February 2, 2022
For cyber-insurance – a watershed moment (involving a $1.4bn payout!)
Hi boys and girls!
It’s been a while since my last installment of iNews, aka – uh-oh cyber-news, aka – cyber-tales from the dark side, so here’s reviving the series to get back on track in giving you highlights of jaw-dropping cyber-astonishments you might not hear about from your usual sources of news…
In this installment – just one iNews item for you, but it’s plenty: an added item might have watered down the significance of this one (hardly appropriate when there’s ‘watershed’ in the title:)…
Briefly about the iNews: after lengthy legal proceedings in the U.S., a court has ruled in favor of big-pharma company Merck against its insurer for a payout of US$1.4 billion (!!) to cover the damages Merck suffered at the grubby hands of NotPetya (aka ExPetr or simply Petya) in 2017.
Quick rewind back to 2017…
In June of that year, all of a sudden a viciously nasty and technologically advanced encryptor worm – NotPetya – appeared and spread like wildfire. It initially targeted Ukraine, where it attacked victims via popular accounting software – affecting banks, government sites, Kharkov Airport, the monitoring systems of the Chernobyl Nuclear Power Plant (!!!), and so on and so on. Next, the epidemic spread to Russia, and after that – all around the world. Many authoritative sources reckon NotPetya was the most destructive cyberattack ever. Which looks about right when you count the number of attacked companies (dozens of which each lost hundreds of millions of dollars), while overall damage to the world economy was estimated at a minimum 10 billion dollars!

One of the most notable victims of the global cyberattack was the U.S. pharmaceuticals giant Merck. It was reported 15,000 of its computers were zapped within 90 seconds (!) of the start of the infection, while its backup data-center (which was connected to the main network), was lost almost instantly too. By the end of the attack Merck had lost some 30,000 workstations and 7,500 servers. Months went into clearing up after the attack – at a cost of ~1.4 billion dollars, as mentioned. Merck even had to borrow vaccines from outside sources for a sum of $250 million due to the interruptions caused to its manufacturing operations.
Ok, background out the way. Now for the juiciest bit…
The policy-contract between Merck and the insurance company Ace American covered all risks, including loss of data related to the use of software. Those risks were insured for 1.75 billion dollars. Ace American, however, refused to recognize the NotPetya ransomware-virus attack as a covered loss and thus wouldn’t pay out: it had the attack down as force majeure. To back this up they said that Russia was to blame for the creation of NotPetya, which, it said, had used it as a cyberweapon in the war against Ukraine, and the insurer wasn’t obligated to indemnify the insured for damages caused by military actions. In turn, to back this up, it cited the announcements made by the governments of the UK and the U.S., both of which had long ago officially blamed Russia for this cyberattack.
In 2019 Merck took its insurer to court, asserting that the attack was not the official action of a nation state and, as such, cannot be deemed military action or armed conflict. Merck’s lawyers also pointed out how cyberattacks were not specified in the insurance-cover exceptions section of the policy. In the end, the court ruled in Merck’s favor, noting that Ace American knew that cyberattacks can be recognized military actions, but chose not to specify this in the insurance policy.
I think that many insurance companies will have been following this case closely, and will now be going over the wordings of their standard policies with a fine-tooth comb. Meanwhile, from the other side, I’m sure plenty of victims of countless cyber-incidents will similarly be reviewing the terms of their insurance agreements to see if they may be due a payout too based on this here precedent of Merck’s. But it should be clear to both the insured and insurers that they need to be mindful of the long-term effect: if the ‘rules of the game’ are changed too markedly, significant increases in insurance premiums look inevitable.
As I don my fortune-telling cyber-wizard’s hat, it seems to me that insurance against cyber-risks will become veeery big business – to an almost unbelievable extent: a direct mapping of traditional insurance practice onto cyberspace without guarantees (on levels of protection against cyber-risks) of cybersecurity vendors could significantly – if not irreparably – damage the whole insurance sector. However, most cybersecurity companies today guarantee protection against, for example, just 50% of ransomware – ransomware like NotPetya.
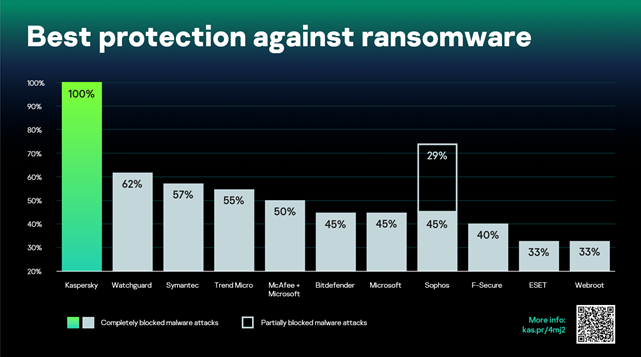
50%? But, that’s like… instead of proper security for a building – cameras, security guards, etc. – simply having a sign above the front door saying: ‘Enemies not allowed in’! You need 100% protection or nothing. Oh, and, against ransomware, just one company provides 100% protection. Guess which!
So, we get a situation here where there are risks of cyberattack, and they’re massive, and this means companies want to insure these risks together with all other risks. At the same time, any normal, sober insurer, seeing that bill there for $1.4 billion, will try its best to make sure cyber-risks aren’t specified in their insurance policies. Which gives us an absolutely revolutionary situation: the insurance companies don’t want to insure cyber-risks, even though their customers want cyber-risk insurance real bad.
So what’s to be done? Clearly, there’s a need to lower the risks of attacks on digital infrastructure. That is, to build it in such a way that the most critical and vulnerable segments are maximally immune against external (and internal) attacks, while all the rest is protected by multiple layers of security of guaranteed resilience. Oh da.
Science fiction? Not in my opinion, but that’s a whole other story ).


