September 12, 2013
K-LOVE & KISSES 2014 – PART 1.
Hip, hip, hurray! Yee ha! Woo hoo! The latest incarnation of KIS has landed – everywhere (almost)!
As per our long held tradition of launching new kit during the summer months – we’ve now managed to get KIS 2014 officially released in all the main regions of the world and in all the most widely spoken languages. For those interested in KIS itself, go here to download the new version. Upgrade guidelines are here.
And as is also becoming a bit of a tradition early fall, the time has come for me to tell you all what’s in this here new version…
First thing I can say: new stuff – there’s plenty of it. So much so that there’ll be several posts covering the key new features separately, as the low-down on all of them won’t fit into one bite-sized blogpost that won’t send you to sleep…
So, here we go… with post No. 1:
Basically, KIS 2014 packs yet more punch than its already punchy predecessor – KIS 2013 – which even without all this year’s additions was unlucky for no one. The protection provided is harder, better, faster, stronger. KIS has gone under the knife for a nip and tuck complete face-lift of its interface, and the logic of its main operations has been overhauled too.
There are new features to ensure secure online money operations (we’ve beefed up Safe Money); there are new features in Parental Control; there’s integrated protection against malicious blockers; and there are various new performance accelerators and optimizers to make the protection even more invisible and unobtrusive.
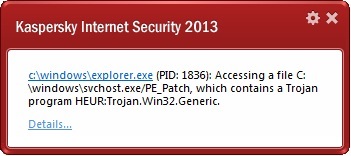
But the best feature of all in this version is what we put most effort into: providing protection from future threats, having added to the product – much to the chagrin of cyberswine – several specialized avant-garde technologies (none of which appears to be included in competitors’ products). No, we haven’t used a time machine; nor did we track down cyberpigs and do a Jack Bauer interrogation on them to get to know about their planned mischief. We shamanized, looked into the future, came up with rough calculations of the logic of the development of cyber-maliciousness, and transferred that logic into practice in our new technologies of preventative protection.
Among the preventative measures against future threats I’d like to emphasize the souped-up Automatic Exploit Prevention – two special technologies from our corporate solutions that have been adapted for our home products – ZETA Shield and Trusted Applications mode, plus a built-in proactive anti-blocker.
So how do all these fancy sounding features actually help in daily computer hygiene? Let me start by telling you first about Trusted Applications mode – the world’s first for such technology being featured in a home product providing complex security.