First, a bit of rewind/intro…:
100% guaranteed protection doesn’t exist. You probably know that perfectly well by now. Indeed, even the most reliable antivirus sometimes gets bypassed in professional attacks. That’s bad news enough already. What’s even worse news is that inferior antiviruses get bypassed a lot more frequently.
If they want, highly professional criminals can hack into anything; thankfully, such cyber-Moriatys are few and far between. For the most part, cyber-outrages are carried out by common-or-garden programmers who seem to get their right and wrong all mixed up – seduced by greed and thinking they can get away with it (ha!). These chancers usually don’t have sufficient criminal cyber-skills to pull off hacking the most advanced mega-defenses out there, but they are more than capable of getting into computers that are either not protected at all or which have colander-protection installed. And, alas, such comps in the world are twenty a penny.
The basic logic of it all is rather straightforward:
The stronger the protection – the stronger the defenses, obviously. At the same time, the more professional the attack – the stronger the defenses it can break.
Now, with 2.5 billion Internet users potential victims out there, this logic leads to the following economics:
Criminals don’t need to go to all the bother of coming up with super-mega skeleton keys for breaking into super-mega secure vaults (especially when what is often saved in such super-mega secure vaults can be some real creepy/weird/dangerous stuff it’s best not to know about). It’s much simpler – cheaper – to break into something more down-to-earth, like a neighbor’s network, since their defenses are bound to be much, much lighter, and their stashes more realizable.
So you get the picture: for the average hacker, there’s no point going to the trouble of preparing for and carrying out mega-professional attacks. Nor is there much sense in switching their criminal focus from Windows to Mac. It’s much more effective to ‘carpet-bomb’ – affecting as many victims as possible with non-pinpointed attacks that don’t take a lot of hassle or brains to carry out.
The better the protection – the less interesting it is for the bad guys. They won’t bother going to the trouble of breaking it, they’ll just find other – more vulnerable – victims elsewhere.
Now, let me tell you more about a feature that puts cybercrims off attacking particularly your comp, and has them decide to go elsewhere where the feature doesn’t reside. Yep, it’s time for another eye-opening excursion under the hood of our antivirus and to let you know more about how the letter K in your taskbar makes you a big turn-off to the cyber-trespassers – through protection from future threats with emulation.
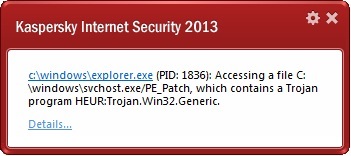
More: The nearly-perfect testing tube…
 Another year, another beer
Another year, another beer