June 23, 2022
Big-league cybersecurity’s 3 ingredients: analyzing the past, testing the present, and predicting the future. Any extra ingredients = filler.
When the past is studied carefully, a detailed and precise picture of the present can be formed; then, the expert’s analytical mind (better – lots of experts’ analytical minds) can warn about – even predict – the foreseeable future. This is precisely how we here at K can often guess predict accurately how the upcoming evolution of digital maliciousness will pan out. It’s also how we keep abreast of the latest cyberattack trends, which allows us to timely develop the corresponding technologies needed in the fight against the cyber-unpleasantnesses around the corner. There’ve been times when we were mistaken in this expertise-based cyber-prophecy of ours: some types of cyber-awfulness is pretty hard to predict at all – but those instances have always been the exception to the rule; more often than not we’ve been bang on the money.
So how do we manage it? Is it just bearded geeky super-brainy types who do all this analysis and cyber-prophesizing? Actually – no. A lot of it is automated. And that’s to be applauded: a human – no matter how brainy – can’t compete with today’s computing power and algorithms and robots and AI machine-learning. The brainy human is still needed, of course; but why do all the heavy-lifting alone?
It’s the heavy-lifting that I’ll be telling you about today in this post. Technological, science-based heavy-lifting that allows us to predict the future (no mystical fortune-telling à la Baba Vanga:).
Let me start off by telling you about the evolution of our Threat Intelligence Platform (TIP).
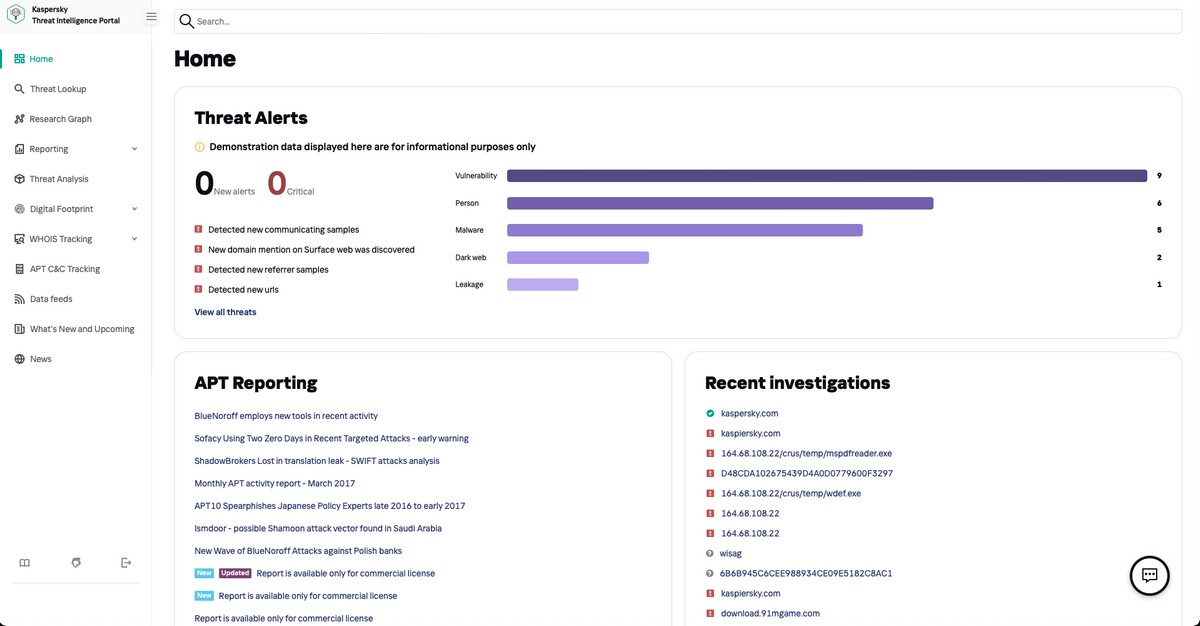
I’ll break it down just like in the title: how we analyze the past, test the present, and then we crystal ball predict the future…
Analyzing the past
When we just starting out developing this service, back in 2016, its first tools dealt with analysis of the past. These were (and still are) its Threat-Data Feeds. As the name suggests, these are feeds of data about already-known-about threats: attack indicators, malware website addresses, botnet control-center addresses, and a lot more besides. You can sign up for them to receive updates in real time.
