogs and so on. Then there’s my email address’s simplicity. Sometimes employees’ blown email addresses we ‘leave out in the cold’ as spam honeypots while setting up new, slightly amended email addresses for the employee. But we can’t have that for me now can we? No. Because – first – I need to keep track of precisely who the enemy is, and – second – I want to personally be able to monitor the quality of our antispam protection. And I also don’t mind a few extra laughs now and again.
Much like entomologists with their butterflies, I file all incoming spam in a separate folder, check out the verdicts, and determine tendencies and false positives, while I forward missed samples to our antispam lab.
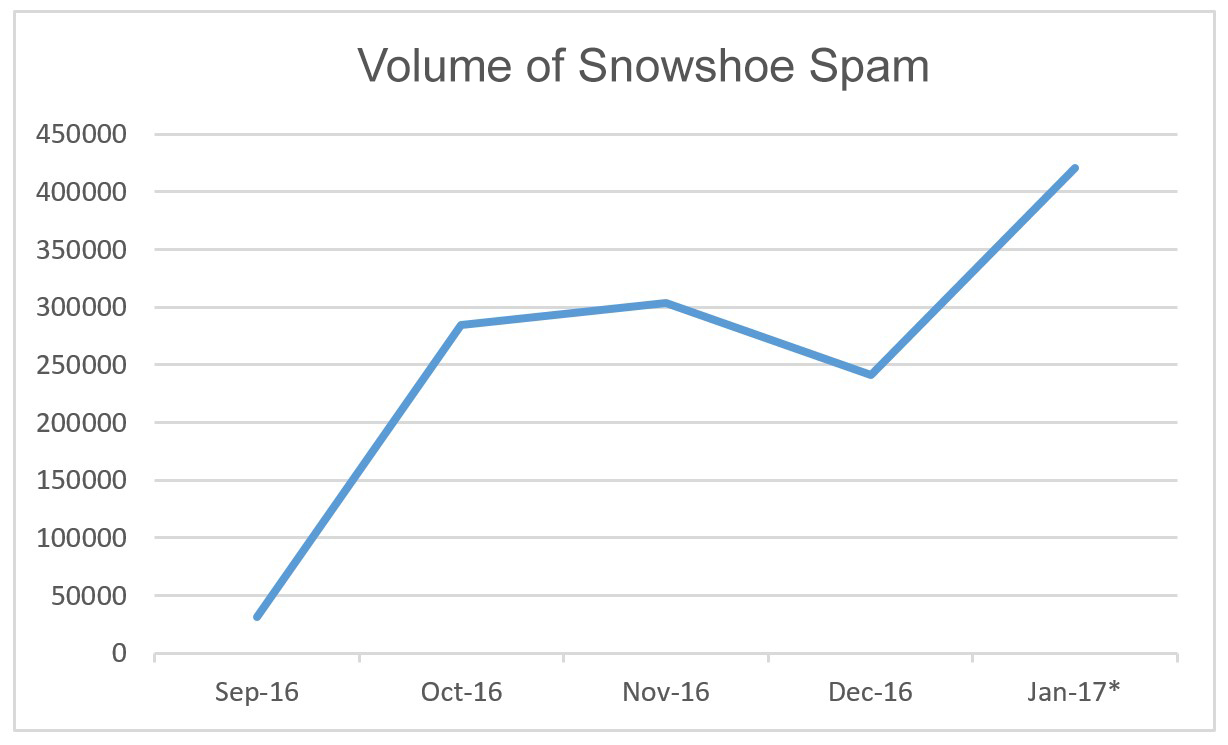
Curiously, since the beginning of the year the amount of spam has gone through the roof! And after studying its structure and style, it looks like most of it comes from one (1) source! Almost all the messages were in English (with just two in Japanese), and – main thing – 100% of this spam was detected by our products! I turned to our specialists… – and it was confirmed: it was a huge tsunami-like wave of a specific type of spam – snowshoe spam. This is unusual as normally around New Year spam activity falls in volume.
