June 9, 2020
Which hacker group is attacking my corporate network? Don’t guess – check!
Around four years ago cybersecurity became a pawn used in geopolitical games of chess. Politicians of all stripes and nationalities wag fingers at and blame each other for hostile cyber-espionage operations, while at the same time – with the irony seemingly lost on them – bigging-up their own countries’ cyber weapons tools that are also used in offensive operations. And caught in the crossfire of geopolitical shenanigans are independent cybersecurity companies, who have the ability and gall guts to uncover all this very dangerous tomfoolery.
But, why? It’s all very simple…
First, ‘cyber’ is still really quite the cool/romantic/sci-fi/Hollywood/glamorous term it appears to have always been since its inception. It also sells – including newspapers online newspaper subscriptions. It’s popular – including to politicians: it’s a handy distraction – given its coolness and popularity – when distraction is something that’s needed, which is often.
Second, ‘cyber’ is really techy – most folks don’t understand it. As a result, the media, when covering anything to do with it, and always seeking more clicks on their stories, are able to print all manner of things that aren’t quite true (or completely false), but few readers notice. So what you get are a lot of stories in the press stating that this or that country’s hacker group is responsible for this or that embarrassing/costly/damaging/outrageous cyberattack. But can any of it be believed?
Generally, it’s hard to know if it can be believed or not. Given this, is it actually possible to accurately attribute a cyberattack to this or that nation state or even organization?
There are two aspects to the answer…
From the technical standpoint, cyberattacks possess an array of particular characteristics, but impartial system analysis thereof can only go so far in determining how much an attack looks like it’s the work of this or that hacker group. However, whether this or that hacker group might belong to… Military Intelligence Sub-Unit 233, the National Advanced Defense Research Projects Group, or the Joint Strategic Capabilities and Threat Reduction Taskforce (none of which exist, to save you Googling them:)… that is a political aspect, and here, the likelihood of manipulation of facts is near 100%. It turns from being technical, evidence-based, accurate conclusions to… palm or coffee grounds’ readings for fortune-telling. So we leave that to the press. We stay well away. Meanwhile, curiously, the percentage of political flies dousing themselves in the fact-based ointment of pure cybersecurity grows several-fold with the approach of key political events. Oh, just like the one that’s scheduled to take place in five months’ time!
So yes, political attribution is something we avoid. We stick to the technical side; in fact – it’s our duty and what we do as a business. And we do it better than anyone, I might modestly add ). We keep a close watch on all large hacker groups and their operations (600+ of them), and pay zero attention to what their affiliation might be. A thief is a thief, and should be in jail. And now, finally, 30+ years since I started out in this game, after collecting non-stop so much data about digital wrongdoing, we feel we’re ready to start sharing what we’ve got – in the good sense ).
Just the other day we launched a new awesome service aimed squarely at cybersecurity experts. It’s called the Kaspersky Threat Attribution Engine (KTAE). What it does is analyze suspicious files and determine from which hacker group a given cyberattack comes from. For knowing the identity of one’s attacker makes fighting it much easier: informed countermeasure decisions can be made, a plan of action can be drawn up, priorities can be set out, and on the whole an incident response can be rolled out smoothly and with minimal risk to the business.
So how do we do it?
As mentioned above, cyberattacks have many purely technical characteristics, or ‘flags’: the time and date when files are compiled, IP addresses, metadata, exploits, code fragments, passwords, language, file-naming conventions, debug paths, obfuscation and encryption tools, and more. Individually, characteristics such as these are useful only to (i) politicians – to point the finger at their opponents on the international arena to bolster a hidden agenda, or (ii) bad journalists – seeking sensational scoops. Only together can they indicate to which hacker group they belong.
Besides, flags are easily faked or emulated.
For example, hackers from the Lazarus group appear to have used Russian words transcribed into Latin letters in their implanted binary code; however, how the sentences are made up is unnatural in Russian and with grammatical/syntax mistakes: it looks like something Google Translate would produce, to perhaps send security experts in the wrong direction:
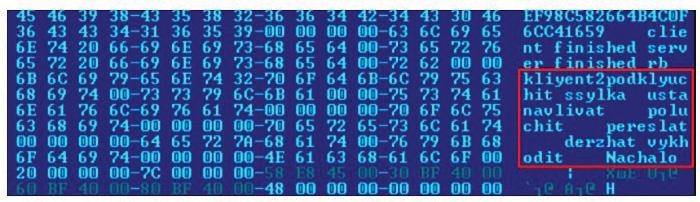
But, then again, any hacker group can use Google Translate – even for its native language, rendering ‘language used’ hardly a reliable pointer.
Here’s another case highlighting this in a slightly different way: The Hades group (authors of the infamous OlympicDestroyer worm that attacked infrastructure of the 2018 Olympic Games in South Korea) planted some flags as employed by the Lazarus group, leading many researchers up the garden path into believing the Hades hackers actually were Lazarus (other differences between the two groups’ ‘style’ led most to conclude it wasn’t Lazarus).
