October 26, 2017
More transparent than the air you breathe.
Hi folks!
I think it’s always possible – if you try hard enough – to be able to find something good in a bad situation.
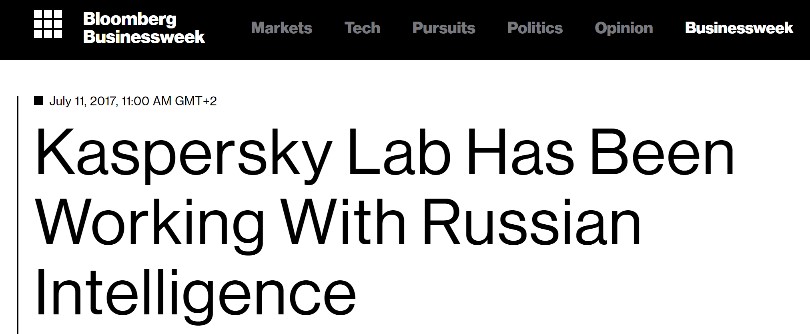
The recent negative campaign against KL in the U.S. press hasn’t been pleasant for us, but we have tried hard – and found – some good things: it allowed us to make certain curious observations and deductions, and also gave a magic kick up the proverbial on planned KL business initiatives that never really came to anything long ago – one of which initiatives I’ll be telling you about in this post.
The cybersecurity business is based on trust: trust between users and the developer. For example, any antivirus, in order to do its job – uncover and protect against malware – uses a number of technologies that require broad access rights to users’ computers. If they didn’t have them, they’d be defunct. But it can’t be any other way: the cyber-bandits use all available methods to be able to penetrate computers to then lodge their malware in those computers’ operating systems. And the only way to be able to detect and smoke that malware out is to have the same deep system access privileges. Problem is, such a truism also acts as fertile ground for all sorts of conspiracy theories in the same vein as the old classic: ‘antivirus companies write the viruses themselves’ (with that kind of reasoning I dread to think what, say, the fire service or the medical profession get up to themselves when not putting out fires and treating the sick). And the latest theory growing out of that fertile ground is the one where a cyber-military has hacked our products and is spying on another cyber-military via those same products.
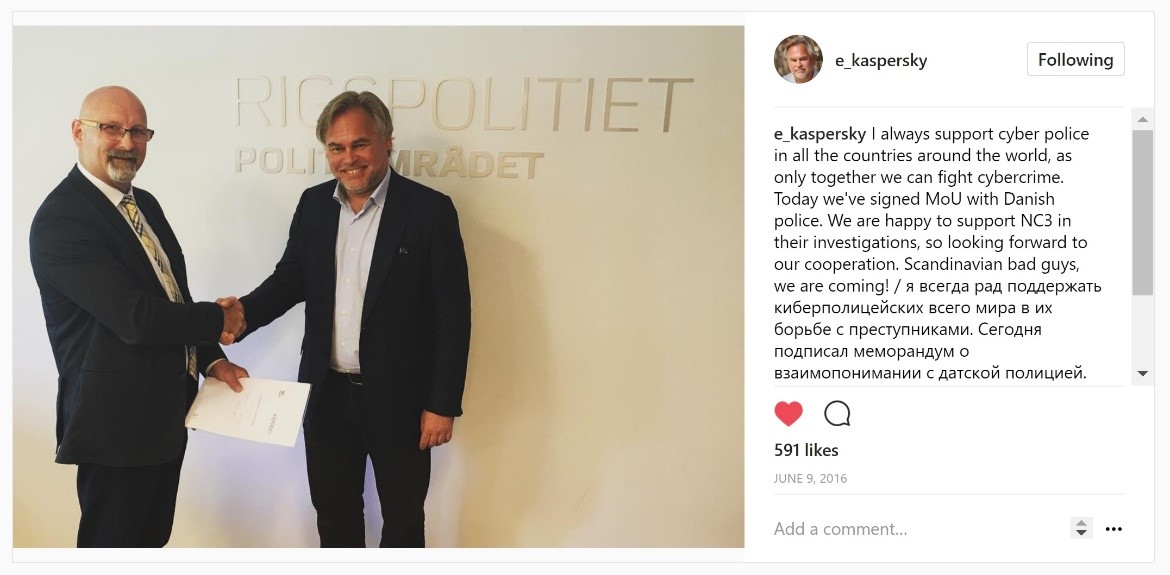
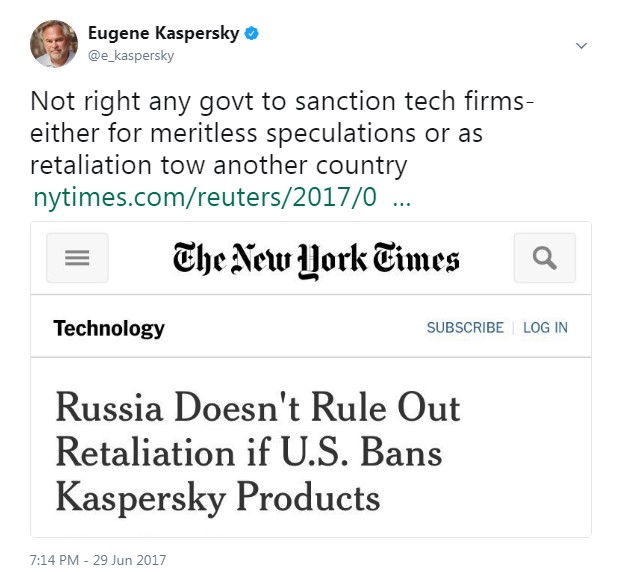
There are three things that all the separate U.S. media attacks on KL have in common: (i) a complete lack of evidence provided as a basis for their reports; (ii) use of only anonymous sources; and (iii) the most unpleasant – abuse of the trust relationship that necessarily exists between users and us. Indeed, it has to be admitted that that trusting relationship – built up over decades – has alas been impaired. And not just for KL, but the whole cybersecurity industry – since all vendors use similar technologies for providing quality protection.
Can this crisis of trust be overcome? And if so – how?
It can. And it must. But it needs to be done only by taking specific, reasoned steps that technically prove how trust is, in fact, being threatened by nothing and no one. Users, just as before, can trust developers – who always have, currently have, and will always have, one single mission: protecting against cyberthreats.
We’ve always been as open as possible with all our plans and undertakings, especially technological ones. All our key tech is documented to the fullest (falling short of revealing trade secrets) and publicly cataloged. Well a few days ago we went one step a huge leap even further: we announced our Global Transparency Initiative. We did so to dispel any remaining doubts as to the purity of our products, and also to emphasize the transparency of our internal business processes and their conformity to the highest standards in the industry.
So what are we actually going to do?
First, we’ll be inviting independent organizations to analyze the source code of our products and updates. And they can analyze literally everything – right down to the last byte of the very oldest of our backups. The key word here is independent. Closely behind it is another key word: updates; the analysis and audit won’t be just of the products but the equally important updates as well.
Second, we’ll have a similarly independent appraisal of (i) our secure-development-lifecycle processes and software, and (ii) our supply-chain risk-mitigation strategies that we apply in delivering our products to the end user.
Third, we’ll be opening three Transparency Centers – in the U.S., Europe and Asia – where customers, partners and government representatives can get exhaustive information about our products and technologies and conduct their own analyses and evaluations.
And that’s only the start of it. We’ve plenty more plans to become even more transparent – as transparent as air (and no jokes please about pollution or smog in large cities:). We’re only just kicking off this project, but we’ll be regularly sharing with you more as we go along. Stay tuned…
PS: If you have any ideas, suggestions or other comments – do let us know, here.