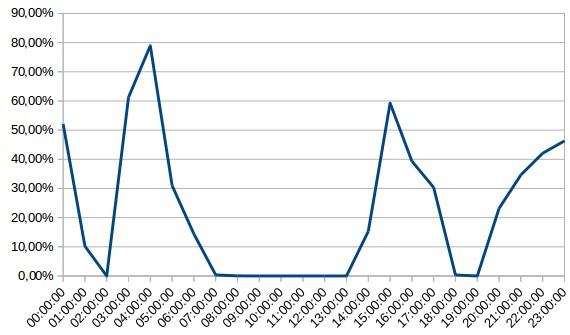
And here’s the data on how the share of snowshoe spam changed on the most active day – January 7 – in the inboxes of our corporate domain:
So just what is this snowshoe when it’s at home, and how can it be protected against?
The snowshoe method isn’t new at all; we first detected it in early 2012. But ever since then it’s been getting bigger and bigger, because it easily fools idiotic spam filters that don’t do multi-level analysis. It does this by being sent not from just one or two IP addresses, but a great many of them, thus getting round IP-address filtration based on reputation. Incidentally, this is where it gets its name from: the weight of a person wearing snow shoes gets distributed evenly over the whole – wide – area of the shoes and causes the person not to slip into the snow. Well, the same principle applies to this spam, kinda: spam distributed widely across many IP addresses causes the spam to not get caught up in filters.
For the spammers, using multiple IP addresses is more complicated, but it gets them the result they want. They have to constantly use auto-generated domains and their providers (usually using a dictionary) and shut down blown hosting and spam proxies. Yes, the fiddles are many and complex, but, like I say, for the spammers it’s worth it.
Once the spam gets to its recipients, social engineering takes over. This starts out with an eye-catching subject text, while in the body of the email there’s a redirect to a site where the respective super-essential product or service is hawked, which you simply cannot let pass you by – and whose sale price ends tomorrow. Miracle cures, once-in-a-lifetime discounts on insurance, impotence pills, utility bills… you name it :-). All sprinkled with a healthy dose of classic con tricks: sob stories (I’m very sick, and have no money), happy endings (I tried this pill here priced at $29.99, and all my symptoms disappeared in a flash!), and so on.
The redirects take you to a site depending on your region. For example, if a user turns up from a very poor country, they simply get redirected to, say, Google. But if a user turns up from a developed country, say, in Europe or North America, then the scam-resource goes into overdrive and comes up with all manner of tales about… the medicinal heritage of the Apache, or Tesla’s mysteries.
But it’s not only crafty social engineering that’s used. This kind of spam can also bring malware along for the ride…
So what about protection?
From the technical standpoint, snowshoe, of course, isn’t all that sophisticated. But that doesn’t mean it shouldn’t be taken seriously. Simple filters unable to adapt to the polymorphism of the spam simply let it through. And there’s no single technology that’s able to deal with snowshoe once and for all. We fight snowshoe with multi-level protection, with first fiddle being played by machine learning. This is logical, since tackling the high volumes of snowshoe spam manually would be simply unrealistic; far better for experts to spend their time on something more useful. And that ‘something more useful’ happens to be creating smart machines, which in turn automatically and extremely accurately and reliably analyse spam and create countermeasure algorithms. For example, thanks to machine learning our products automatically recognize and block new spammer domains, IP addresses and subnetworks, and conduct content-analysis based on various attributes. And they do all of it, as already mentioned, very successfully.
In fact, the war between cyber-good and cyber-evil long ago turned into a war of algorithms. The bad guys learned how to skillfully disguise and alter the appearance/nature of their cyberattacks, and this itself is increasingly done automatically too, resulting in attacks carried out as per complex logic. But for every algorithm, there’s a counter-algorithm, what’s more – a longer one :-). Today, effectiveness depends on the flexibility and reliability of the self-learning systems created by experts. And success goes to those able to provide a combination of (i) the mathematical abilities of man, and (ii) complex infrastructure that permits developing new algorithms. And we call that combination Humachine Intelligence.