September 24, 2013
K-LOVE & KISSES 2014 – PART 2: ALPHA, BETA, ZETA.
Welcome back folks!
What else new and interesting is to be found under the hood of KIS 2014, missioned to save your data from the cyber-swine? Today’s guest star is ZETA Shield technology.
ZETA Shield I think might be best described as a high-tech antivirus microscope for the detection and elimination of the most cunning of malware, which hides deep in the bowels of the inner recesses of complicated files. In short, this is our unique defense technology against future threats, one which can track down unknown cyber-contagion in the most unexpected places.
To understand the concept better, let’s take a set of traditional Russian dolls.
Open one and you find another inside, and nested inside that one – another, and so on and so on. And in terms of where troublesome programs hide, this is a pretty good analogy. Malware tries its hardest to embed itself into the very essence of its surroundings, and even uses digital ‘plastic surgery’ to change its appearance and hide from antivirus programs. It puts itself into archives, crypto-containers, multimedia files, office documents, scripts etc., etc. – the possibilities are endless. The task of the antivirus program is to delve into the actual essence of all these different objects, probe the interior, and extract the malware.
So that’s it? Well… no, it’s not quite as simple as just that.
Antivirus programs have long been able to take apart complicated files. For example, ever since the early 90s other companies have been licensing our antivirus engine in particular because of its ability to unpack archived and packed files. But unpacking is only half the job. You need an instrument that’s clever enough to not only take apart complicated files but that can also analyze these ‘Russian dolls’, understand what’s doing what in there, build connections between different events, and finally diagnose; importantly, to do that proactively – without classic signatures and updates. It’s a bit like the detective work that goes into locating potential binary weapons. Such weapons are made up of individual components which on their own are harmless, but when mixed create a deadly weapon.
And this is where ZETA Shield comes in.
And just in time too, as the number and perversity of both targeted and zero-day attacks are on the up and up. These are the very things ZETA is designed to deal with (ZETA = Zero-day Exploits & Targeted Attacks).
ZETA Shield follows another KIS 2014 debutante imported from our heavy-duty corporate products – Trusted Applications. ZETA also first appeared in our corporate solutions, where it’s more than proven its worth and has now been adapted for use in personal products. And as far as I know, it’s the world’s first use of such technology in personal products.
ZETA‘s work can be divided into two stages.
First comes the mechanical bit – the target needs to be taken to pieces. For instance a Word document might contain embedded items – other files, flash data, other documents, even an operating system distribution or a collection of viruses – anything at all! Our task is to identify the nature of all these items (and boy how they love to disguise themselves!) and classify them.
Then it gets more interesting… The heuristic analyzer kicks in – weighing up the contents, the layers of nesting, and the relationships among all these items, evaluating their similarity to templates of threats detected earlier, detecting anomalies, and taking a decision about how dangerous a given file is (whether or not it’s a binary weapon).
That decision is a joint one, taken together with our cloud-based KSN security network, which gives the antivirus program statistics on detection of similar suspicious symptoms on other users’ comps. Via KSN we see the scale and geographical distribution of threats, can identify anomalies typical of a targeted attack, and gain a lot of other useful data to help us protect users in the future.
Another analogy!: What ZETA Shield does at first is a bit like identifying a car by its components. Plastic body? Drive to one wheel? Motorcycle engine? German? Must be a Trabant. Simple!
But what it does next – like breaking the Trabant down to its components and then analyzing all of them individually to see what they’re really about – that takes some serious brainpower.
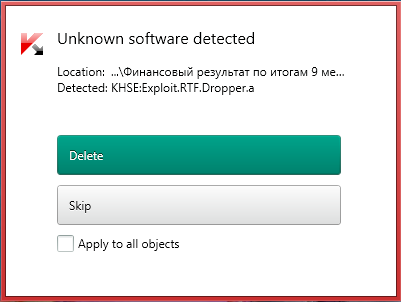
Take the example of a targeted attack back in March: the selected victims were sent RTF documents with tempting titles like ‘Financial Results for the First Nine Months of 2012’, supposedly from the Rubin Submarine Manufacturing Company (yes, this type of social engineering still works). Deep inside the document both an exploit and a malware dropper were hidden away but – and here’s the rub – the antivirus they were using didn’t recognize them – the cybercrims had concealed them so well among various types of garbage! ZETA Shield on the other hand when shown the offending RTF located them immediately!
A feature of this technology in the corporate environment is the ability to ‘take apart’ not only individual files but also streams of data. At the end of the day every file is part of a larger picture, and it’s by looking at this larger picture (of all the components of the binary weapon) that it’s possible to see the more complicated relationships and take more informed (better) decisions.
Alas, in KIS 2014 ZETA Shield has had to be handicapped a little in the interests of productivity: The home version works only with files and only in on demand mode. Nevertheless, with proper system hygiene (i.e., regular checking of the computer at maximum scanning power), this is still a serious +1 to defending against targeted attacks on home users. (For example, senior managers may be targeted either while at work, or at home on their personal computers. At home, they unfortunately don’t have protection at the corporate server level. And this is where ZETA Shield comes into its own, working together with Trusted Applications and Automatic Exploit Prevention to accurately filter out attacks that use various vulnerabilities.)
Logical questions here would be (i) why put this clever server technology into a personal product, and (ii) who aims a targeted attack at a home computer (or also, say, a small firm)?
First of all, one important point:
There’s a common view that targeted attacks are always aimed at governments, defense organizations, critical infrastructure installations or politicians, while if aimed at commercial companies – then at least those the size of Microsoft. Also, it’s often thought that the mind-boggling complexity of such attacks is worthy of… immortalization by Hollywood.
No. And no.
The reason for the first misconception can be explained by the fact that most of the media carry stories only about attacks at the highest level. And the reason for the second misconception comes from an abundance of incomprehensible technical terms or, on the contrary, a lack of information, with the logical train of thought going something like: ‘aha, they attacked a ministry, and ministries employ top security professionals and have good defenses, which means targeted attacks must take some real computer geniuses to pull off’.
But in reality almost any user or organization can become a victim of a targeted attack, as demonstrated by the antics of the Winnti hacking group or by the fact that commercial spyware like FinSpy exists. And don’t forget that computer threats are sometimes about as controllable as the flu – a targeted attack can go out of control and hit a lot of innocent bystanders (sometimes from one’s own camp!).
And as for the apparent complication of a targeted attack, well, the word ‘apparent’ hits the nail on the head. Yes, there are complicated cyber-operations (like Stuxnet and Flame). But the great majority is assemblies of known methods with a sprinkling of social engineering. And it’s actually becoming easier and cheaper. You can buy exploit kits for about a thousand dollars and put them together like a model kit.
Finally we come to the main reason for including ‘clever server technology’ and multi-level protection in personal products.
Any invention, including an evil one, has a life cycle. Sooner or later a broad spectrum of cyber-baddies will find a way to apply even the most complicated of attacks which were earlier the preserve of top professionals (yep, the commercialization of targeted attacks). But we’re ready for this: already KIS can withstand serious assaults from tomorrow’s malware!
In summary: We’re ready for what the future will bring. And now you are too.