A step up from the feeds, there are our detailed threat reports. Examples: analytical reports on APT-threats dedicated to targeted attacks and hacker groups; Crimeware Intelligence Reporting, which describes new variants of malicious programs; and ICS TI Reporting – on new threats against industrial control systems.
And since we’re hardly ever going to throw away any of the data we’ve collected over the last quarter century, we now have petabytes sillybytes zillybytes worth of threat data stored away. Seems a shame to keep it locked up, so we decided to give clients (clearly here we’re talking corporations/enterprises – the IT/IT-security departments thereof) the ability to search our database themselves. And that’s how our Threat Lookup service, kind of a Google Threats, came to be. And it’s already used by hundreds of well-known and highly-esteemed companies from all over the world.
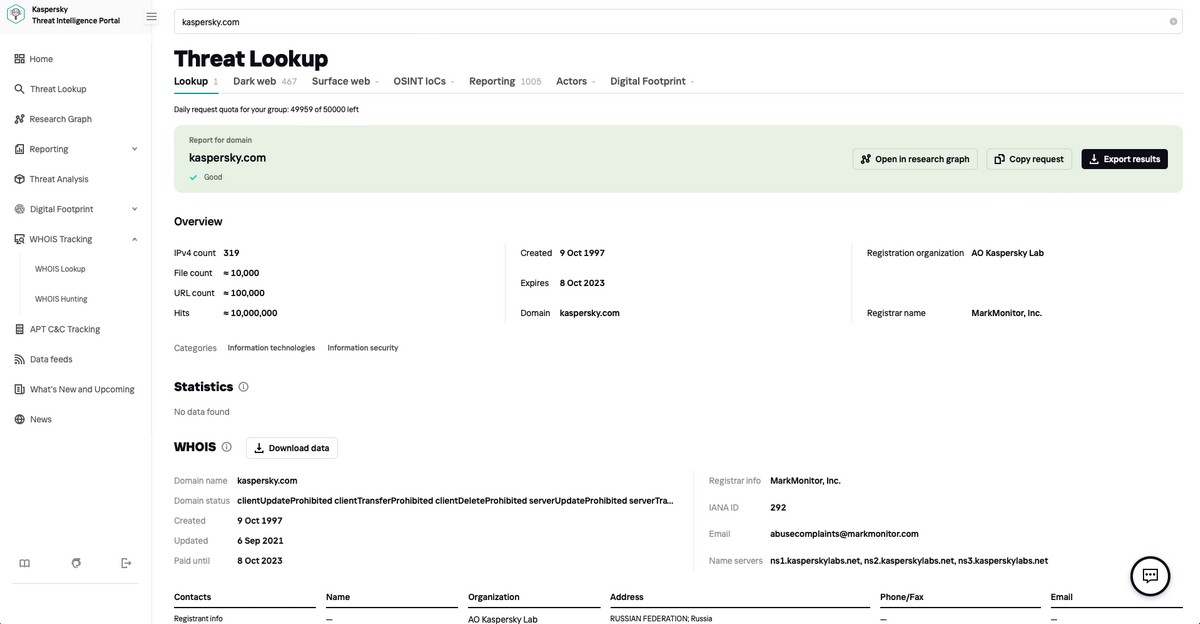
Testing the present
Logically, we turn now from the past to the present…
Imagine that, this morning, you found a suspicious file somewhere on your corporate network and you need some analysis of it pronto. This means your threat intelligence (TI) platform needs to provide investigation tools, in the words of Fatboy Slim, “right here, right now”.
