Hi all!
D.Z. – this is one of most distinguished and respected KLers, with us since last century (taking a brief creative break in the mid-2000s). D.Z. has also been my fellow traveler a d.z.illion times to… oh, practically everywhere on this planet – but surprisingly not to Singapore. He always takes with him a trusty large black (super-duper) DSLR camera with a dozen or so different lenses too – his tools to create most of the pro-level pics on this here blog and elsewhere. He’s also a great storyteller, so he helps out with all the tales I want to tell – whatever they may be about. Still, despite all these talents, plus his confirmed KL-Establishment member status, he is nevertheless the most modest guy you’d ever meet.
 Mr. modest… et moi (1999)
Mr. modest… et moi (1999)
Like I say, somewhat surprisingly this was D.Z.’s first visit to Singapore. He liked the place so much he took more pics than he normally does and wrote a long write-up too. It’s true that there’s ‘nothing like the first time’. It’s also true that a fresh pair of eyes will see things in a foreign place that others who’ve been several times before already miss due to familiarity – or just plain tiredness from the non-stop globetrotting. Thus, in this post, I pass the reins over to D.Z. to let him give his ‘first-time’ account of this remarkable city – just for a different, fresher perspective.
My only comment to the story: want one book to read to get the real real deal on Singapore? Check it: Lee Kuan Yew – ‘From Third World to First‘
So, D.Z.’s tale:
—-8<—-
What do we know about Singapore?
It’s a long way away, hot and humid, skyscraping, totalitarian, and they beat you with sticks for dropping gum, spitting, walking barefoot, and other carnal sins. At least, those are the stereotypes impressions of I’d say the majority of non-Singaporeans from afar, for those are the bits that seem to end up in the world’s media about this city-state extraordinaire.
This was my first time in Singapore.
What I saw with my own eyes was far from what I expected – nothing like the above-described imaginings. I have habit of boning up on a country I’m planning on traveling to – to get to know the ‘real’ place and not get caught up in lazy stereotypes and maybe inadvertently insult or upset or annoy anyone. And Singapore’s real deal fairly amazed and intrigued me. The first half of the 19th century is packed with curious history I’d let pass me by, but it’s fascinating how it’s connected with all sorts of details of international relations of my time.
Collisions of civilizations, a struggle for colonies and trade routes, the friction within and among European and Asian powers, wars, injustice, betrayal, greed and other unpleasantness… Singapore had more than its fair share of all of them. Its history is peppered with nightmare tales, but all the same, in spite of all that, today it stands as the shining example of a successful state based on humane, productive cooperation among peoples, helped by being at an important crossroads of civilization.
A natural competitive advantage of Singapore is its geographical location on a strategic sea route connecting East Asia with the rest of the world. Despite miraculous diversification of the economy in its 50 years of independence, already on the approach to Changi airport it becomes clear how this advantage still plays a hugely important role in the development of the country.

Back in 1819 it was exclusively the geography of the island that made Britain’s Sir Stamford Raffles set up on the bank of the Singapore River a watch post. Within just several years it had become an important hub of influence of the British Empire in Asia.
Singapore was founded not on an empty greenfield site but on a longstanding fishing village in which folks of different nationalities and religious faiths had lived peacefully for a long time. The arrival of the British naturally saw the town take on a decidedly more European flavor. And, talking of flavors, incidentally the resultant Singaporean cuisine came to be a most interesting and original one – the dishes both tasty and unique.
Having founded Singapore, Raffles left it for a few years to do yet more of his bit for the Empire, handing over the reins to a Major-General William Farquhar for the duration. Upon Raffles‘ return three years later, he was met with two main developments – basically good news and bad. The good news was that the town had gotten much busier and bigger. The bad – it had gotten much busier and bigger un-systemically, resembling an eastern bazar than an exemplary model of a colony of the British Empire.
So a town council was quickly created under the supervision a Lieutenant Jackson, who soon developed a plan for the reconstruction of Singapore. In the main, it was divided up based on the ethnicity of the inhabitants; thus, European, Chinese, Indian, and Arab (Muslim) quarters emerged.
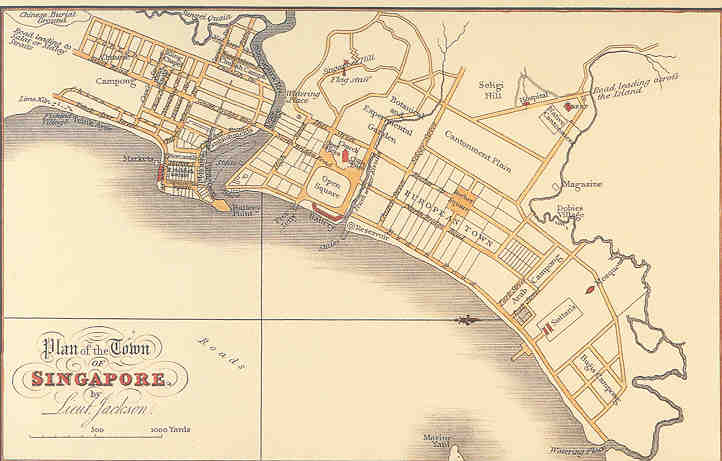
It might seem correct at this point to label Jackson an out and out racist and accomplice in apartheid. However, it turned out that such division suited everyone just fine! Each group was happy to cook in its own juices – yet still work closely together; indeed, they’d be doing so for centuries before Raffles. Since then of course, in almost in 200 years, a lot has changed; all the same the main traits of the town-building designs of Jackson remain.
Singapore has two principal must-visits – Little India and Chinatown. Guess which ethnic nationalities make up most of their populations? Yep – Indians and Chinese, respectively, even after all these years. In fact the delineation is blurring somewhat, with many an Indian and much Indian signage to be seen in Chinatown, and vice versa. The result is a serious bit of multiculturalism: Pagodas, stupas, mandirs (Hindu temples), mosques and churches all together peacefully coexisting on small squares. Nice. All the same, the dominating cultural ‘signature’ of the districts remains.

Read on: Chinatown vs Little India…