September 11, 2012
Monthly Archives: September 2012
September 6, 2012
Windows 8: We’re Ready Already
Greetings droogs!
The new version of KIS is attracting quite a bit of buzz in the media: in the two weeks since its global premiere it has been receiving gushing review after gushing review. Just about all of them go into plenty of detail covering all the ins and outs of the product, and specific features have been covered here on this blog of mine – for example posts about automatic protection from vulnerabilities and making secure payments.
But KIS has one more delicious layer of features; however, they can’t be used yet, and will only become applicable in the (nearest) future (we really mean it when we say Be Ready for What’s Next, you know!). These futuresque featuresques are undeservedly not getting the limelight. I’m talking about KIS support for Windows 8.
So what are these technologies, how do they fit in with Win8, and what are the benefits for users?
I’ll start with the most obvious: the new Windows 8 interface. I haven’t had a test-drive myself, but I’ve heard lots of good things about it and read flattering reviews. The fully redesigned interface is really not bad looking at all, and that goes for the desktop version and the tablet-touchscreen-mobile incarnation. I’m looking forward to its release and the reactions of users…
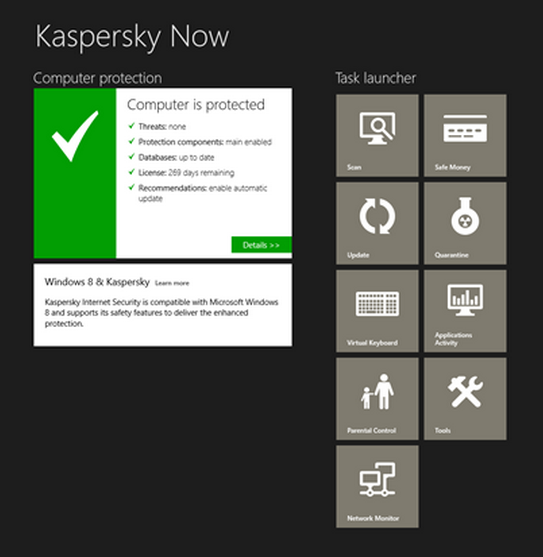
At the same time it has to be said that this new kid on the block has significantly increased the proverbial pain in the neck for third-party software developers: in order to cater to the whole spectrum of user preferences it was deemed necessary to have two interfaces – the classic one we’re all used to, and the new go-faster-stripes one. In response, we’ve been one of the first in the antivirus industry to develop a special application that transfers the antivirus management features to the new Windows 8 interface. The application is free of charge, and you can download and install it from the Windows Store.
September 5, 2012
Kamchatka-2012: Rocking the Ksudach.
Days 3-4-5. Ksudach.
We flew from Kurile Lake to Ksudach by helicopter. We could have got there by foot of course, but, first, no one knew the way; second, we couldn’t find a crazy enough guide; and third, no one really fancied battling through the dense undergrowth. Oh, and fourth: the whole route is cut with bears. Maybe next time we should prepare beforehand and work out a passable route – one that would also take in Kambalny volcano. From Google Maps it looks rather tempting.
September 4, 2012
Social Networks: the Force Is Strong with These Ones.
Prologue
The history of social networks is pretty much like Star Wars. Really! Social networks started out obscure and mysterious, with folks saying, “There’s this new type of site, with enormous capabilities and hidden business opportunities, which no one can estimate at present, but in the future will truly make all people truly connected, free and equal!” It’s pure Eastern-spirituality-influenced George Lucas – about “bringing balance to the Force.” And so it came to pass – social networks became a perfect communication ground for all – ordinary folks, companies, and the media.
Of course, with such a boring script you’re hardly going to get a blockbuster movie :-). Let’s face it, you can’t have folks living happily ever after (and all with equal rights, opportunities, etc., etc.) at the start of a film, can you?! The story needs an insidious infernal plan pursued by dark forces to arise. And – voila! – that’s what we got. Social networks became the medium of choice for games played by the world’s intelligence services and manipulation of public opinion – about which I’ve written and talked plenty before.
So, Star Wars: A New Hope has finished. The next chapter has begun:
The Empire Strikes Back
“Forming public opinion” via social networks has for several years already been practiced rather successfully by governments of many countries, no matter their political traditions or leanings. With so much open and free (no cost) information on the surface – no digging necessary – folks themselves tell all about their news, interesting information, whereabouts, lists of colleagues, friends and professional contacts. And the bizarre thing is that anyone who can access that data – private individuals, companies, criminals, members of a cross-stich embroidery group… (you get the point). The data lies about on the surface and people continue (despite warnings) to put more and more such data on the Internet. But with the many APIs crisscrossing social networks acting as mutagens that speed up the evolution, information uploaded one day on just one network is the next day forever (literally: eternally) indexed in search engines.
At the same time the intelligence services have happily joined social networks – becoming “users” themselves – but with their own agenda, naturally. For ordinary folks social networks are mostly a source of reading matter; for companies they’re a source of – or tool for – sales and marketing; but for intelligence services social networks represent a vital means for protecting state interests, and can also be used as weapons against potential opponents.




