December 8, 2021
A paradigm shift for industrial security: immunizing factories.
Ten years is a long time in cybersecurity. If we could have seen a decade into the future in 2011 just how far cybersecurity technologies have come on by 2022 – I’m sure no one would have believed it. Including me! Paradigms, theories, practices, products (anti-virus – what’s that?:) – everything’s been transformed and progressed beyond recognition.
At the same time, no matter how far we’ve progressed – and despite the hollow promises of artificial intelligence miracles and assorted other quasi-cybersecurity hype – today we’re still faced with the same, classic problems we had 10 years ago in industrial cybersecurity:
How to protect data from non-friendly eyes and having unsanctioned changes made to it, all the while preserving the continuity of business processes?
Indeed, protecting confidentiality, integrity and accessibility still make up the daily toil of most all cybersecurity professionals.
No matter where it goes, ‘digital’ always takes with it the same few fundamental problems. ANd ‘go’ digital will – always – because the advantages of digitalization are so obvious. Even such seemingly conservative fields like industrial machine building, oil refining, transportation or energy have been heavily digitalized for years already. All well and good, but is it all secure?
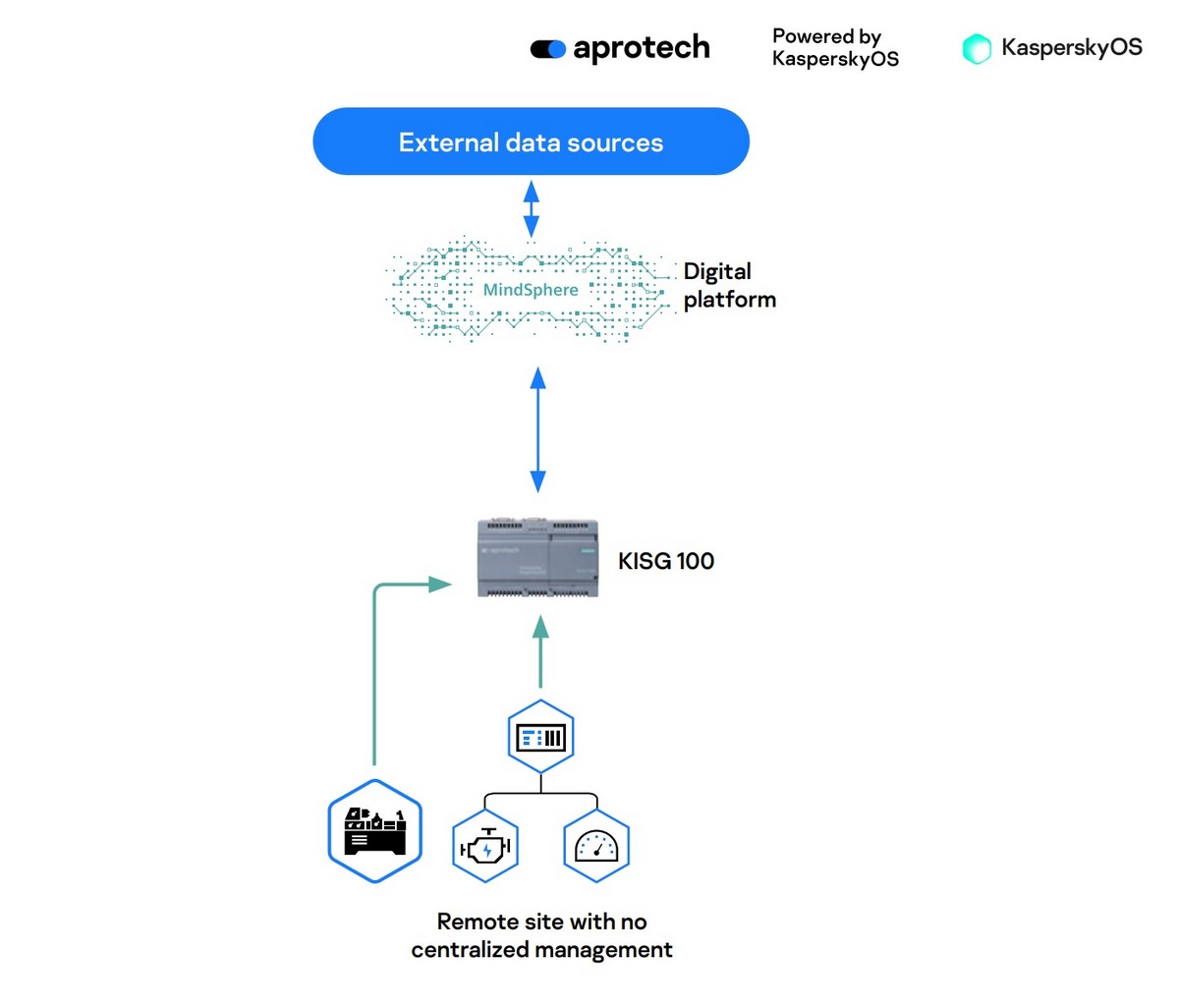
With digital, the effectiveness of business grows in leaps and bounds. On the other hand, all that is digital can be – and is – hacked, and there are a great many examples of this in the industrial field. There’s a great temptation to fully embrace all things digital – to reap all its benefits; however, it needs to be done in a way that isn’t agonizingly painful (read – with business processes getting interrupted). And this is where our new(ish) special painkiller can help – our KISG 100 (Kaspersky IoT Secure Gateway).

