January 24, 2013
All Mouth, No Trouser.
“All animals are equal, but some are more equal than others.” Thus spake Napoleon, the head-hog in Orwell’s dystopian classic.
The genius of this phrase lies in its universality – a small addition turns the truth inside out. Alas, this witty paradox [sic.] is met not only in farmer-revolutionary sagas, but also in such (seemingly very distant) themes as – and you won’t believe this – antivirus tests! Thus, “All published AV-test results are equal, but some are more equal than others.” Indeed, after crafty marketing folk have applied their magic and “processed” the results of third-party comparative AV tests, the final product – test results as published by certain AV companies – can hardly be described as equal in value: they get distorted so much that nothing of true value can be learned from them.
Let’s take an imaginary antivirus company – one that hardly distinguishes itself from its competitors with outstanding technological prowess or quality of protection, but which has ambitions of global proportions and a super-duper sales plan to fulfill them. So, what’s it gonna first do to get nearer its plan for global domination? Improve its antivirus engine, expand its antivirus database, and/or turbo charge its quality and speed of detection? No, no, no. That takes faaaar too much time. And costs faaaar too much money. Well, that is – when you’re in the Premiership of antivirus (getting up to the First Division ain’t that hard). But the nearer the top you get in the Champions League in terms of protection, the more dough is needed to secure every extra hundredth of a real percent of detection, and the more brains it requires.
It’s much cheaper and quicker to take another route – not the technological one, but a marketing one. Thus, insufficient technological mastery and quality of antivirus detection often gets compensated by a cunning informational strategy.
But how?
Indirectly; that’s how…
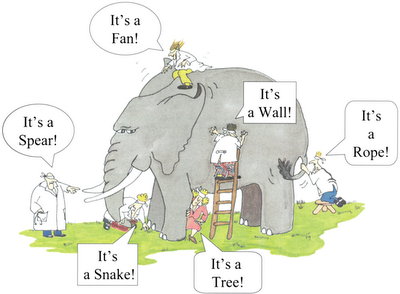
Now, what’s the best way to evaluate the quality of the protection technologies of an antivirus product? Of course it’s through independent, objective opinion by third parties. Analysts, clients and partners give good input, but their impartiality naturally can’t be guaranteed. Comparative tests conducted by independent, specialized testing labs are where the real deal’s at. However, testers are peculiar beasts: they concentrate purely on their narrow trade – that’ll be testing – which is good, as testing done well – i.e., properly and accurately – is no easy task. But their results can often come across as… slightly dull, and could do with a bit of jazzing up. Which is where testing marketing done by those who order the testing kicks in: cunning manipulation of objective test results – to make the dirty-faced appear as angels, and/or the top-notchers appear as also-rans. It all becomes reminiscent of the ancient Eastern parable about the blind men and the elephant. Only in this case the marketing folk – with perfect eyesight – “perceive” the results deliberately biasedly. The blind men couldn’t help their misperceptions.