Every now and again (once every several years or so), a high-profile unpleasantness occurs in the cyberworld – some unexpected new maliciousness that fairly bowls the world over. For most ‘civilians’ it’s just the latest in a constant stream of seemingly inevitable troublesome cyber-surprises. As for my colleagues and me, we normally nod, wink, grimace, and raise the eyebrows à la Roger Moore among ourselves while exclaiming something like: ‘We’ve been expecting you Mr. Bond. What took you so long?’
For we’re forever studying and analyzing the main tendencies of the Dark Web so we can get an idea of who’s behind its murkiness and of the motivations involved; that way we can predict how things are going to develop.
Every time one of these new ‘unexpected’ events occurs, I normally find myself in the tricky position of having to give a speech (rather – speeches) along the lines of ‘Welcome to the new era‘. Trickiest of all is admitting I’m just repeating myself from a speech made years ago. The easy bit: I just have to update that old speech a bit by adding something like: ‘I did warn you about this; and you thought I was just scaremongering to sell product!’
Ok, you get it (no one likes being told ‘told you so’, so I’ll move on:).
So. What unpleasant cyber-unexpectedness is it this time? Actually, one affecting something close to my heart: the world of automobiles!
A few days ago WIRED published an article with an opening sentence that reads: ‘I was driving at 70 mph on the edge of downtown St. Louis when the exploit began to take hold.‘ Eek!
The piece goes on to describe a successful experiment in which hackers security researchers remotely ‘kill’ a car that’s too clever by half: they dissected (over months) the computerized Uconnect system of a Jeep Cherokee, eventually found a vulnerability, and then managed to seize control of the critical functions of the vehicle via the Internet – while the WIRED reporter was driving the vehicle on a highway! I kid you not folks. And we’re not talking a one-off ‘lab case’ here affecting one car. Nope, the hole the researchers found and exploited affects almost half a million cars. Oops – and eek! again.

However, the problem of security of ‘smart’ cars is nothing new. I first ‘joked’ about this topic back in 2002. Ok, it was on April 1. But now it’s for real! You know what they say… Be careful what you wish for joke about (there’s many a true word spoken in jest:).
Not only is the problem not new, it’s also quite logical that it’s becoming serious: manufacturers compete for customers, and as there’s hardly a customer left who doesn’t carry at all times a smartphone, it’s only natural that the car (the more expensive – the quicker) has steadily been transformed into its appendage (an appendage of the smartphone – not the user, just in case anyone didn’t understand me correctly).
More and more control functions of smart cars are now firmly in the domain of the smartphone. And Uconnect isn’t unique here; practically every large car manufacturer has its own similar technology, some more advanced than others: there’s Volvo On Call, BMW Connected Drive, Audi MMI, Mercedes-Benz COMAND, GM Onstar, Hyundai Blue Link and many others.
More and more convenience for the modern car-driving consumer – all well and good. The problem is though that in this manufacturers’ ‘arms race’ to try and outdo each other, critical IT security matters often go ignored.
Why?
First, the manufacturers see being ahead of the Jones’s as paramount: the coolest tech functionality via a smartphone sells cars. ‘Security aspects? Let’s get to that later, eh? We need to roll this out yesterday.’
Second, remote control cars – it’s a market with good prospects.
Third, throughout the auto industry there’s a tendency – still today! – to view all the computerized tech on cars as something separate, mysterious, faddy (yep!) and not really car-like, so no one high up in the industry has a genuine desire to ‘get their hands dirty’ with it; therefore, the brains applied to it are chronically insufficient to make the tech secure.
It all adds up to a situation where fancy motorcars are becoming increasingly hackable and thus stealable. Great. Just what the world needs right now.
What the…?
Ok. That’s the basic outline. Now for the technical background and detail to maybe get to know what the #*@! is going on here!…
Way back in 1985 Bosch developed CAN. No, not their compatriot avant-garde rockers (who’d been around since 1968), but a ‘controller area network’ – a ‘vehicle bus’ (onboard communications network), which interconnects and regulates the exchange of data among different devices – actually, those devices’ microcontrollers – directly, without a central computer.
For example, when the ‘AC’ button on the dashboard is pressed, the dashboard’s microcontroller sends a signal to the microcontroller of the air conditioner saying ‘turn on, the driver wants cooling down’. Or when the brake pedal is pressed, the microcontroller of the pedal mechanism sends an instruction to the brake pads to press up against the brake discs.
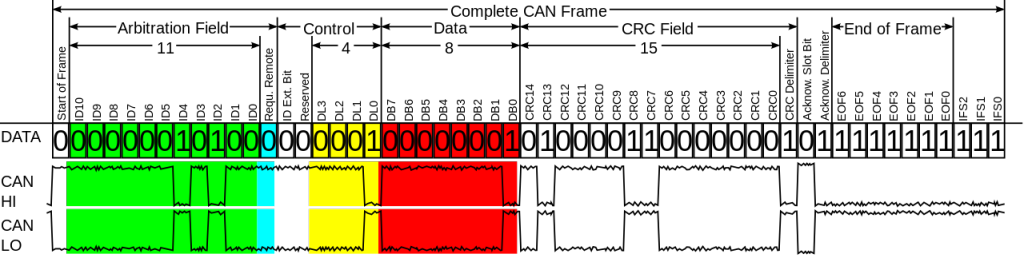
Put another way, the electronics system of a modern automobile is a peer-to-peer computer network – designed some 30 years ago. It gets better: despite the fact that over three decades CAN has been repeatedly updated and improved, it still doesn’t have any security functions! Maybe that’s to be expected – what extra security can be demanded of, say, a serial port? CAN too is a low level protocol and its specifications explicitly state that its security needs to be provided by the devices/applications that use it.
