August 14, 2012
Safe Money: A Virtual Safe for Virtual Money – that Actually Works.
Apart from petty cash carried on the person, where in general does money mostly get stored?
Sure, gangsters still prefer cash stashed in a grubby cubby hole, while grandma still resorts to the trusty in-a-stocking-under-the-matrass option. But in most other cases the sensible move is to have cash converted into non-cash funds – or virtual money – ASAP, and put in banks and the like, where it can at least earn a bit of interest. And banks tend to keep cash in big safes. With this sensible option today come various useful knick-knacks like online banking, online shopping, and online just about whatever.
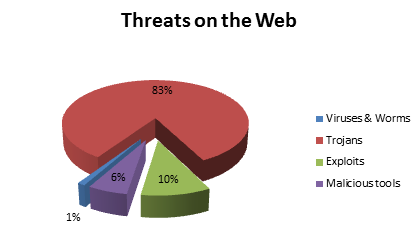
Of course, wherever lots of money and the Internet are closely connected there’ll always be plenty of cyber-scoundrels close by trying to get at that money – be it in folks’ current, savings or credit card accounts. And we’re not talking here about an occasional threat posed by a pair of unwashed, long-haired marginals from da cyber-underground either. It’s a real serious problem on a worldwide scale. A well-organized and smoothly running criminal industry with a multi-billion dollar turnover. It’s no wonder then that the security of financial transactions on the Internet has become the No. 1 problem (pdf) in the world for the majority of users.
Now, just like with banks with safes for paper money, this virtual money accessed via the Internet could also do with a safe – a virtual one, but one no less secure than a high-tensile steel armor-plated one. So let me tell you about our new Safe Money technology, which will be appearing in the next version of KIS towards the end of August/the beginning of September (depending on the country).
Before going through the details and advantages of Safe Money, it’s probably best first to look at how the cyber-swine try to get their grubby mitts into your virtual pockets. Or, less figuratively, to get at your user logins and passwords to access your online banking and other ‘monied’ accounts.
So, three ways how the cyber-baddies tend to break in:
- Infecting the computer of a victim with a Trojan to thieve data, take screenshots, and log keyboard strikes. Infection frequently occurs via a vulnerability in popular software;
- Phishing and social engineering: imitating genuine online stores, bank websites, dialog boxes, even telephone calls, etc.; and
- Different high-profile attacks like sniffing, DNS/Proxy server substitution, fraudulent certificate use, etc. to intercept traffic using man-in-the-middle attacks, and also man-in-the-browser threats, wardriving, etc.
And now – another threesome: the three main problems in terms of security against financial cyber-fraud:
- a lack of reliable site identification;
- a lack of trusted connections via the Internet between online services and clients; and
- a lack of guarantees that software installed on a computer doesn’t contain vulnerabilities that could be exploited by malware.
Luckily (for some), many aspects of this problem are comfortably dealt with by the latest Internet Security-class protection products. Only the most slothful of IT Security vendors these days don’t offer built-in protection against phishing; however, the quality of protection is another matter. But this is in no way enough to be safe in real life scenarios (about scenarios – see below). Still, the majority of products don’t have all the necessary features to provide fully comprehensive protection. What’s worse, the features they do have don’t work together harmoniously in solving specific problems, even though what’s really needed here is a multi-faceted, wide-spectrum “medicine”.
And so, if you’ll please now welcome onto the stage… Safe Money technology!
Safe Money resides in the upcoming version of KIS. What you do is enter the address of an online service that needs to be protected that uses money (a bank, store, auction system, payment system, etc.). Or you can choose a site from the built-in database, which includes 1500 different banks and 84 domains. On entering the site you need to choose the “Run the protected browser automatically” option, and from then on all sessions with that site are automatically launched in a special protected browser mode.
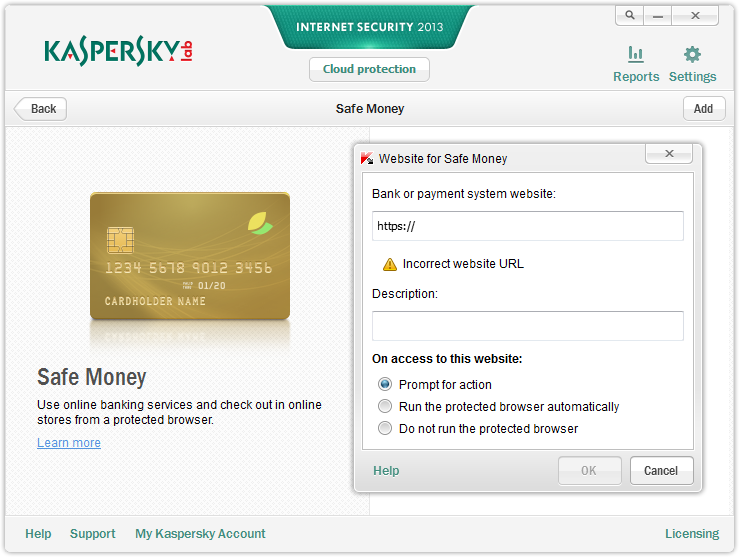
More: So what does this here protected browser mode do then? …