February 10, 2012
The Black Box.
Filtering out spam may not seem such a big deal – after all, even a kid knows the difference between a Viagra advert and a normal message! In the security world things are much more complicated as we have to create something akin to artificial intelligence that is capable of doing the job automatically, on the fly.
That’s no easy task and entails all sorts of demands in terms of efficiency, reliability, compatibility and so on. And you no doubt know where things stand with AI – there are plenty who claim to have got it figured, but there’s nothing really to show for it (or if there is, they’re doing a good job of keeping it a secret).
Anti-spam security is no easier a task than anti-malware protection. And may even be more difficult (or maybe I just understand more about viruses…). The spam industry is a multi-billion dollar business and tens of thousands of skilled bloodsuckers are behind the huge variety of junk that is sent out. And these parasites show great ingenuity when it comes to linguistics and other stuff to make spam reach your inbox.
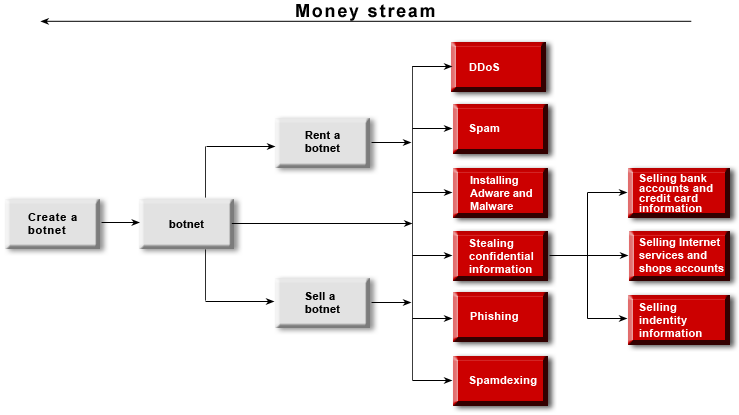
On the face of it, a spammer’s work looks fairly easy – write a spam message, test it against several of the most popular anti-spam filters and spawn via a botnet. But few customers realize that a spam message’s lifecycle is just half an hour to an hour long. 90% of a mass mailing will never reach its intended recipients – spam filters, activated with an update or triggered by statistics, will intercept it.
And it’s that black box – the thing that withstands the worst things that email traffic throws at it and keeps your inbox clean – that I want to discuss here.
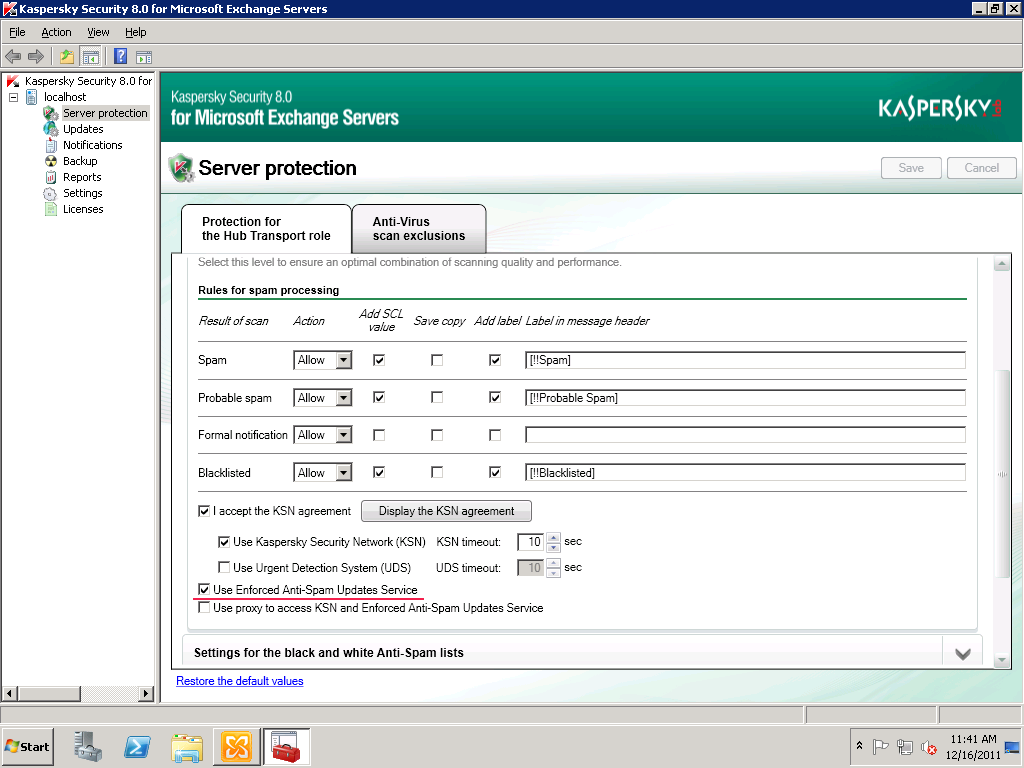
First of all, a bit of background. Since 2002 our anti-spam solution (KAS) has got through four generations of engine and we’re now developing a fifth. A single blog post would hardly suffice to recount everything. Basically, KAS has acquired lots of bits and bobs over the last 10 years. It boasts over 10 methods of spam analysis alone. That’s why I’ll start with our new ‘Möbius‘ technology – just in time for its debut in the latest version of KAS for Exchange Server.