March 4, 2019
Cyber-news from the dark side: Japanese legal hacking; iKeychain hack; 2FA -> $0; an Iranian cyber-whodunit; and a USB-eating leopard seal.
Privyet boys and girls!
Herewith, the next in my periodic/occasional cyber-news cyber-shocker-bulletins: a few stories of the cyber-interesting, the cyber-this-news-just-in, and the cyber-absurd…
State-sanctioned hacking!
The Japanese government is believed to be planning to hack 200 million IoT devices of its citizens. And that’s not science fiction folks; it looks like it’s for real. Indeed, it’s how the Japanese are preparing for the Olympics to be held in Tokyo in 2020 – and it’s all legal of course, since it’s the government who’s behind it. So their citizens’ gadgets will be hacked using the cybercriminals favorite method: using default passwords and password dictionaries. If a device is found to have a weak password, bureaucrats will enter the device into a list of unsecure gadgets, which list will then be handed over to internet service providers, which will be expected to inform subscribers and have them make their devices secure by changing the password. It’s all being done as a resilience test in the run-up to the Olympics, to work out if IoT devices in the country are sufficiently protected, and to try and prevent their use in attacks on the Olympics’ infrastructure. The methods to be used for this ‘test’ can easily be disputed, but the fact that the authorities are doing something concrete so well in advance is certainly a good thing. For let’s not forget that the Olympics have been targeted before – and not all that far away from Japan.
iOops!
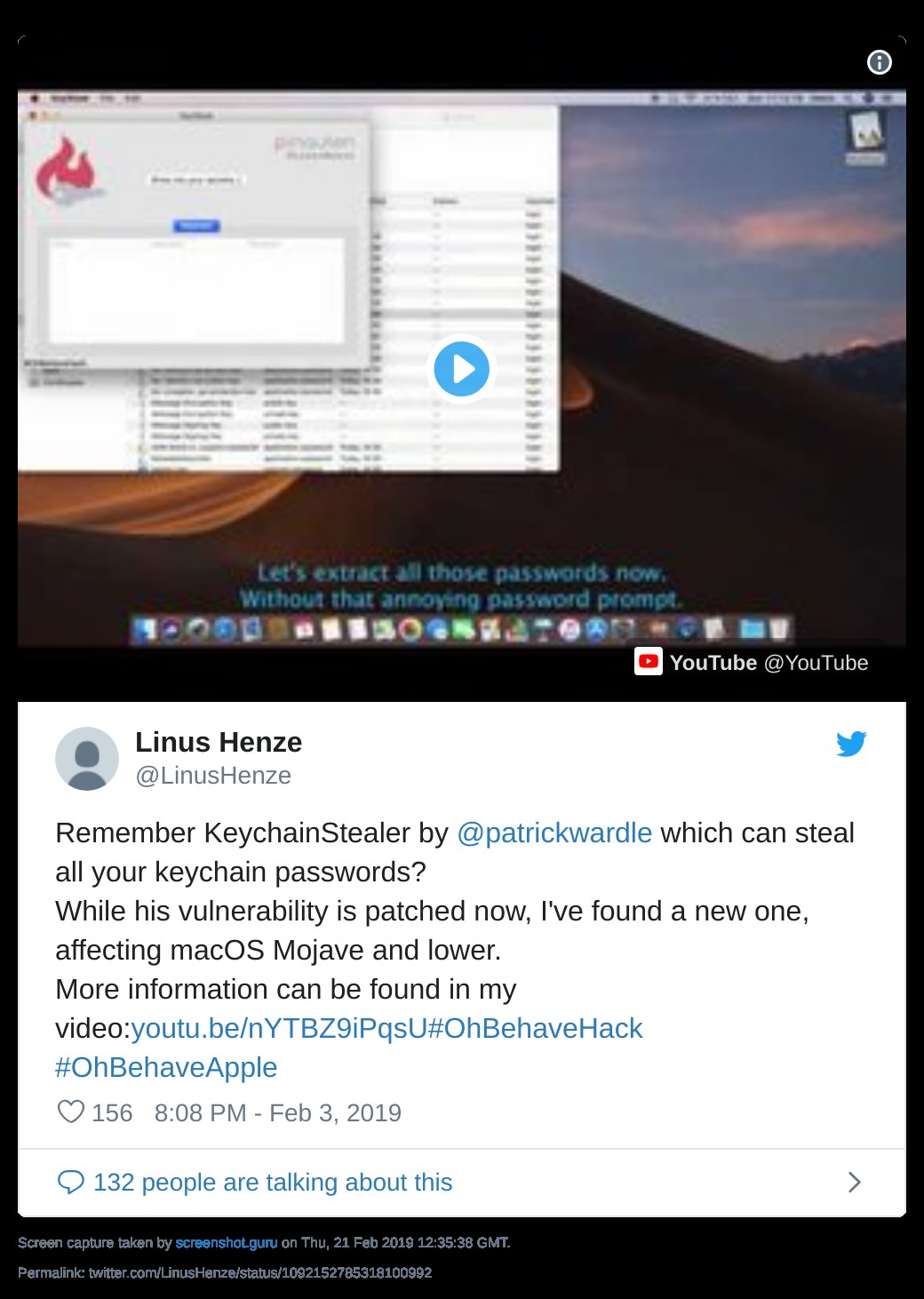
An 18-year-old hacker, Linus Henze, has published a video highlighting a startling weakness in MacOS – specifically its Keychain program, which stores and secures a user’s many passwords. The teenager used a zero-day to develop his own app that can scan the full contents of the keychain.