This tiny box (RRP – a little over €1000) is installed between industrial equipment (further – ‘machinery’) and the server that receives various signals from this equipment. The data in these signals varies – on productivity, system failures, resource usage, levels of vibration, measurements of CO2/NOx emissions, and a whole load of others – and it’s all needed to get the overall picture of the production process and to be able to then take well-informed, reasoned business decisions.
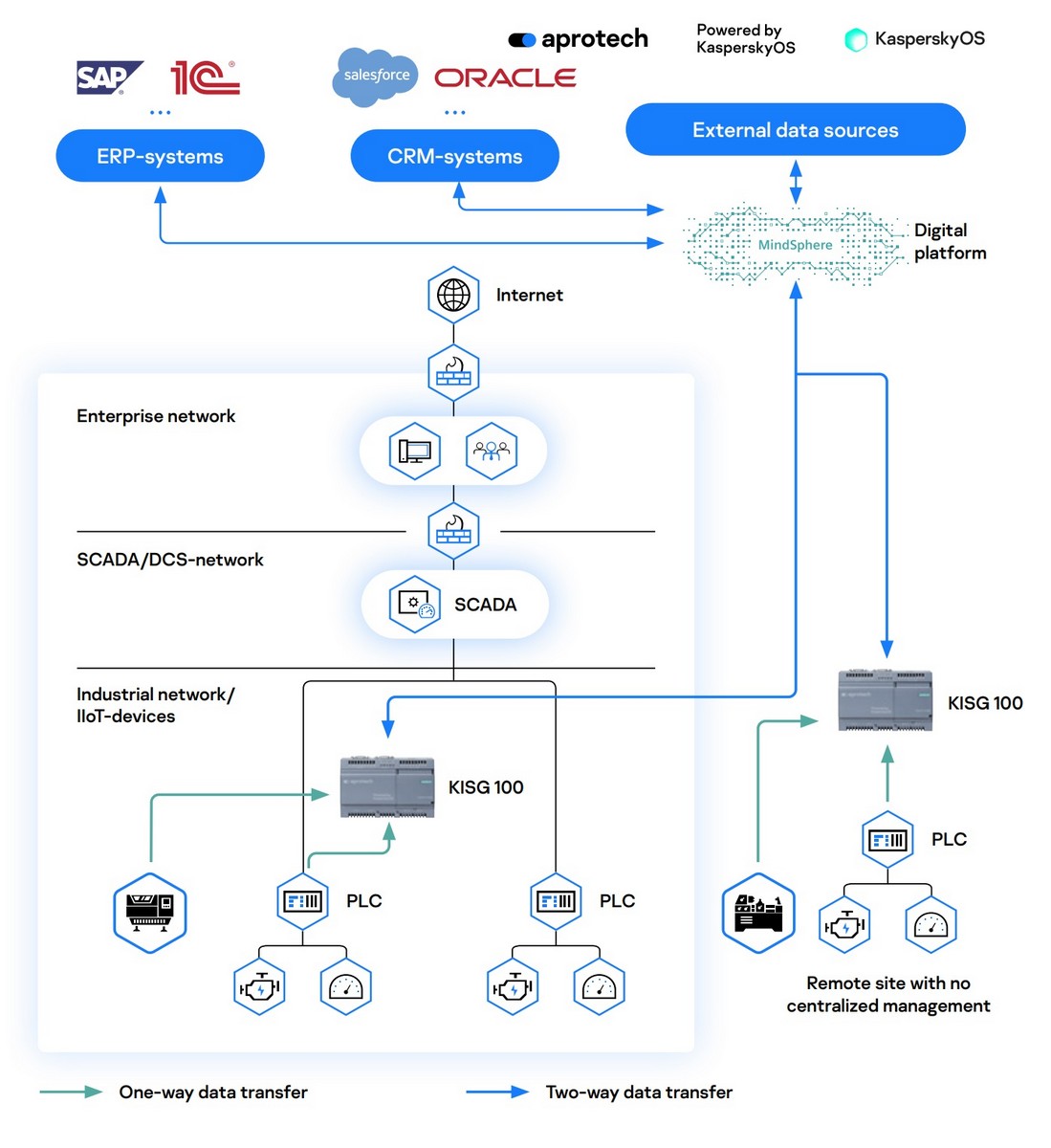
As you can see, the box is small, but it sure is powerful too. One crucial functionality is that it only allows ‘permitted’ data to be transferred. It also allows data transmission strictly in just one direction. Thus, KISG 100 can intercept a whole hodge-podge of attacks: man-in-the-middle, man-in-the-cloud, DDoS attacks, and many more of the internet-based threats that just keep on coming at us in these ‘roaring’ digital times.
