September 1, 2020
The Catcher in the YARA – predicting black swans.
It’s been a long, long time since humanity has had a year like this one. I don’t think I’ve known a year with such a high concentration of black swans of various types and forms in it. And I don’t mean the kind with feathers. I’m talking about unexpected events with far-reaching consequences, as per the theory of Nassim Nicholas Taleb, published in his book The Black Swan: The Impact of the Highly Improbable in 2007. One of the main tenets of the theory is that, with hindsight, surprising events that have occurred seem so ‘obvious’ and predictable; however, before they occur – no one does indeed predict them.
Example: this ghastly virus that’s had the world in lockdown since March. It turns out there’s a whole extended family of such viruses – several dozen coronaviridae, and new ones are found regularly. Cats, dogs, birds, bats all get them. Humans get them; some cause common colds; others… So surely vaccines need to be developed against them as they have been for other deadly viruses like smallpox, polio, whatever. Sure, but that doesn’t always help a great deal. Look at flu – still no vaccine that inoculates folks after how many centuries? And anyway, to even start to develop a vaccine you need to know what you’re looking for, and that is more art than science, apparently.
So, why am I telling you this? What’s the connection to… it’s inevitably gonna be either cybersecurity or exotic travel, right?! Today – the former ).
Now, one of the most dangerous cyberthreats in existence are zero-days – rare, unknown (to cybersecurity folks et al.) vulnerabilities in software, which can do oh-my-grotesque large-scale awfulness and damage – but they often remain undiscovered up until the moment when (sometimes after) they’re exploited to inflict the awfulness.
However, cybersecurity experts have ways of dealing with unknown-cyber-quantities and predicting black swans. And in this post I want to talk about one such way: YARA.
Briefly, YARA helps malware research and detection by identifying files that meet certain conditions and providing a rule-based approach to creating descriptions of malware families based on textual or binary patterns. (Ooh, that sounds complicated. See the rest of this post for clarification.:) Thus, it’s used to search for similar malware by identifying patterns. The aim: to be able to say: ‘it looks like these malicious programs have been made by the same folks, with similar objectives’.
Ok, let’s take another metaphor: like a black swan, another water-based one; this time – the sea…
Let’s say a network you (as a cyber-sleuth) are studying (= examining for the presence of suspicious files/directories) is the ocean, which is full of thousands of different kinds of fish, and you’re an industrial fisherman out on the ocean in your ship casting off huge drift nets to catch the fish – but only certain breeds of fish (= malware created by particular hacker groups) are interesting to you. Now, the drift net is special: it has special ‘compartments’ into which fish only get into as per their particular breed (= malware characteristics). Then, at the end of the shift, what you have is a lot of caught fish all compartmentalized, and some of those fish will be relatively new, unseen before fish (new malware samples) about which you know practically nothing, but they’re in certain compartments labeled, say, ‘Looks like Breed X’ (hacker group X) and ‘Looks like Breed Y’ (hacker group Y).
We have a case that fits the fish/fishing metaphor perfectly. In 2015, our YARA guru and head of GReAT, Costin Raiu, went full-on cyber-Sherlock mode to find an exploit for Microsoft’s Silverlight software. You really need to read that article on the end of the ‘case’ link there but, if very briefly, what Costin did was carefully examine certain hacker-leaked email correspondence (of ‘Hacking Team’: hackers hacking hackers; go figure!) published in a detailed news article to put together out of practically nothing a YARA rule, which went on to help find the exploit and thus protect the world from all sorts of mega-trouble.
So, about these YARA rules…
We’ve been teaching the art of creating YARA rules for years. And since the cyberthreats YARA helps uncover are rather complex, we always ran the courses in person – offline – and only for a narrow group of top cyber-researchers. Of course, since March, offline training have been tricky due to lockdown; however, the need for education has hardly gone away, and indeed we’ve seen no dip in interest in our courses. This is only natural: the cyber-baddies continue to think up ever more sophisticated attacks – even more so under lockdown. Accordingly, keeping our special know-how about YARA to ourselves during lockdown looked just plain wrong. Therefore, we’ve (i) transferred the training format from offline to online, and (ii) made it accessible to anyone who wants to do it. For sure it’s paid, but the price for such a course at such a level (the very highest:) is very competitive and market-level.
Introducing! ->
What else?
