June 3, 2020
Cyber-tales update from the quarantined side: March 92, 2020.
Most folks around the world have been in lockdown now for around three months! And you’ll have heard mention of a certain movie over those last three months, I’m sure, plenty; but here’s a new take on it: Groundhog Day is no longer a fun film! Then there’s the ‘damned if you’re good, damned if you’re bad’ thing with the weather: it stays bad and wet and wintry: that’s an extra downer for everyone (in addition to lockdown); it gets good and dry and summery: that’s a downer for everyone also, as no one can go out for long to enjoy it!
Still, I guess that maybe it’s some consolation that most all of us are going through the same thing sat at home. Maybe. But that’s us – good/normal folks. What about cyber-evil? How have they been ‘coping’, cooped up at home? Well, the other week I gave you some stats and trends about that. Today I want to follow that up with an update – for, yes, the cyber-baddies move fast. // Oh, and btw – if you’re interested in more cyber-tales from the dark side, aka I-news, check out this archives tag.
First off, a few more statistics – updated ones; reassuring ones at that…
March, and then even more so – April – saw large jumps in overall cybercriminal activity; however, May has since seen a sharp drop back down – to around the pre-corona levels of January-February:
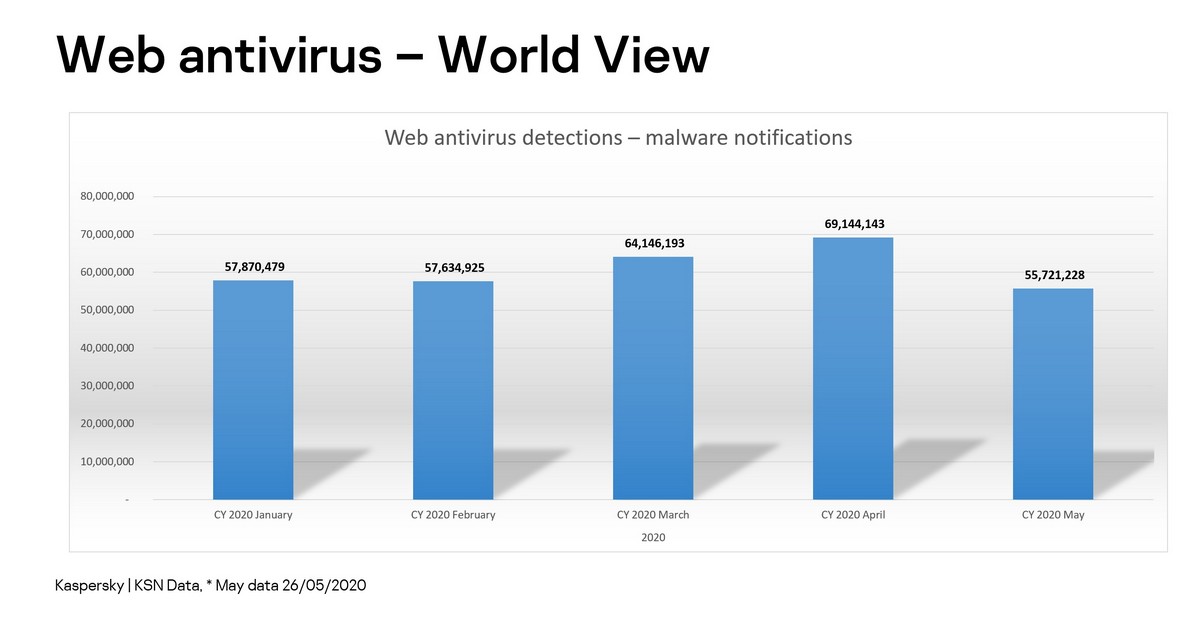
At the same time we’ve been seeing a steady decline in all coronavirus-connected malware numbers:
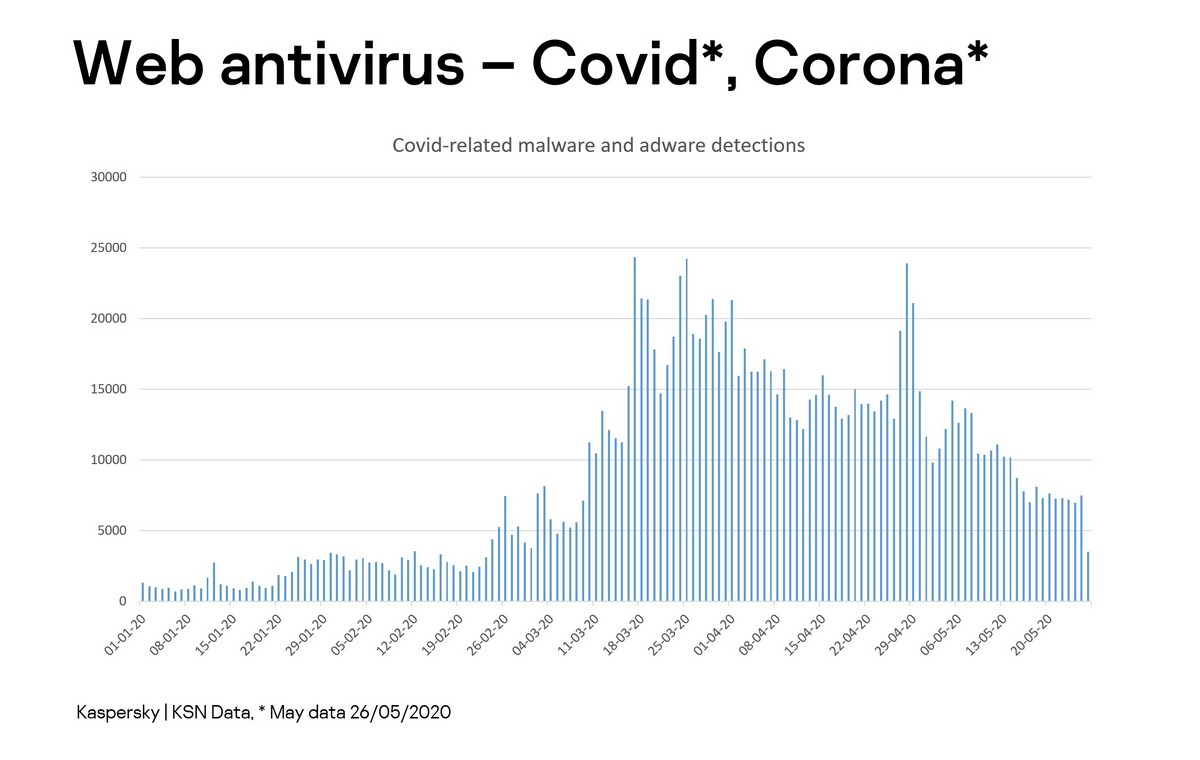
// By ‘coronavirus-connected malware’ is meant cyberattacks that have used the coronavirus topic in some way to advance its criminal aims.