KISG 100 (which works on the Siemens SIMATIC IOT2040 hardware platform and our cyber immune KasperskyOS) separates external and internal networks in such a way that not a single byte of malicious code can possibly get between the two – so the machinery stays fully protected. The technology (for which we have three patents pending) works based on the data-diode principle: opening the flow of data in only one direction and only when certain conditions are met. But, unlike competing solutions, KISG does this (i) more reliably, (ii) simpler, and (iii) cheaper!
OK, let’s have a closer look…
It’s not for nothing this little box is called a ‘gateway’, for in principle it works just like the mechanical hydro-technical gateway found on canals – a lock. You open the lower gate, the boat goes into the chamber; the water level rises, the upper gate opens, the boat leaves the chamber. In the same way, KISG 100 first initializes the agent of the source from the industrial network, then connects it with the agent of the receiver of data in the direction of the server, and allows a one-way transfer of data.
Once a connection is made between the machinery and the server, the system has so-called protected status: access to an external network and also untrusted memory is forbidden to both agents (source and receiver), while access to trusted memory (from which they receive working parameters like encryption keys, certificates, etc.) is permitted. With this status, the gateway can’t be compromised by attacks from an external network – since all its components at this stage are disconnected from the external world and are considered trusted; they are only loaded and initialized.
After initialization, the status of the gateway is changed to active: the receiver agent gets the right to both transfer data to an external network and access untrusted memory (in which temporary data is contained). Thus, even if there’s a hack on the server side, the hackers can’t get to the other components of the gateway or the industrial network. Like this:
Control over observation of the rules of interaction between agents, plus switching the statuses of the gateway, is done by our cybersecurity monitor – KSS. This isolated subsystem of KasperskyOS constantly monitors observance of pre-defined security policies (what component can do what) and, as per the ‘default deny’ principle, blocks all forbidden actions. The main competitive advantage of KSS is that the security policies are very convenient to both describe with a special language and to combine different pre-defined models of cybersecurity. If just one of the components of KISG 100 (for example, the receiver agent) turns out to be compromised, it can’t harm the rest of the components, while the system operator is informed of the attack and can get to work dealing with it.
So, you still with us? :) Then here comes the inevitable ‘wait, there’s more!’…
The tiny box can help provide additional digital services. It allows safely integrating industrial data in ERP/CRM and assorted other business systems of an enterprise!
Scenarios involving such services can vary greatly. For example, for our respected customer Chelpipe Group (a leading producer of steel pipe), we calculated the efficiency of a machine-tool that cuts pipe. Thanks to this predictive analysis, up to $7000 per month (!) can be saved on outlays when choosing to buy such a tool. In fact, such integration provides simply endless possibilities.
One more example: the St. Petersburg company LenPoligraphMash connected its industrial equipment to ther 1C ERP system, and now (almost in real time) it shows analytics in an ERP on the performance of all operators – so it can pay those operators based on actual (not normative or averaged) down time. The uniqueness of this approach and its scalability was confirmed by experts of the respected analytical agency Arc Advisory Group in its first cyberimmunity report.
So, as you can see, this isn’t just any old box. It’s a perfectly ingenious magical one! Already, besides its being in full combat duty at Chelpipe Group, KISG 100 is installed on the metals processing machinery of StankoMashKomplex, successful pilot projects are up and running at Rostec and Gazprom Neft, and dozens of other pilots with large industrial organizations have begun. The device received a special awards for outstanding tech achievement at the largest Chinese IT event, Internet World Conference; at the Hannover Messe 2021 industrial exhibition KISG 100 earned a place among the world’s top innovational solutions; and just recently it took the top prize in the IoT Awards 2021 of the Internet of Things Association, beating many top-rated companies.
In the future, we’ll be expanding the range of such smart boxes. Already, KISG 100‘s ‘older brother’ – KISG 1000 – is being beta tested. In addition to being a gateway-guard like KISG 100, KISG 1000 is also an inspector: it not only collects, checks and distributes telemetry, it also transfers management commands to devices and protects against network attacks.
The takeaway: you needn’t be afraid of digital; you simply need to be able to… cook it properly! And we’re here to help with that – with the best chefs and recipes!


