February 3, 2012
DDoS – a Nasty SOB, but Curable – with KDP.
Hi everyone!
The Russian parliamentary elections late last year and the ensuing mass protests against their alleged falsification have brought about a sharp increase in the level of polarization of viewpoints being bandied about on Russian-language social networks and online media.
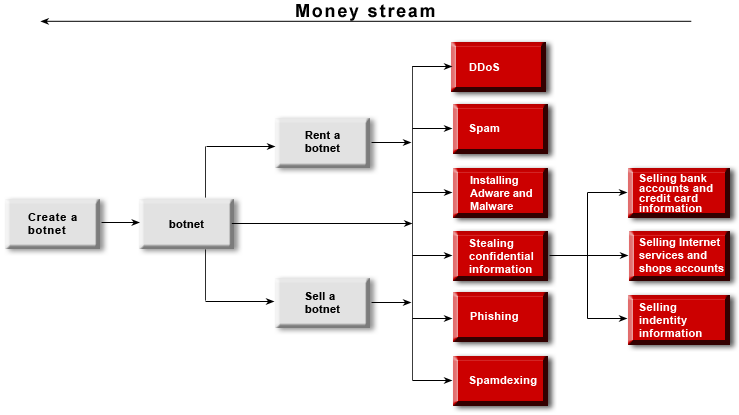
Simultaneously with all this, plenty of the Russian online media were visited by a ghost – the ghost of DDoS (Distributed Denial of Service Attack) – in early December 2011. This led to brazen hacker attacks, with one after another Russian website going down, and several attacks occurring simultaneously. Some were organized using traditional criminal bot networks, but behind them, it sure seems to me, stood marginal political groups, since the victims of the attacks were the sites both of opposition groups (including the Communist Party) and also of the ruling United Russia party.
A second DDoS attack – in mid-December – was more sophisticated. To date we still don’t have any reliable information about its origin – that is, not technically (how they actually pulled off the DDoS), and not the people who ordered it. And I’m not sure we’ll ever get to the bottom of it.
But I won’t get bogged down here with theory.