August 6, 2020
Top-5 K-technologies that got us into the Global Top-100 Innovators.
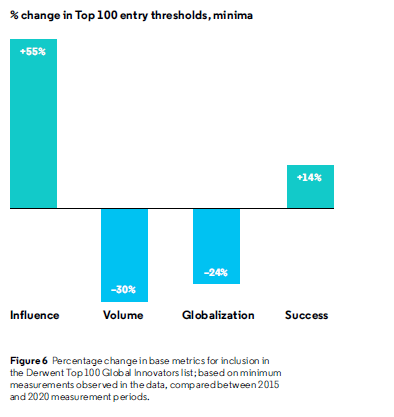
We’ve done it again! For the second time we’re in the Derwent Top 100 Global Innovators – a prestigious list of global companies that’s drawn up based on their patent portfolios. I say prestigious, as on the list we’re rubbing shoulders with companies such as Amazon, Facebook, Google, Microsoft, Oracle, Symantec and Tencent; also – the list isn’t just a selection of seemingly strong companies patents-wise: it’s formed upon the titanic analytical work of Clarivate Analytics, which sees it evaluate more than 14,000 (!) candidate companies on all sorts of criteria, of which the main one is citation rate, aka ‘influence’. And as if that wasn’t tough enough, in five years the threshold requirement for inclusion in the Top-100 on this criterion has risen some 55%:
In a bit more detail, the citation rate is the level of influence of inventions on the innovations of other companies. For us, it’s how often we’re mentioned by other inventors in their patents. And to be formally mentioned in another company’s patent means you’ve come up with something new and genuinely innovative and helpful, which aids their ‘something new and genuinely innovative and helpful’. Of course, such an established system of acknowledging other innovators – it’s no place for those who come up with mere BS patents. And that’s why none of those come anywhere near this Top-100. Meanwhile, we’re straight in there – in among the top 100 global innovator companies that genuinely move technological progress forward.
Wow, that feels good. It’s like a pat on the back for all our hard work: true recognition of the contributions we’ve been making. Hurray!
Still reeling – glowing! – from all this, ever the curious one, I wondered which, say, five, of our patented technologies are the most cited – the most influential. So I had a look. And here’s what I found…
5th place – 160 citations: US8042184B1 – ‘Rapid analysis of data stream for malware presence’.
This patent covers our technology that rapidly scans data streams passing through network gateways. It carries out real-time analysis of stream content separately – segment by segment – per format (e.g., web pages, files, email with attachments, and so on), and then transfers each separate element for the corresponding specialized processing. That is, the entire transferred data object doesn’t need to be assembled. This is easier on hardware resources, and scanning speed is greatly increased meaning there’s more chance of finding cyberthreats. This K-tech is licensed to Allied Telesis, D-Link, Nokia, ZyXEL, and many other developers and providers; and it’s cited in the patents of: IBM, Webroot, FireEye, Trend Micro, HP, Juniper, and others.
Not bad, eh?! And all that’s down to what we do here in northwest Moscow, not Palo Alto ).
4th place – 170 citations: US8214905B1 – ‘System and method for dynamically allocating computing resources for processing security information’.
Cybersecurity – it’s everyone’s business, in all senses. Without anonymized signals from users about suspicious activity, developers can’t provide adequate levels of protection. And the more users – the better: so with big data, anomalies are much easier to pick out, which helps uncover hitherto unknown cyberattacks.
But not all data is equal, and not all users are equal either. There are different levels of expertise in computer usage on the part of users – including savviness with computer security. And the more sophisticated a user is, the more likely the signals they send – anonymously, of course – will lead to a cyberattack.
This K-technology evaluates the level of savvy of users based on how they use their computers. For example: the type of installation of the antivirus (regular or advanced), whether interactive mode is chosen, and other software and equipment used. Then, at the next level, user activity is analyzed – including the quantity and quality of detected threats, the share of error messages, reaction speeds, and so on. And the higher the rating of the source, the more weight is given to their evaluation and, correspondingly, processing of their data is granted a higher priority. Details – here.
Cited in the patents of: NEC, Dell, IBM, FireEye, Symantec, HP, and others.
3rd place – 170 citations: US8365297B1 – ‘System and method for detecting malware targeting the boot process of a computer using boot process emulation (mirror patents in Russia: RU2472215C1, in Europe: EP2610774B1, and in China: CN103065094B).
This is one of the best technologies in the world for uncovering bootkits – dangerous malicious programs that covertly activate before the operating system boots up, meaning before the cyberprotection loads. To fish out a bootkit we create an artificial environment – an emulator – that mimics the process of a computer loading up and launch within it suspicious objects. The malware thinks the time has come to get to work and launches its standard procedure – and that’s when we zap it! I’ve already detailed this patent – here.
Cited in the patents of: Huawei, Intel, Tencent, Trend Micro, FireEye, Symantec, Palo Alto Networks, and others.
2nd place – 179 citations: US8370939B2 – ‘Protection against malware on web resources (mirror patents in Russia: RU2446459C1, Europe: EP2410452B1, and China: CN102147842B).
Here’s the essence of this tech: many websites (and FTP sites) can’t be scanned for cyberthreats without access rights. The solution is simple and effective: the AV uses information from the admin panel of the site provided by the user in order to reach the web resources (including files). This then enables the AV to go about its usual business of scanning them for malware.
Cited in the patents of: Dell, IBM, FireEye, Microsoft, Rockwell Collins, F-Secure, PayPal, Trend Micro, Gemalto, Symantec, and others.
And finally…
1st place – 181 citations(*): US8713631B1 – ‘System and method for detecting malicious code executed by virtual machine (mirror patents in Russia: RU2522019C1 and in China: CN103593608B).
There are certain applications written in code that requires a virtual machine for the code to be executed. Classic example: Java. This is done so a developer can easily port code onto other platforms (Windows, Linux…): the code’s the same, you just need a virtual machine to put it on.
The cyber-sleaze exploit vulnerabilities in virtual machines to penetrate computers; what’s more – for other applications (including for antivirus) on the virtual machine – it’s a black box and a trusted process. The patented technology is an effective way of controlling execution of code on virtual machines with the help of their modifications and receipt of events.
Cited in the patents of: Intel, FireEye, IBM, ESET, Check Point, Bitdefender, Symantec, and others.
In closing, a few stats to add further gloss to the above oh-my-global-innovations!…
In/by the Top-100: around 10 million employees work; 145,000 innovations were invented; $316 billion was spent on research; and $4.5 trillion was made in earnings!
You’ll surely agree – earning a place in this Top-100 isn’t only an honor to be proud of, it’s also really hard to pull off; which makes it all the more pleasant if you do actually manage it. To us, it’s confirmation that we create innovations of a truly global level, we secure the legal rights, and we get respective new products to the market. And we earn the deserved recognition for doing so. Nice. We work, we win. Keep up the good work (and the winning!).
(*) As per the patent database of Derwent Innovation as of May 9, 2020. The citation rate constantly increases; example: since the writing of this post this first place has had a +1 citation from FireEye, bringing total citations up to 182 from 181.

