July 5, 2022
A Kuarter of a century? Where did that go?!…
Hi folks!
25 years and nine days ago – on June 26, 1997 – the company that happens to have the same name as me was registered. And it was “humble beginnings” in the truest sense: around a dozen folks with zero turnover – but with some special tech-expertise and some equally special and veeeery ambitious plans. And we looked something like this:
Fast-forward two years to 1999 and there’s already around 40 of us ->

And that’s how it all started. // Btw: you can find out more details about our history here.
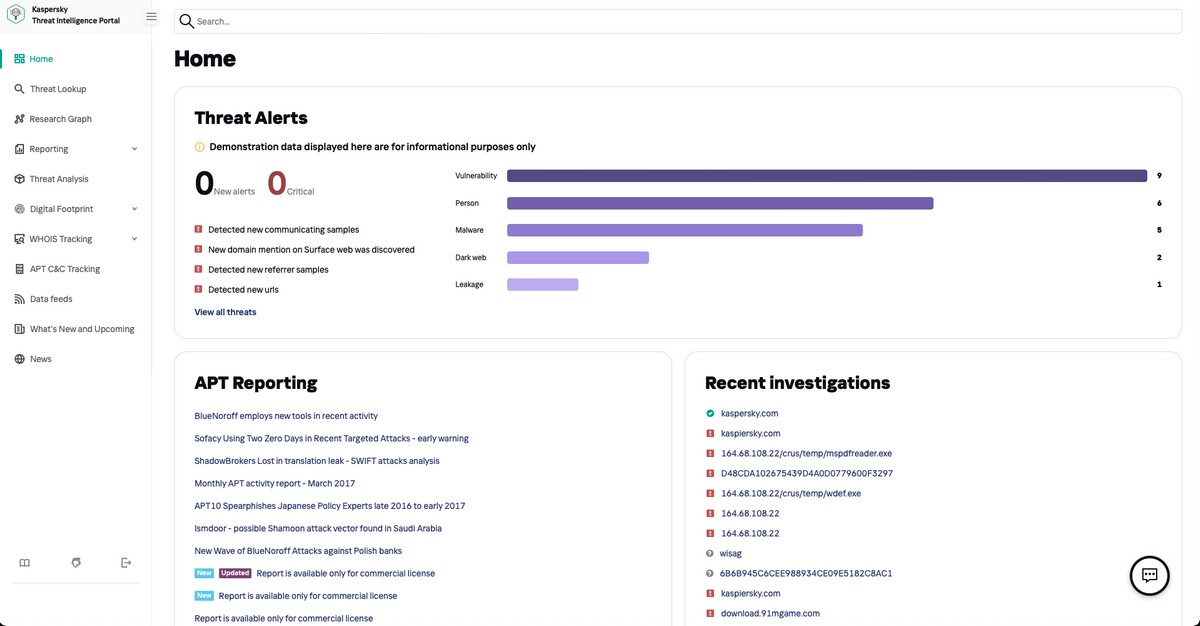
Twenty-five years – a quarter-century! – doing some great work! Based on our own world-beating antivirus engine, we developed breakthrough internet security products for home users. It didn’t always go smoothly, but we got there! There was our Ver. 6 – remember that? (And what a grandiose tale there is to tell there:) Then we gradually moved into the enterprise market, managing to develop some great products there too: first in the endpoint category, and then also network-traffic control, protection against targeted attacks and so on. Then we turned to protecting industrial objects. And now (without being too modest), I can say we’re the only company in the world that provides such a broad range of top-notch cyber protection: for user devices, workstations, server infrastructure and network traffic, as well as industrial control systems like SCADA. Moreover, we cover the widest range of operating systems and device types.