So, it would appear the news is promising. The cyber-miscreants are up to their mischief less than before. However, what the stats don’t show is – why; or – what are they doing instead? Surely they didn’t take the whole month of May off given its rather high number of days-off in many parts of the world, including those for celebrating the end of WWII? No, can’t be that. What then?…
Alas, I don’t know. They don’t tell me about their criminal business plans. However, I do have my own hypothesis: perhaps they overdid it so much in April that they had to take time-out in May to analyze their ‘catch’ – masses of data – which takes time to sift through and monetize properly. It’s only a guess, but possible.
Thus, I do think it’s too early to let our guard down in any way, thinking things have gone back to ~’normal’. Cyber-villains have always hacked, still hack, and will continue to hack. And all different kinds of hacks are still exploiting the coronavirus panic-pandemic-lockdown theme to assist them in their bad deeds. For example, many APT groups have been using it in their phishing emails. But there are a several particular uses of corona (actually, some don’t use it) that need specially highlighting:
For example, the Transparent Tribe group (about which we recently wrote an APT report), which specializes in attacks on Indian companies, the public sector and military institutions, has recently gone one further in its badness. They’ve been pretending to be the official Indian coronavirus trace-and-tracking app – which must be installed on all devices in the country – so as to distribute Android backdoors. And it looks like they’re pinpointing military figures.
On April 20 on the 4chan forum a post was published about a leak of logins and passwords from the Wuhan Institute of Virusology. Shortly after, many posts on various social media platforms were sharply trending (and also much media coverage) all about alleged data leaked not only from the Wuhan Institute, but also from the WHO, World Bank, Gates Foundation and other organizations. Our own internal investigation of the leak found that most of the data was compiled from leaks from years ago. Moreover, the information presented about this leak on various forums was mostly described as presumed proof of the theory about intentional spreading of SARS-CoV-2 / COVID-19 among the population. On the whole it looks like real fake (!) news with political undertones. But I’ll pass on the ‘who may be behind it and why’ conjecture ).
The next bit of news isn’t directly connected to coronavirus; however, many of the supercomputers that were hacked were being used to research COVID-19 and so that research was slowed. Anyway, it goes like this…
Simultaneously, several supercomputers across the world were hacked one day in early-mid-May. There was the Archer in Edinburgh, the German bwHPC, the Swiss National Supercomputing Centre (which is currently analyzing the coronavirus protein), and many more across Europe, North America and China. Our analysis showed how the cybercriminals used a backdoor and then used it to… mine cryptocurrency! All that superhacking of supercomputers just for that? Surely not. What with mining being hardly the most profitable field of cybercrime these days, the question remains – what were they really up to? A test-run for something a lot bigger to come? And once again, the who and why remain a mystery.
Interesting research published in Forbes claims that Xiaomi smartphones have been sending all users’ internet links and searches, together with metadata about their devices, to… the servers of Alibaba! Yep, the researcher installed his own browser onto his phone and that’s what he discovered. Xiaomi of course denies everything, but still followed up by promising a software update and adding a checkbox for users to opt out of data being sent.
And finally, here’s another company whose reputation recently took a knock due to security issues – Zoom. The issues were so blatantly bad I decided to only use its software (since lockdown started) on an ’empty’ computer, and then only when I really had to. Still, you have to hand it to Zoom – in two months they really have turned things round. With each patch they improve security, and they’ve launched a good bug bounty program (managed by Katie Moussouris, who’d introduced such a program previously at Microsoft). And just lately Zoom announced that it’s buying the Keybase crypto-service to protect transferred data. Thus, I hope Zoom will become a good example of how a good attitude to security leads to business success – and its software even finding its way onto my ‘combat’ laptop ). Respect to Zoom!
And that’s about it for today for tales from the quarantined-92-days-of-March side. As and when more cyber-tales from the lockdown front arise – I’ll be bringing you updates thereon not long afterward. And now… back to work!…