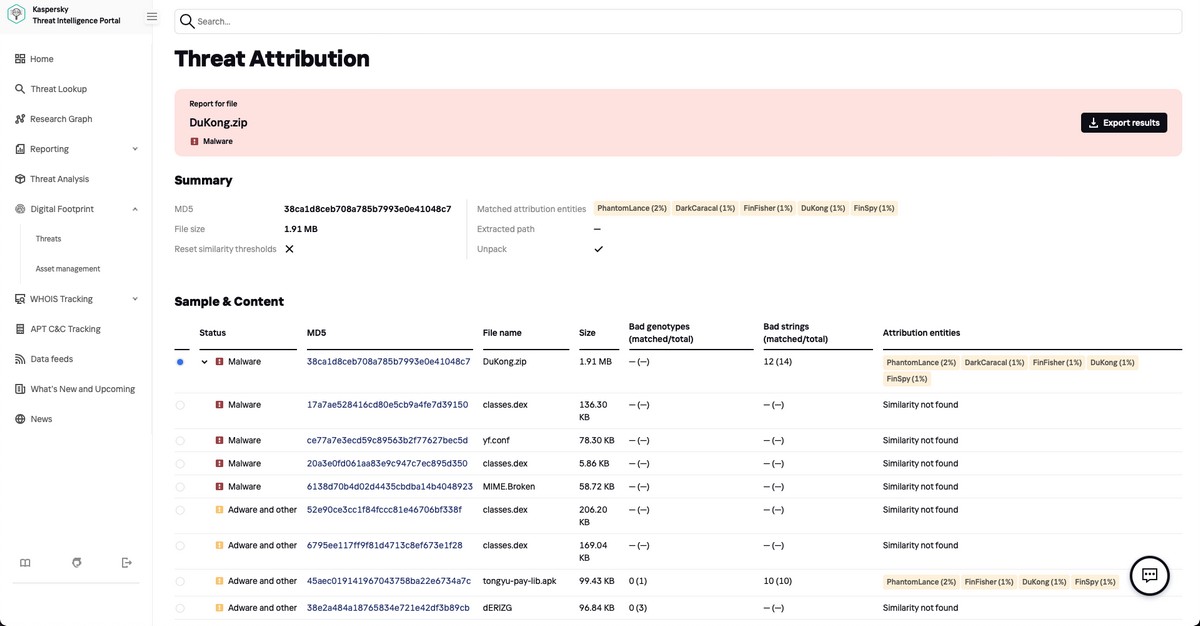
First up, you’d need static code analysis. We’ve had this one covered since way back in the day when starting out with classic methods of antivirus (hashes, heuristics), which over the years morphed into a cutting-edge threat-attribution system. It’s now able to work out the origin of malware even if it’s a largely rewritten version of previously-known malware.
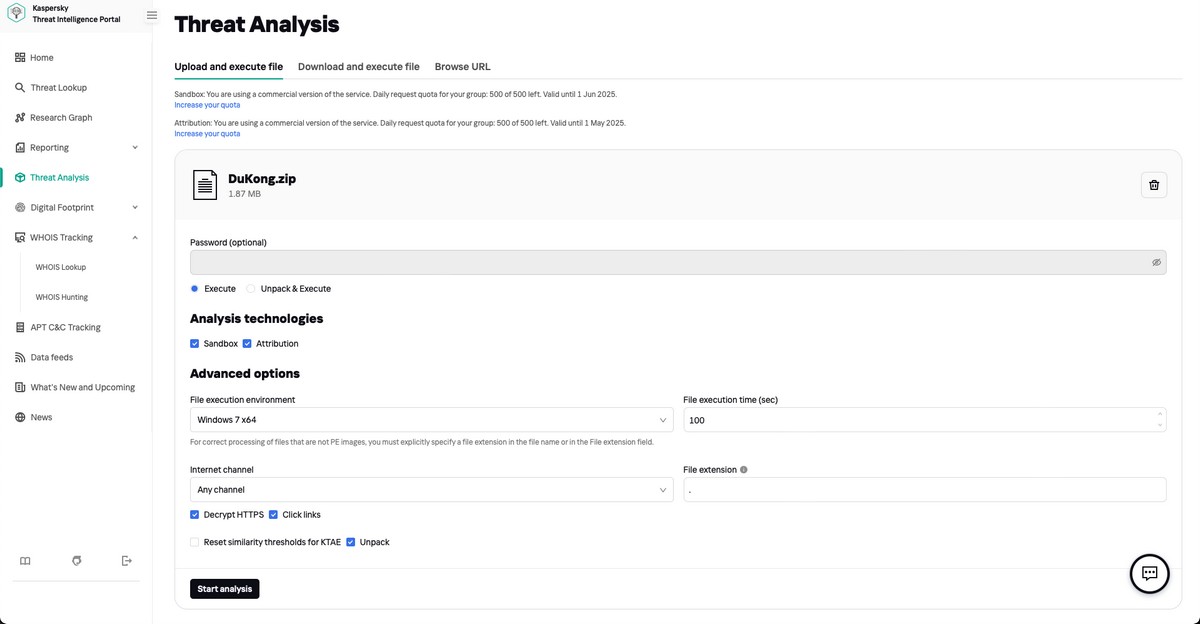
You see, certain “genes” – distinguishing pieces of computer code – are kinda like specimens of a hacker’s signature, and so remain unchangeable. And it’s such genes that are caught out by our Threat Attribution Engine, which has been trained to recognize the hundreds of millions of both bad and good genes that we’ve been saving up over the last 25 years. The result is being able to tie new malware to known authors.
