September 20, 2022
Introducing: KEDR Optimum. Superior enterprise-cybersecurity – with no fluff.
Naming products and services – and also their many different functions and features – in the infosec domain is, in a word, tricky. Why? Complexity…
Cybersecurity: it’s not a one-dimensional object like, say, a boat. There are different sized boats, different types of boats, but a boat is mostly always a boat. But in infosec, a modern system of enterprise cybersecurity does a great many technically complex things, and the question arises: how can it all be labeled simply and catchily (if that’s at all possible) so as to be reasonably easy to understand? And how can you differentiate one security system from another? Often it’s difficult explaining such differences in a long paragraph – let alone in the name of a product or service. Like I say: tricky.
Maybe that’s why Kaspersky is still associated by some with “antivirus software”. But actually, detecting and neutralizing malware based on an antivirus database is today just one of our security technologies: over a quarter century we’ve added to it a great many others. The word antivirus today is more of a metaphor: it’s known, understood, and thus is a handy (if not too accurate or up-to-date) label.
But what are we supposed to do if we need to tell folks about complex, multifunctional protection for enterprise IT infrastructure? This is when strange sets of words appear. Then there are all the abbreviations that come with them, whose original idea was simplification (of those strange sets of words) but which often just add to the confusion! And with every year the number of terms and abbreviations grows, and memorizing them all becomes increasingly… tricky! So today, let me take you on a brief excursion of all this gobbledygook some of these complex but necessary names, terms, descriptions and abbreviations – so that, hopefully, we achieve the thing the abbreviations themselves struggle with: bringing clarity.
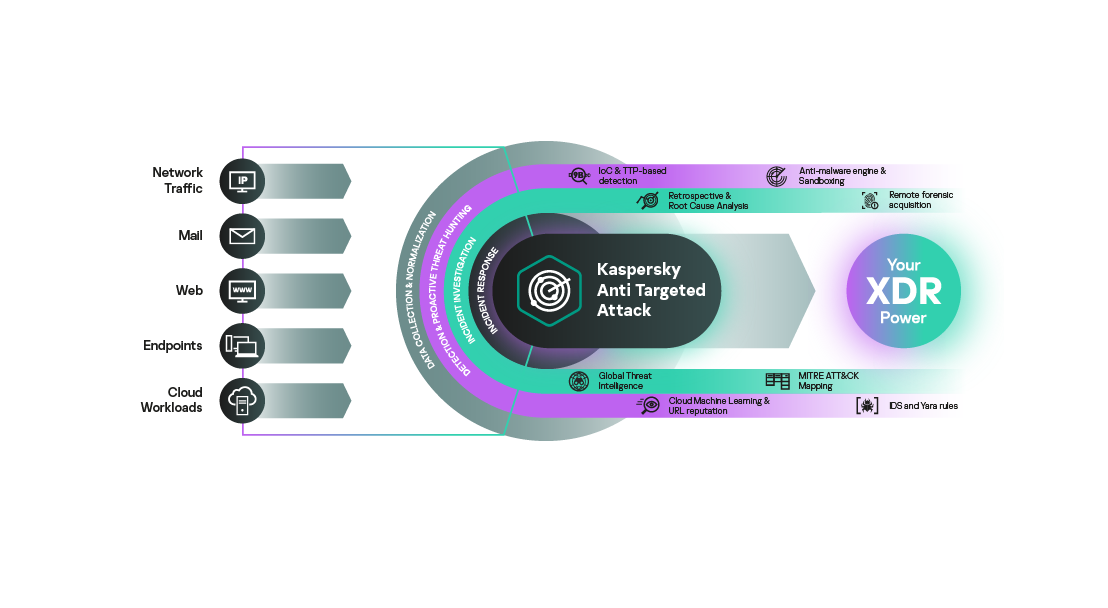
From EPP to XDR
Ok. Back to the boat; rather – “antivirus”…
The more accurate name for this class of products today is Endpoint Protection or Endpoint Security. After all, as stated above, it’s not only the antivirus that’s protecting endpoints these days, but a collection of security measures. And sometimes the varied endpoint technologies are given an updated name – including the word “platform”. Somehow that sounds more appropriate, and more accurately descriptive; it also seems fashionable, as is its abbreviation: EPP (Endpoint Protection Platform).
The Endpoint Protection Platform is, in essence, a concept that dates back to the 1990s. It’s still needed, but other methods are required for quality protection of distributed infrastructure. Data needs to be collected and analyzed from the whole network to detect not only singular incidents, but also whole chains of attacks, which aren’t limited to a single endpoint. Threats need to be reacted to across the whole network – not just one computer.
