If you’re a regular reader of this here blog of mine, you’ll know about our GReAT (Global Research and Analysis Team) – 40+ top-notch cybersecurity experts dotted all around the globe specializing in protecting our customers from the most sophisticated cyberthreats out there. GReATers like to compare their work to paleontology: exploring the deep web for the ‘bones’ of ‘cyber monsters’. Some may consider this an old-fashioned approach: what’s so special about analyzing the ‘bones’ of ‘creatures’ from the distant past when it’s protecting your networks from monsters that are alive now that’s key? Well, here’s a fresh story that proves that sometimes you won’t find today’s living monsters without looking at old ones…
Some of you will be aware of so-called wipers – a type of malware which, once installed on an attacked PC, completely wipes all data from it – leaving the owner of the computer with a completely clean, hardly operating piece of hardware. The most famous (and infamous) wiper is Shamoon – malware which in 2012 made a lot of noise in the Middle East by destroying data on 30,000+ endpoints at the world’s largest oil company – Saudi Aramco, and also hitting another energy giant – Rasgas. Just imagine: 30,000+ pieces of inoperable hardware in the world’s largest oil company…
Shamoon, Shamoon 2.0, StoneDrill, Newsbeef. The wipers are spreading across the globe
Curiously, since it’s devastating campaign against the Saudi company in 2012, little has been heard of Shamoon, until it returned in 2016 as Shamoon 2.0, with several new waves of attacks – again in the Middle East.
Since the new waves of Shamoon attacks began, we’ve been tuning our sensors to search for as many versions of this malware as possible (because, let’s face it, we don’t want ANY of our customers to EVER be struck by malware like Shamoon). And we managed to find several versions – hurray! But together with our haul of Shamooners, our nets unexpectedly caught a completely new type of wiper malware, which we’ve named StoneDrill.
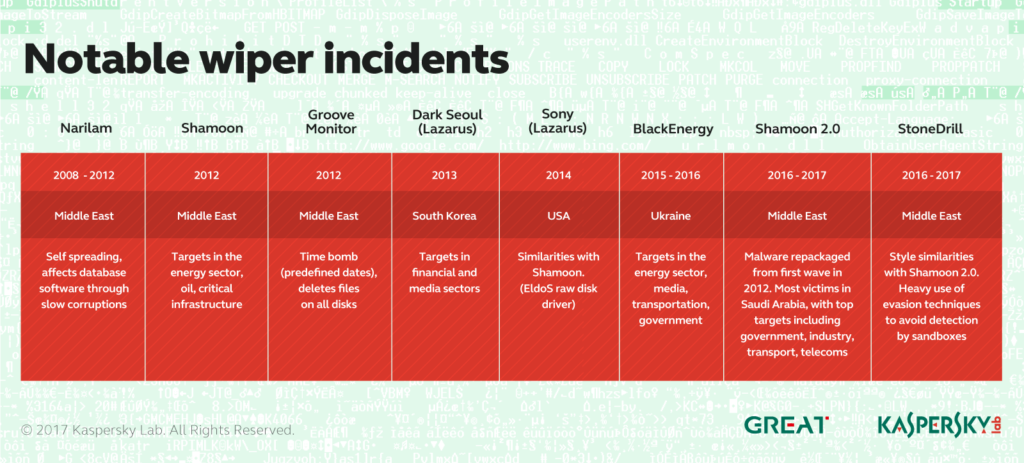
The code base of StoneDrill is different to that of Shamoon, and that’s why we think it’s a completely new malware family; it also utilizes some advanced detection avoidance techniques, which Shamoon doesn’t. So it’s a new player, for sure. And one of the most unusual – and worrying – things we’ve learned about this malware is that, unlike Shamoon, StoneDrill doesn’t limit the scope of its targets to Saudi Arabia or other neighboring countries. We’ve found only two targets of this malware so far, and one of them is based in Europe.
Why is this worrying? Because this finding indicates that certain malicious actors armed with devastating cyber-tools are testing the water in regions in which previously actors of this type were rarely interested.
Read on: more wipers!…