March 30, 2022
Cybersoft IP vs K: yet another win against patent trolls.
Despite these hard times, we continue our work to save the world from all manner of cyber-maliciousness. Therefore, we’re not staying silent ->
Hi everyone!
Regular readers of this here blog of mine will have noticed how it’s been ages since the last time the patent-trolls tag has been put to good use (the last such post was about our victory against Uniloc, way back in March 2020 – yes, just as worldwide lockdowns were kicking in for the first time). Well, here, today – time for some patent-troll catch-up. And thank goodness, it’s good news – something that’s all the more appreciated these days…
We recently came to the end of a year of litigation proceedings with the U.S. patent troll Cybersoft IP, LLC. So that’s good news there. The even better news: we won!
So what did this particular troll want? What was its claim against us?
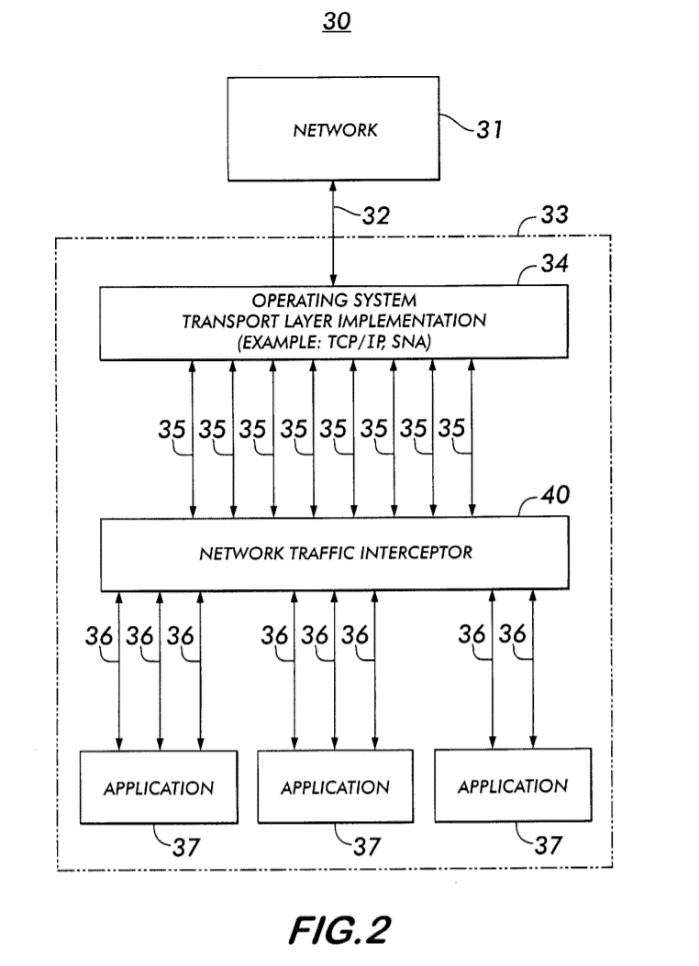
Well, it filed a lawsuit against us in April 2021 in the District Court of Massachusetts. In it, the troll took issue with our wonderful Kaspersky Secure Mail Gateway, claiming it infringed its patent (US6763467B1) covering a ‘network traffic intercepting method and system’ (specifically – network security technology that checks data transferred via a network (in particular, in emails and their attachments) on a user’s device).
The patent is for a method conducted within a single computer system connected to a network for intercepting, examining, and controlling all data – without exceptions – flowing via transport connections between the transport layer of an operating system and user applications, where the intercepted data is checked to see whether it can be scanned for unwanted content.
Basically, the patent relates to something resembling a personal firewall on a user’s computer device that intercepts and scans network data. The description of the patent, its claim, and also its figures [diagrams] all clearly confirm this. Thing is… such network-traffic filtration tech installed on a user’s device is not only well-known and widely-used tech – it’s also been available in the cybersecurity industry for years.