June 30, 2014
Cybernews from the dark side: June 30, 2014
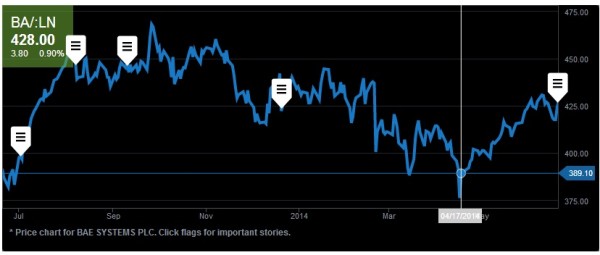
Stock market hacks for microsecond delays.
Cyber-swindling gets everywhere. Even the stock market. First, a bit of history…
The profession of stockbroker was once not only respected and honorable, but also extremely tough. Dealers in stocks and shares once toiled away on the packed floors of stock exchanges and worked silly hours a week, stressed to the limit by relentless high pressure decisions all day (and night). They bought and sold securities, stocks, bonds, derivatives, or whatever they’re called, always needing to do so at just the right moment while riding the waves of exchange rates and prices, all the while edging nearer and nearer to serious heart conditions or some other burn-out caused illness. Other times they simply jumped out of windows to bring a swift end to it all. In short – hardly the world’s best job.
Anyway, all that was long ago. All that hard manual labor has been replaced by automation. Now thinking hard, stressing and sweating aren’t needed: a large proportion of the work today is carried out by robots – special programs that automatically determine the very best moments to buy or sell. In other words, the profession of stockbroker has in large part been boiled down to the training of bots. And to these bots reaction times – to the microsecond – are vital to take advantage of this or that market swing. So speed literally depends on the quality of an Internet connection to the electronic stock exchange. That is, the nearer a robot is physically located to the exchange, the higher its chances of being the first with a bid. And vice versa – robots on the periphery will always be outsiders, just as will those not using the very latest progressive algorithms.
These critical reaction times were recently tampered with by unknown cyber-assailants. A hedge fund’s system was infected with malware to delay trading ability by a few hundred microseconds – which can – and probably did – make all the difference between clinching deals and losing them.