November 2, 2020
OpenTIP, season 2: drop by more often!
A year ago I addressed cybersecurity specialists to let them know about a new tool we’d developed – our Open Threat Intelligence Portal (OpenTIP). Tools for analysis of complex threats (or merely suspicious objects) – the very same ones used by our famous cyber-ninjas in GReAT – became accessible to anyone who wanted to use them. And use them lots of folks wanted – testing zillions of files every month.
But in just a year a lot has changed. Things have become much more difficult for cybersecurity experts due to practically the whole world having to work remotely because of coronavirus. Maintaining the security of corporate networks has become a hundred times more troublesome. Time, which was precious enough as it was before corona, has become a highly precious resource. And today the most common request we get from our more sophisticated users is simple and direct: ‘Please give us API access and increase rate limits!’
You asked. We delivered…
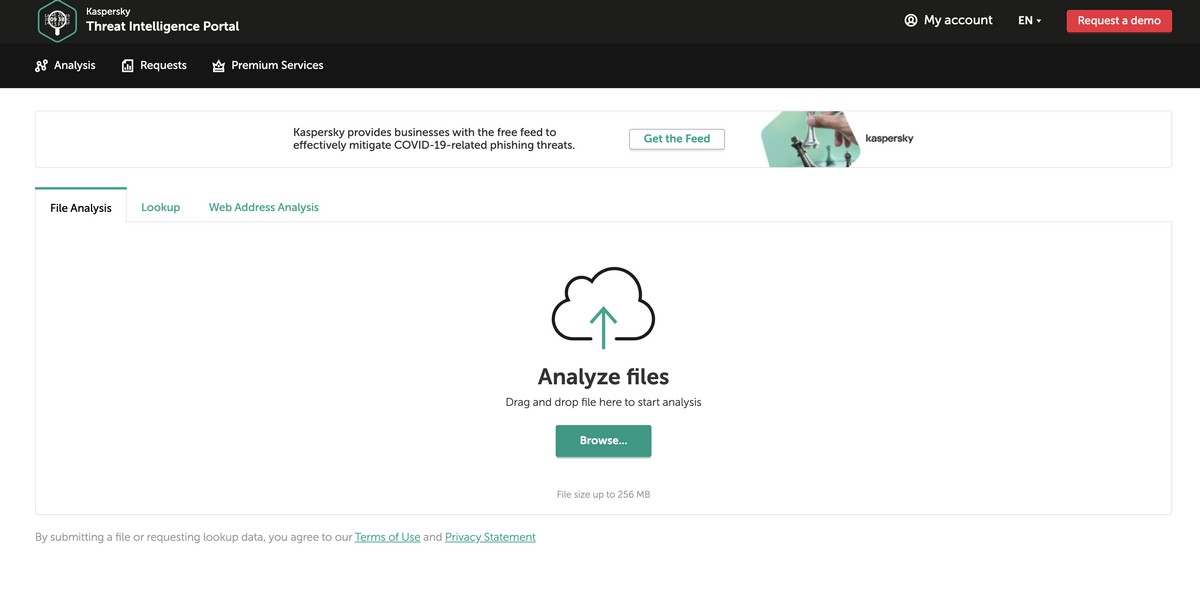
In the new version of OpenTIP there’s now user registration available. And I highly recommend regular visitors do register, since when you do a large chunk of the paid Threat Intelligence Portal turns up out of the ether.
First, sending artefacts for testing can done via the API. You can integrate OpenTIP into your analysis processes whichever way you consider is quicker and more convenient. And besides unlimited quantities of files, you can also test other suspicious artefacts such as URLs, IPs and hashes.
Second, when we’re talking an executable file, besides the verdict about what specifically in it seems to be suspicious, OpenTIP now supplies more raw material for analysis. By this I mean data about the structure of PE-files, and also text strings extracted from them. It’s possible to periodically use our super cool cloud sandbox, which is actually a paid product in its own right. And finally, in the settings appears a ‘Private submission’ button, permitting a check of artefacts without telling anyone about the fact that they were submitted into OpenTIP. We didn’t allow anyone to watch others’ files from the very beginning, but now it’s possible not to send tested portal indicators to the public history.
Even without registration, OpenTIP improvements will be noticeable.
There’s the more convenient web interface, which saves time and is very easy on the eye ); while the analysis results will be much more informative.