Maybe they don’t read the manuals. Or maybe they’re too busy trying to stay ahead of competitors and come up with the best smart car features.
Whatever the reasons, the fundamental fact causing all the trouble remains: Some auto manufacturers keep squeezing onto CAN more and more controllers without considering basic rules of security. Onto one and the same bus – which has neither access control nor any other security features – they strap the entire computerized management system that controls absolutely everything. And it’s connected to the Internet. Eek!

Just like on any big computer network (e.g., the Internet), cars too need a strict ‘division of trust’ for controllers. Operations on a car where there’s communication with the outside world – be it installation of an app on the media system from an online store, or sending car performance diagnostics to the manufacturer – need to be firmly and securely split from the engine control, the security and other critical systems.
If you show an IT security specialist a car, lots of functions of which can be controlled by, say, an Android app, he or she would be able to demonstrate in no time at all a dozen or so different ways to get round the ‘protection’ and seize control of the functions the app can control. Such an experiment would also demonstrate how the car isn’t all that different really from a bank account: bank accounts can be hacked with specially designed technologies, in their case with banking Trojans. But there is a further potential method that could be used to hack a car just like a bank account too: with the use of a vulnerability, like in the case of the Jeep Cherokee.
Any reasons to be cheerful?…
…There are some.
Now, the auto industry (and just about everyone else) seems to be well aware of the degree of seriousness of the problem of cybersecurity of its smart car sector (thanks to security researchers like those in the WIRED article, though some manufacturers are loath to show their gratitude openly).
A sign of this is how recently the US Alliance of Automobile Manufacturers announced the creation of an Information Sharing and Analysis Center, “that will serve as a central hub for intelligence and analysis, providing timely sharing of cyber threat information and potential vulnerabilities in motor vehicle electronics or associated in-vehicle networks.” Good-o. I just don’t see how they plan to get along without security industry folks involved.
And it’s not just the motor industry that’s now on its toes: hours (!) after the publication of the WIRED article (the timing was a coincidence, it was reported) new federal legislation in the US was introduced establishing standardization of motor industry technologies in the field of cybersecurity. Meantime, we’re hardly twiddling thumbs or sat on hands: we’re actively working with several auto brands, consulting them on how to get their smart-car cybersecurity tightened up proper.
So, as you can see, there is light at the end of the tunnel. However…
…However, the described cybersecurity issue isn’t limited just to the motor industry.
CAN and other standards like it are used in manufacturing, the energy sector, transportation, utilities, ‘smart houses’, even in the elevator in your office building – in short – EVERYWHERE! And everywhere it’s the same problem: the growth of functionality of all this new tech is hurtling ahead without taking security into account!
What seems more important is always improving the tech faster, making it better than the competition, giving it smartphone connectivity and hooking it up to the Internet. And then they wonder how it’s possible to control an airplane via its entertainment system!
https://twitter.com/sidragon1/status/588433855184375808
What needs doing?
First things first, we need to move back to pre-Internet technologies, like propeller-driven aircraft with analog-mechanical control systems…
…Not :). No one’s planning on turning the clocks back, and anyway, it just wouldn’t work: the technologies of the past are slow, cumbersome, inefficient, inconvenient and… a lot less secure! Nope, there’s no going backwards. Only forwards!
In our era of polymers, biotechnologies and all-things-digital, movement forward is producing crazy results. Just look around you – and inside your pockets. Everything is moving, flying, being communicated, delivered and received, exchanged… all at vastly faster speeds to those of the past. Cars (and other vehicles) are only a part of that.
All that does make life more comfortable and convenient, and digitization is solving many old problems of reliability and security. But alas, at the same time it’s creating new problems. And if we keep galloping forward at breakneck speed, without looking back, improvising as we hurtle along to get the very best functionality, well, in the end there are going to be unpredictable – even fatal – consequences. A bit like how it was with the Zeppelin.
There is an alternative – a much better one: What we need are industry standards; new, modern architecture, and a responsible attitude to the development of features – by taking into account security – as a priority.
In all, the WIRED article has shown us a very interesting investigation. It will be even more interesting seeing how things progress in the industry from here. Btw, at the Black Hat conference in Vegas in August there’ll be a presentation by the authors of the Jeep hack – that’ll be something worth following…
Smart cars can be remotely hacked. Fact. Period. Shall we go back to the Stone Age? @e_kaspersky explains:
PS: Call me retrogressive (in fact I’m just paranoid:), but no matter how smart the computerization of a car, I’d straight away just switch it all off – if there was such a possibility. Of course, there isn’t. There should be: a button, say, next to the hazard lights’ button: ‘No Cyber’!…
…PPS: ‘Dream on, Kasper’, you might say. And perhaps you’d be right: soon, the way things are heading, a car without a connection to the ‘cloud’ won’t start!
PPPS: But the cloud (and all cars connected to it) will soon enough be hacked via some ever-so crucial function, like facial recognition of the driver to set the mirror and seat automatically.
PPPPS: Then cars will be given away for free, but tied to a particular filling station network digital network – with pop-ups appearing right on the windscreen. During the ad-break control will be taken over and put into automatic Google mode.
PPPPPS: What else can any of you bright sparks add to this stream-of-consciousness brainstorming-rambling? :)
 Photo courtesy of Wikipedia
Photo courtesy of Wikipedia