Fast-forward a decade or so, and in the early 2000s there appears a class of products called SIEM – security information and event management. This class of products is made up of tools for the collection and analysis of all infosec telemetry from various devices and applications. And not only for today: a good SIEM can pull off retrospective analysis – comparing events from the past and uncovering attacks lasting many months or even years.
So, by this stage (the early 2000s for those at the back not paying attention) we’re already working with the whole network. But there’s no “P” for “Protection” in SIEM. So the protection was provided by the EPP (Endpoint Protection Platform; you at the back – detention after school). However, EPP doesn’t see network events; for example, it could easily miss an APT (advanced persistent threat).
Therefore, in the early 2010s, along comes another abbreviation to fill the gap and cover both security functions: EDR (Endpoint Detection and Response). On the one hand, EDR provides centralized monitoring of the whole IT infrastructure – allowing, for example, to compile traces of attacks from all hosts. On the other, an EDR-type product uses for detection not only EPP methods, but also more advanced technologies: correlational analysis of events and the picking out anomalies on the basis of machine learning and dynamic analysis of suspicious objects in a sandbox, plus assorted other threat hunting tools to assist in investigation and response.
And when we do EDR ourselves here at K, of course we need to put our stamp on it, which we do, giving us… KEDR.
So far, so good great. But… there’s no limit to perfection!
Fast-forwarding again, this time to the early 2020s, and a new abbreviation is introduced and quickly becomes all the rage in the cybersecurity industry: XDR (eXtended detection and response). This, basically, is EDR on steroids. Such a system analyses data not only from endpoints (workstations), but also from other sources – for example the mail gateways and cloud resources. Which totally makes sense, since attacks on infrastructure can come in via any and all kinds of entry points.
XDR can be even further enriched in terms of its expertise by further data from (i) threat-analysis services (ours is called TIP (Threat Intelligence Portal)), (ii) network-traffic analysis systems (ours – KATA), and (iii) security-events monitoring systems. Such data can also come in via similar services provided by third-party companies.
XDR’s response capabilities are also advanced. More and more protective actions are becoming automated where before they were all done manually. And now the security system can itself respond to events based on cunning rules and scenarios input by experts.
Complicate or simplify?
I hope it’s clear by now that any EDR or XDR system represents a large, complex collection of technologies. However, the functionality of different providers’ EDRs or XDRs can differ greatly. For example, each provider determines what and how much their experts input into an EDR/XDR to better reflect and thus repel modern-day attacks. So, though they’re all called EDR/XDR, they’re by far not all the same.
For example, on the Kaspersky XDR platform, besides the listed-above XDR capabilities there’s also a module providing interactive training for raising client-companies’ employee cyber-literacy. And no other XDR does such a thing! Surely that’s a good reason to cheer if not boast?…
Actually, sceptics may not be cheering. They might say that if we add simply everything we’ve got to enterprise protection – kitchen sink and all – won’t this simply be too much? A morass that becomes too complex, cumbersome, and hard-to-understand and master. “Whatever next?” they think. “Marketing types coming up with YDR next year, then ZDR the year after that?!”
Ok, we get it. And we listened to our customers too. And over the years we’ve come to realize that in enterprise cybersecurity, by far not all companies need everything plus the kitchen sink. Often, more up their street we’ve found is a basic set of EDR tools plus clear and convenient instructions on how to use them. This is especially the case for small and medium-sized businesses with small teams of infosec specialists.
So what have we done to meet these more essential needs? We’ve come up with our new and improved KEDR Optimum: “advanced detection, simple investigation and automated response in an easy-to-use package to protect business against the latest threats”. For example, in its new alert cards, besides detailed descriptions of suspicious events and threats, there’s also now a Guided Response section. This gives step-by-step recommendations for investigation and response regarding discovered threats:

Recommendations like this have been prepared based on the decades of dedicated work of our leading experts, and come in the form of links to detailed descriptions of protective procedures. This not only raises reaction speeds, it also allows infosec specialist trainees to boost their skills, for example – with interactive pop-ups:

Another thing KEDR Optimum can now do is keep an eye on infosec specialists possibly inadvertently blocking this or that critical system object. After all, malware can sometimes launch using legitimate operating system files – and blocking such files can hinder the operation of the whole IT infrastructure. With KEDR Optimum – you’re covered.
And finally, I must mention just one other thing about KEDR Optimum. All the above was written by me – Mr. K. Prefer something more impartial? Be my guest! Head on over to independent testing laboratories to see what they think. For example: IDC, Radicati and SE Lab. There. 100% transparent and fair (and a rhyme too:).