Curiously, intriguingly, Mr. Henze isn’t planning on sharing his research and his app with the tech giant, since Apple still doesn’t run a bug-bounty program. So that leaves the company with two options: negotiate with the expert (which would be an unprecedented move for Apple), or consider trying to remedy the issue themselves – which they may or may not be able to do, of course.
Meanwhile, you, dear readers, need not fear for the safety of your passwords! Since there do exist (who’d know?!) fully secure, cross-platform password managers out there. And researchers – there do exist software companies that run bug-bounty programs ).
Even two-factor authentication can be hacked now.
Bank accounts being emptied by cyber-thiefs is on the up. One example recently involved accounts held at the UK’s Metro Bank. And the method used for the robberies involved intercepting text messages sent to account-holders’ phones for two-factor authentication. Now, 2FA is a good thing: it’s an extra layer of security and all that, so why not? It’s just that SMSs are by far not the most secure way to transfer data. For example, vulnerabilities can be exploited in the SS7 protocol, which is used by telecoms operators the world over to coordinate how they route texts and calls. If cyber-baddies manage to access the mobile network of an operator, they’re able to re-route messages and calls without the user being any the wiser. First they’d need to know your login and password for online banking, but that isn’t beyond the abilities of modern-day cyber-villains with their crafty keyboard spies, phishing tactics, or banking Trojans.
Once inside the online bank, the criminals send a request for a money transfer and intercept the message with the one-time code from the bank. The code is entered, and the bank transfers the funds, since both the password and the code were correctly entered. And the criminals are laughing all the way to the bank, as it were ).
So what can you do to stop such a scenario happening to you? Here are a couple of tips:
- Never tell anyone your login or passwords – even to a bank employee, but you’ll probably know that one: banks helpfully remind us whenever they can.
- Protect your devices from malware with a reliable antivirus app. There is one I happen to know of… but no – you choose the one you want ).
Cyber-spying on foreign diplomats in Iran – but whodunit?
Our researchers just recently discovered multiple attempts at infection of foreign diplomatic missions in Iran with some rather primitive cyber-espionage malware. The backdoor is presumed to be associated with the hacking group know as Chafer, which happens to ‘speak’ Farsi, and which is thought to have been responsible for cyber-surveillance on individuals in the Middle East in the past. This time, they cybercriminals used an improved version of the Remexi backdoor, designed to remotely control (as administrator) a victim’s computer.
Remexi software was first detected in 2015 when it was used for illegal surveillance of individuals and organizations across the whole region. The Windows-targeting surveillance-ware can exfiltrate keystrokes, screenshots, and browser-related data like cookies and history.
Much ‘home made’ malware is used in the region – often in combination with public domain utilities. But who’s behind these particular attacks? Finding out is made all the more difficult by the very fact that the malware is homespun; it literally could be anybody: Iranians, or non-Iranians pulling a false-flag operation. Alas, false flags are on the up and up and look set to remain so.
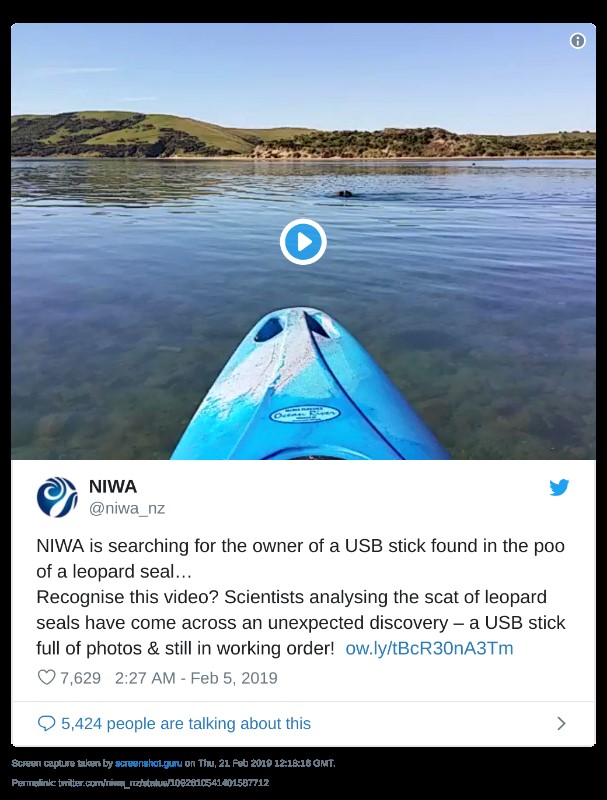
“Well, actually… a seal ate my USB stick, sir.”
In New Zealand, one day out walking a vet observed a clearly unwell leopard seal on a beach. As any concerned vet would, he proceeded to… scoop up a lump of the poorly seal’s poop and took it off for analysis. He was expecting to find therein some ghastly little parasites or viruses or what have you, but instead found… a USB stick. After much disinfection (I hope), the vet stuck the thumb drive into his computer (don’t try any of this at home kids, but this was a special case). And guess what? Thereon were stored lots of photos of the beautiful New Zealand scenery! Now the vet and Co. are seeking the owners of the USB – using this here video. Recognize it, anybody?