June 6, 2018
Features you’d normally never hear about (ver. 2018): KFP – Keeps your Funds Preserved!
When it comes to choosing an item of clothing – the only thing that’s important for me is functionality. Nice packaging, a designer brand, status level and other stuff don’t matter to me one bit. Same with cars really: if one gets you from A to B in good time, safely, and in reasonable comfort (so, maybe with a/c.) that’s all that really matters.
The same ‘ignore the unimportant stuff’ principle should be applied when it comes to one’s choice of cybersecurity product too. One really should – though many don’t – make sure one doesn’t fall for the ‘other stuff’ (= marketing waffle) that has no relation to actual protection. For it turns out that in thorough independent testing, new glamorous ‘next-generation antivirus’ products are shown to contain under their hoods fake artificial intelligence, adopted AV detection, and ‘protection’ full of holes. Put another way: they’re placebos, nothing more. So, in order not to become a victim of shiny marketing based on unsound security, you need to lift the hood yourself to have a look at how things work.
Of course, not everyone has the time and patience and technical knowledge to be able to plough through technical documentation of a cybersecurity product and understand it. But even if someone did, there’s still a chance the developer is mostly spinning a yarn throughout all that techy jargon.
With us, on the other hand, it’s just the opposite: we’re proud of our technologies, openly publish their technical details (without the yarns) and consider that anyone can understand them if explained appropriately. Ultimately we’re the most transparent cybersecurity company around – even to the extent that we’re ready to share our source code for inspection.
But to add to the clarity and accessibility of some of our tech, seven years ago, I started a series of regular posts on this here blog with the technology tag, in which all the main points of our more complex tech features are explained in simple language (complex tech features ‘you’d normally never hear about’, much less – read about in the regular, for-geeks-only technical notes). These are the largely invisible – under-the-hood – features, but they’re the ones that happen to be the real nuts-and-bolts of our cyberprotection.
Ok. Intro over. Today’s post is about how banks recognize a hack into your bank account.
Let’s say that one day you get a message from your bank that goes along the lines of: ‘Suspicious activity has been detected on your account…’. The first thing you do is go over the last few days trying to recall everywhere you’ve been, where you withdrew cash and how much, what you bought in shops/cafes, etc. and/or online, and so on.
In my case, it may look like this: (i) withdrew Norwegian kroner from an ATM in Longyearbyen, Svalbard, Norway; (ii) bought a steak and a beer salad and a mineral water in Oslo Airport, Norway; (iii) bought the missus a present in Schiphol Airport in Amsterdam, Holland – plus another salad and mineral water for lucky me; (iv) somewhere in the vicinity of the Azores bought some airplane internet access time; (v) withdrew some balboas in Tocumen Airport in Panama; and (vi) paid for dinner for a large party in a village not far from Panama City. And that was all in just one day!
Now, of course, to a bank, that string of transactions with a credit card – registered in none of the countries mentioned – sure could look suspicious. Quite who starts the day in the northernmost town in the world, buys an expensive duty free item a while later in a European capital, and ends up in Panama in the evening and forks out for a banquet, but has never taken such an unusual route before ever?
Sure. But let’s face it, banks can’t keep track of their millions of clients. How many employees would they need to do so? No, instead, the bank has a smart automated system (like Kaspersky Fraud Prevention (KFP)) that recognizes fraud automatically and with a high degree of accuracy. Ok, let’s have a look under KFP’s hood and see how it protects your money.
Each client of a bank has a model of behavior: a mathematical graph that contains the devices (computers, smartphones, tablets) and accounts of the user, bank services used (e.g., internet banking), and also rules for interaction among all the just mentioned. The model is built on the basis of collected anonymized data about specific activity of the client on the internet and using mobile bank. Crucially, the system isn’t interested in concrete transactions, sums involved, invoice details, names and so on – banking secrecy remains banking secrecy. Threats are calculated based solely on technical metadata and analysis of anonymized actions.
Such an approach allows to automatically detect many different kinds of cyber-fraud.