Ah yes…
Now, given the ongoing (biological) virus-related troubles the world over, we’re continuing providing our assistance to those on the front lines. We started helping out the ‘light side’ at the start of the whole corona thing by giving free licenses to healthcare organizations. Now we’re adding to that helping out a variety of non-profit and non-governmental organizations fighting for rights in various causes or focusing on making cyber a better place (full list – here). For them, our YARA training will be free. Why? Because NGOs work with very sensitive information, which can end up being a hacked in targeted attacks, and by far not all NGOs can afford the luxury of a whole department of IT experts.
Ok, a quick run-through of what’s included in the course:
- 100% online, self-paced training, all from the sofa ). You could do the course intensely in a few evenings, or spread it over a month
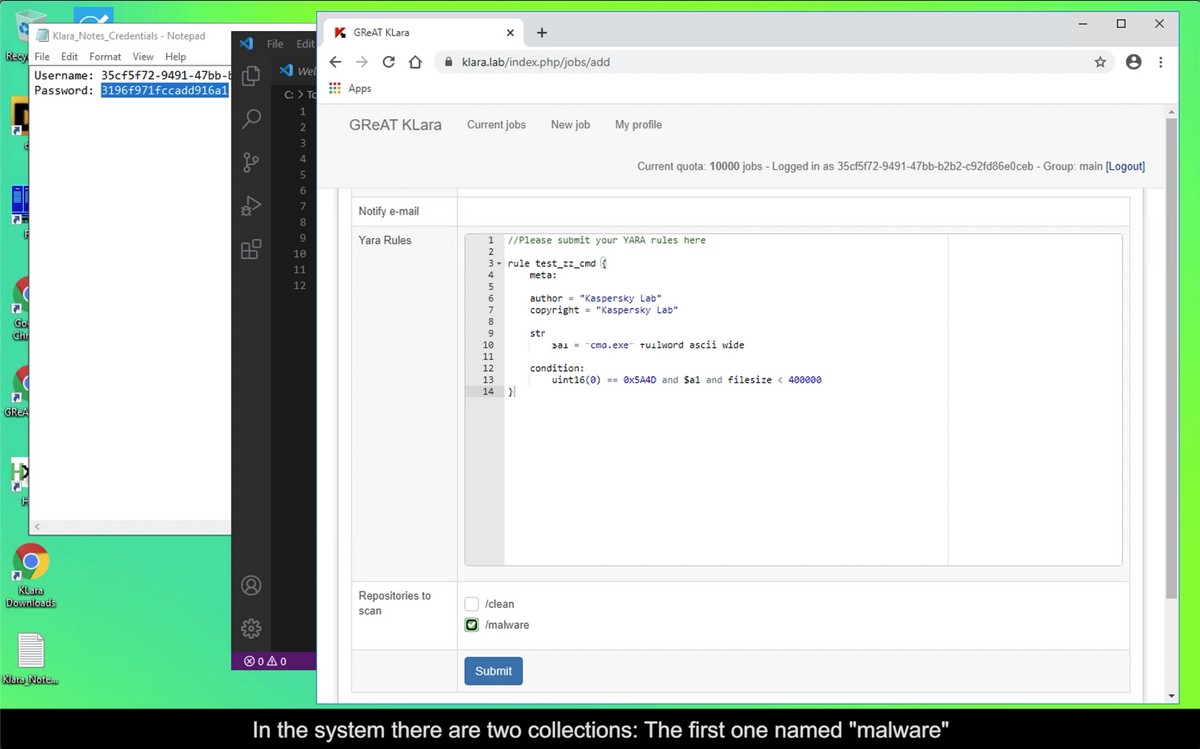
- A combination of both theory and hands-on doing: there’s a virtual lab for training in writing rules and searching for malware samples in our collection
- Practical exercises based on examples of real cyber-espionage attacks
- There’s a special module about the art of looking for something about which you’ve no precise knowledge: when intuition tells you cyber-evil is lurking somewhere, but you don’t know where or which cyber-evil in particular
- Everyone who completes the course gets a certificate confirming their new status as a YARA ninja. As previous graduates have told us, it really does help in their professional career
So there you have it folks – another extremely useful potential string in your bow in fighting highly sophisticated cyberthreats. Welcome! Meanwhile, it’s business as usual here at K – continuing our cyber-detective work so that we’ll be able to share yet more of our very latest know-how and practical experience in the good fight…
.@kaspersky launches its famous ‘YARA Ninja’ training online. Both theory and hands-on doing in a virtual lab. Apply hereTweet