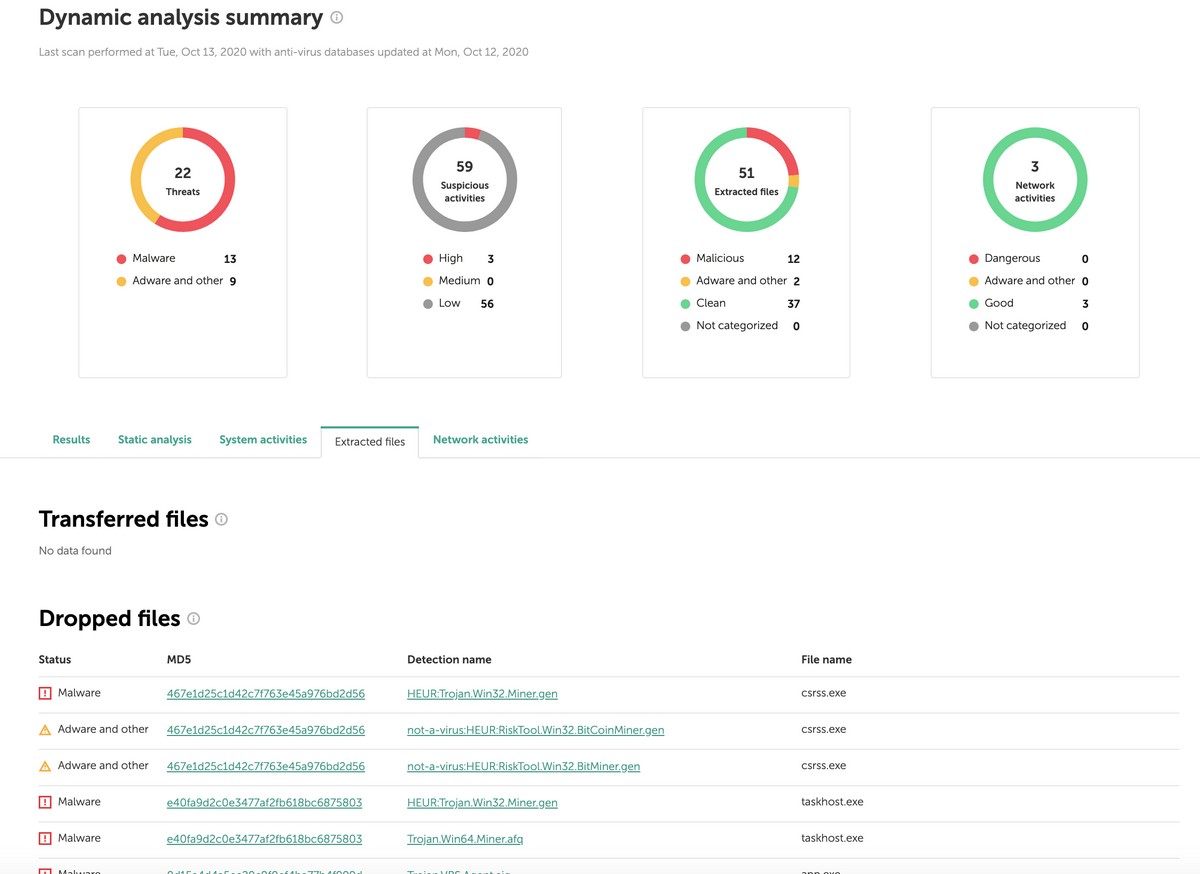
In this second version of OpenTIP we’ve applied extra technologies of behavior analysis. And let me say it again: this isn’t simply a verdict of ‘infected/clean’, like with traditional endpoint protection, but a detailed analysis of suspicious properties, on the basis of which an analyst takes a decision about whether to dig further. For suspicious URLs, categorization of dangerous properties will be also available.
For those needing even more, there’s a paid version of the Threat Intelligence Portal, which is much richer – in part because of the detailed reports on detected cyberthreats written up by our top analysts it gives access to.
But enough reading these abstract descriptions already! Best is to have a go for yourself. Simply throw a suspicious file at OpenTIP. For those who aren’t subscribed to our Threat Intelligence services, the portal will be indispensable (yes, I remember about Virustotal, but I talked about that in my last post on Open TIP). But OpenTIP will be useful most of all to those who’ll adapt it to their daily processes of analysis of all manner of cyber-nastiness.