Does it seem we’re still in the past? Then we toss the suspicious file into our Cloud Sandbox. This is literally “present continuous” dynamic analysis of a file upon its execution in an isolated environment. Judging just by its code, it could appear to be completely innocent; but run in the sandbox… uh-oh: it’s trying to encrypt something! Who would have thought it? As malicious as they come, after all!
Now comes the question – where did this maliciousness come from? And should we look around its vicinity to see if there’s anything else lurking about? You guessed it: yes, we should!…
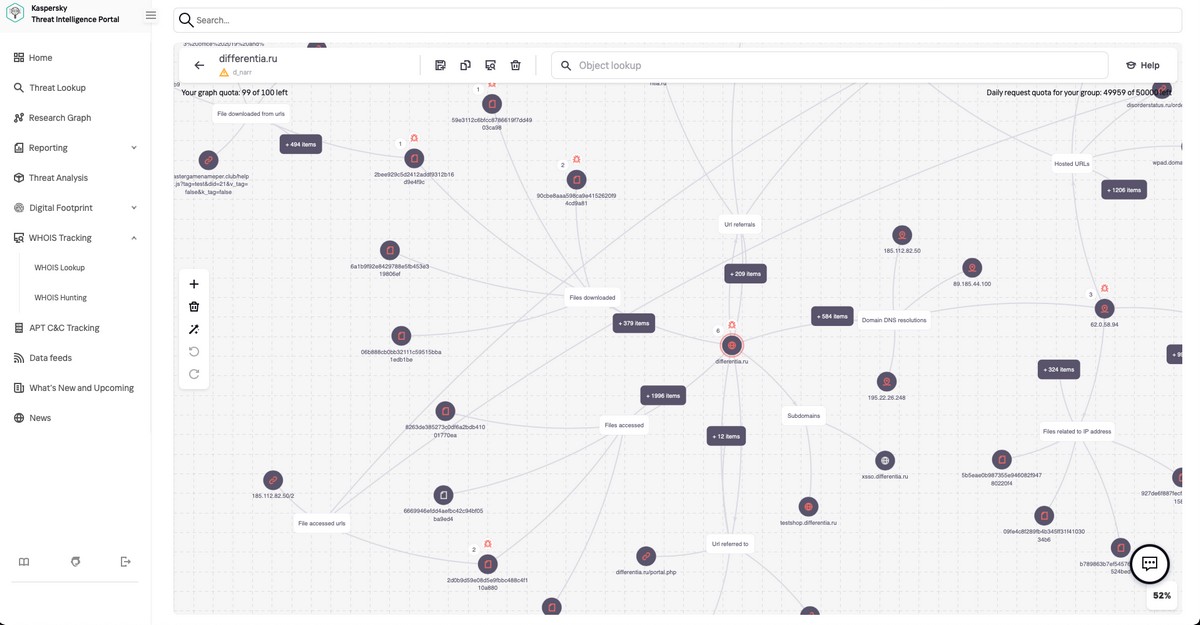
To do so we check out our Research Graph, where we see the relations of the investigated file with other objects: domains with which it interacted, files that it loaded – or that loaded it – and also connections with other threats and indicators listed in our database. These indicators can be then be searched for by the customer itself on the internet – just to make fully sure that nothing’s been missed and that the bad guys are well and truly expelled.
Predicting the future
So, we’ve used knowledge of the past to investigate something that’s occurred in the present. But where’s the future? Of course, it hasn’t occurred yet – but we can already see signs of what it’s gonna look like. And it resembles things like weak points in your infrastructure’s protection, vulnerabilities in software and settings, and potential entry points for cyberattacks. Such things can be found out about in the above-mentioned subscription-based reports (Threat Intelligence Reporting). It’s in these where we describe in detail which hacker groups exist on the planet and – most importantly – what tools they use, how they use them, and for what objectives (that is, we uncover their TTPs – tactics, techniques and procedures). Knowing all this, one can prepare for potential future attacks much better.
However, the bad guys’ methods can differ given different contexts, and our clients often ask us for further data on how certain attack techniques can be applied in specific situations that are typical for a given client. And now they can get such consultations with analysts in real time via our Ask the Analyst service.