Example 1: Citizen X uses his internet banking application on his home computer. To authenticate his identity he uses the USB token given him by the bank. But since for protection he’s installed a next-generation antivirus based on a ‘cutting-edge AI system’, one day a malicious Trojan gets through. That Trojan – assisted by the token being forgotten about and left in the USB port – starts to transfer money on the quiet from Citizen X’s account. But it’s not ‘on the quiet’ for the banking anti-fraud system, which detects the anomalous behavior quickly, blocks the operation and informs the bank’s security department.
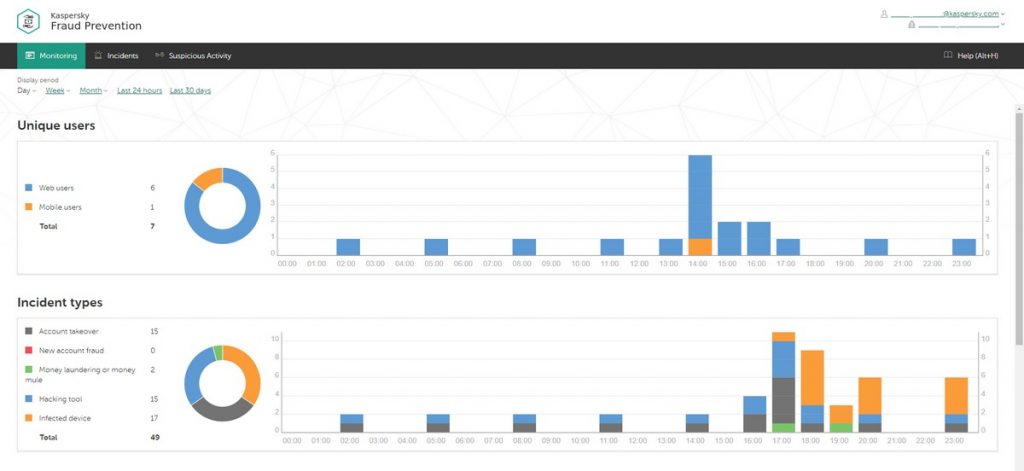 KFP control panel
KFP control panel
Indeed, any activity that goes outside the bounds of the standard model of the user’s behavior is flagged as suspicious. What’s more, the older the model (the longer the client has been with the bank), the more suspicious will be deemed even the tiniest anomaly. But once a certain threshold of suspicion is reached, or a critical event occurs, the system informs the bank for it to decide on the next steps: a message to the client asking for confirmation that the operations were genuine, blocking of the bank card, getting an expert to look at the case, and so on.
Example 2: Citizen Y from the town of Trumpton decided it would be ok to jot down the login and password to his internet banking on the back page of his diary, which tends to always lie around the apartment. Somehow, a cyber-fraudster learned of this shoddy cybersecurity hygiene, got hold of the login and password, and used them to attempt to access Citizen Y’s account. However, that cyber-fraudster tried to use an unknown (to the bank) desktop in the town of Trumptown, situated some 3000 kilometers from Trumpton. But, since Citizen Y only five minutes earlier had transferred his gran 100 dollars via the IP address of his Trumpton internet provider, the system quickly decided that this was – with very high probability – a fraudulent operation, and blocked the operation.
 The decision-making system for protection from bank fraud
The decision-making system for protection from bank fraud
The rules for interaction among devices, user accounts and banking services describe the logic of the system of protection. In general, rules can be pre-designated (created by experts of the developer company on the basis of analysis of cyber-fraud schemes), cloud-based (created by automated machine learning technologies in real time), or set by the bank in accordance with how paranoid it is its security policy.
So there you have it: what goes on behind the scenes to make sure your bank account’s secure. Of course, there’s a lot more to it, with many sub-technologies used in the system – including patent-pending ones and others about which PhDs have been written, but I can hardly fit explanations of those into this here short blogpost. Still, if you do have questions – let me know in the comments.
Yes, it turns out that knowledge of technologies – even just a little knowledge – is a good remedy against BS marketing in the era of placebo protection. It also helps you choose the right cybersecurity solutions – ones that really work, and work better than the rest. It’s also all rather nice and curiosity-satisfying to be able know details of how you’re actually protected!
What does a child first do with a new toy? He/she wants to look what’s inside – take it apart! Curiosity is only natural for cats human beings. It’s never too late to return to the basics in order to become cleverer and thus stronger!
That’s all for today folks. Back soon with this tag!…


