May 23, 2022
Cyber-enlightenment: how to effectively catch out the wolves in sheep’s clothing; or – it’s never too late to learn.
Hi folks!
We all know perfectly well that the internet is awash with all kinds of malware – from the primitive amateur-grade to the sophisticated pro-grade. And over the last three months things have gotten a lot worse. The cyberswine are becoming all the more daring, and their methods – all the more advanced and refined. And though battling the cyber-baddies is both worthy and wholly necessary, prevention is always better than cure.
That is, being able to recognize cyber-evil for what it is and in good time is a task of vital strategic importance; all the more so when we’re talking not simply about protecting businesses, but about protecting critical infrastructure – the kit that provides us with the safe, comfortable and stable conditions in which to live.
Accordingly, educating employees how to spot cyberattacks on corporate networks is real important. And yes, we’re the world’s biggest fans of such cyber-enlightenment: we regularly conduct trainings of all different kinds – and also formats: both online (including in real time) and offline, and all under the caring and attentive gaze of our experts.
Not so long ago I wrote on this here blog of mine about our training programs on identifying cyberattacks based on sets of malware characteristics (you can read more about YARA rules here). But here at K, we never stand still, so we’ve gone and upgraded, and today I want to tell you about our new course, which has just been added to our educational portfolio of online training for experts.
So here it is folks – introducing… training on how to respond to (Windows OS) incidents (including ransomware) – the Kaspersky Windows Incident Response course. Btw, earlier this course existed only in offline format and was the most popular among our customers; however, it’s intended for internal teams just as much as for independent cybersecurity specialists who want to further improve their knowledge and raise their qualifications.
Now, according to recent research, top managers of (non-IT) companies, and also owners of businesses seem to overestimate their ability to deal with ransomware – especially if they’ve never come across the problem. And ~73% of companies aren’t able to cope with a ransomware attack even with the help of their IT service contractors. Yes – that’s plenty!
So, why is this new course so amazing?
Well, the program was developed by our GERT (Global Emergency Response Team) (not to be confused with our GReAT:), which has over 12 years of experience in incident response:
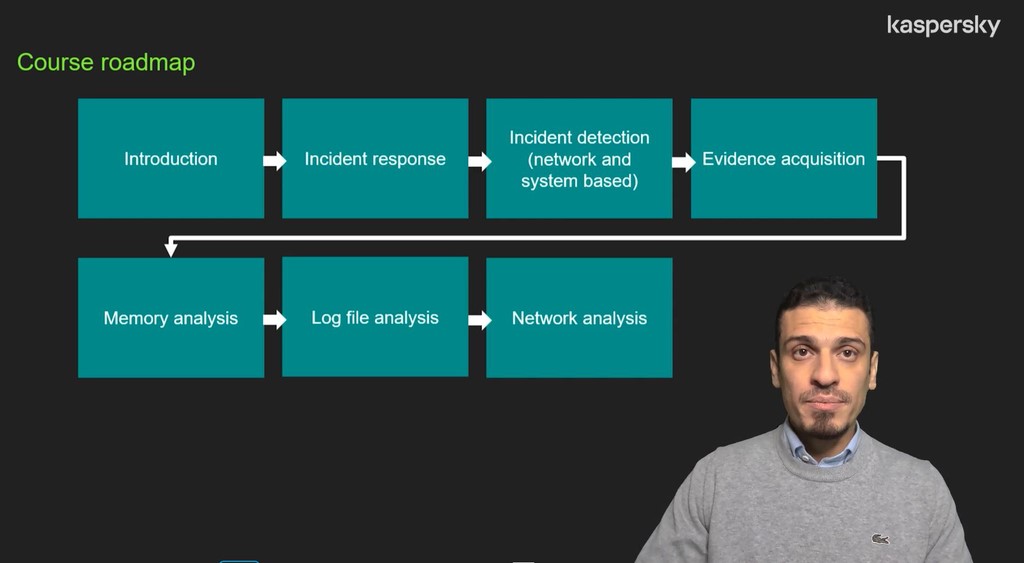
Practical tasks are emphasized on the course, and its main feature is the development of skills using a real incident – the REvil ransomware attack.
What can be expected as a result? Cybersecurity specialists will know how to identify and respond to cyber-incidents, be able to differentiate APTs from other threats, and will have studied various methods and anatomies of targeted attacks through a cyber kill chain. Participants will master security-incident investigations, learn how to collect evidence, analyze logs of (i) operating systems, (ii) security-perimeter network traffic, and (iii) memory contents; determine indicators of compromise, and much, much more…
Students will be given access to a modelled virtual working environment with all the necessary tools for developing their skills.
The program is basically chockfull of really useful, practical know-how, and super interesting for its intended audience. More details, including how to apply, can be found here.
So there you have it folks – serious, upgraded training for the serious business of fighting advanced threats to businesses and infrastructure. All aboard… – the cyber-train (to a safer world through top-notch cybersecurity) will be leaving soon!…