The second type of signs regarding the future is suspicious activity “somewhere on the internet” that uses an organization’s data, which can be regarded as planning for an attack. And it is particularly these signs regarding the future that our Digital Footprint Intelligence (DFI) service is dedicated to.
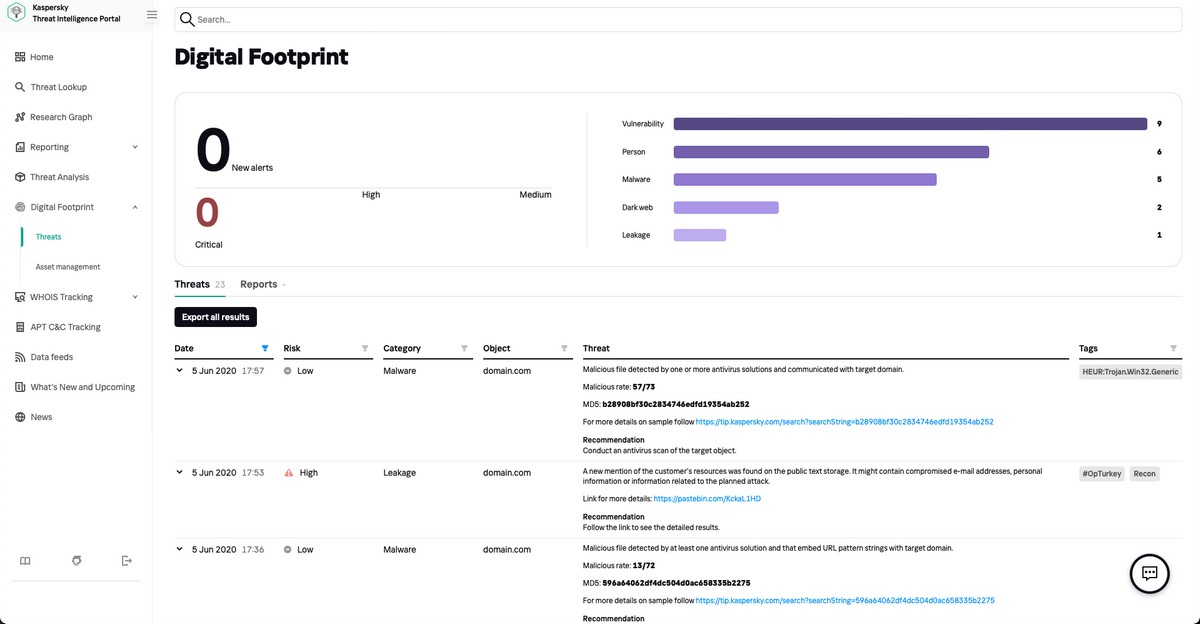
It works like this: with the help of dedicated robots, a team of our experts makes up a “digital portrait” of the given organization, and then it tracks how this data is used on the internet to be able to predict possible attacks.
For example, someone registers a domain that closely resembles that of a given company (say, with just one letter different, or with a dash added somewhere), and launches a site with this address that looks very much like the “original”. The DFI service will warn you about such phishing sites, and the Takedown Service will assist with swift blocking of the copy-cat site.
Besides, in the new version of our TI portal there’s now a specialized internet search function. Thus, what you’d find earlier in our internal threat database is now complemented by fresh data from checked open sources, including cybersecurity media, information security forums, and experts’ blogs.
And finally, our TIP can be used to search the murkiest corners of the web (Dark Web, Deep Web). You can check if an organization’s data has been leaked, see if there’s been chatter regarding an organization’s vulnerabilities, and check up on other signs of preparations for attacks. And the dark/deep webbers thought they were untrackable? Yeah, right!
But, you may be thinking… “Can it flag a future hacker based on his/her teenage gait?!” Or: “Can it tell how system administrator X will organize company Y‘s data leaks in three years time?!” Or something like that). Of course the answer is no. What we can do is give the users of our analytical platform the most important information about the threats they may realistically come up against: by whom and why they may be attacked, how such attacks may be implemented and how they can protect themselves from them.
So there you have it folks – time-machine cybersecurity – with the past, the present, and the future all Kovered! But despite such sci-fi wording, I do hope that you see now how this is anything but science fiction. Not Vanga, not Sauron, not a shaman, not a fortune-teller, not astrology, not magic. Science and technology only – 100%.
Who would have thought you need to analyze the past, investigate the present, and predict the future for top-notch cybersecurity in 2022? We cetainly would – and do, with our Kaspersky Threat Intelligence. And now you can.