However, manual expert analysis of hundreds of characteristics and comparing them with the signature styles of other hacker groups… it’s practically impossible in short timeframes, with limited resources, and with acceptable quality of results. But such results are needed sooooo badly. Companies want to quickly catch the cyber…-octopus that’s attacking them, and nail down all its tentacles so that it doesn’t crawl somewhere where it shouldn’t again, and to be able to tell everyone about how to stay protected from this dangerous cyber-mollusk.
So, that’s what was needed sooooo badly? Well, that’s just what we’ve come up with…
A few years ago we developed for internal use a system for automated analysis of files. It works like this: we extract from a suspicious file something we’ve called genotypes – short fragments of code selected using our proprietary algorithm – and compare it with more than 60,000 objects of targeted attacks from our database on a whole spectrum of characteristics. This allows us to determine the most likely scenarios as to the origin of a cyberattack, and provide descriptions of the likely responsible hacker groups and links to paid and free resources for more detailed information and the development of the incident response strategy.
So, how reliable is the search, you may ask. Well, let’s just say that in three years the system hasn’t made a single mistake in pointing an ongoing investigation in the right direction!
Some of the more well-known investigations in which the system was used include: the LightSpy iOS implant, TajMahal, Shadowhammer, ShadowPad and Dtrack. And in all these cases the result full coincided with the evaluation of our experts. And now this tool can used by our customers!
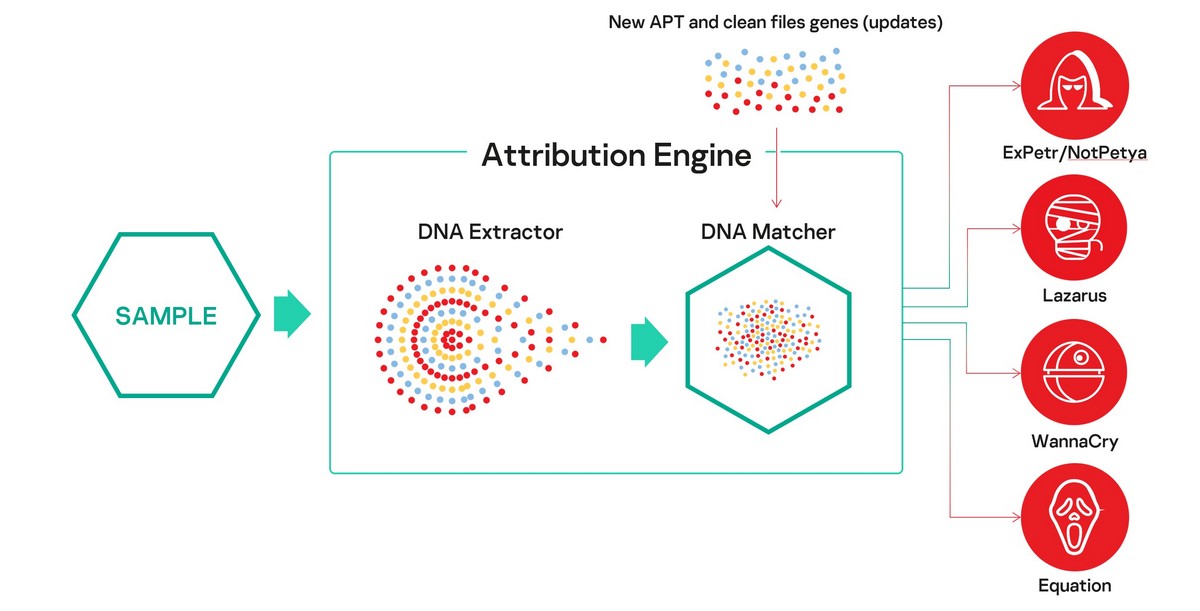
The Kaspersky Threat Attribution Engine comes in the form of a Linux-based distribution kit to be installed on a customer’s air-gapped computer – for maximal confidentiality. Updates are supplied on a USB. Besides, malware samples found by the customer’s own in-house analysts can be added to the KTAE database, and there’s also an API interface to connect the engine to other systems – including a third-party SOC (Security Operations Center).
In closing, I just want to state one disclaimer: like with any tool for automated analysis of malicious cyber-activity, KTAE doesn’t give a 100%-guaranteed result regarding attribution of an attack. Everything can be faked and tricked – including the most advanced solutions. Our main objective is to give experts a highly accurate pointer as to which direction they should be looking in, and to test different likely scenarios. Also, despite the ubiquitous resounding choruses about the effectiveness of AI (which doesn’t actually exist yet), existing ‘AI’ systems – even the very smartest – are at present not able to do everything without the assistance of Homo sapiens. It is namely a synergy of machines, data and experts – humachine – that today helps effectively fight even the most complex of cyberthreats.
Kaspersky releases Threat Attribution Engine that provides code similarity analysis and gives technical evidence for APT attributionTweet
And finally, I’d like to invite you to join a webinar on June 17 to see a live demo of the product, hear directly from its developers, and ask questions in real time.
That’s about all for today for your intro to our new KTAE. You can find more info on the product page, product datasheet and in this white paper.
PS: I highly recommend a read of this here post by one of the parents of this product, Costin Raiu, in which he goes into detail about the story of how it was developed, and also explains some of the finer points of KTAE on the whole.










