May 27, 2016
Darwinism in IT Security, Pt. 3: Time to Deal with These No-Good Parasites.
Hi all!
On a bit of a roll here on the survival-of-the-fittest-in-IT theme. Wasn’t planning a trilogy… it just kinda happened. Sort of…
…Sort of, as, well, the specific problem of parasites in the IT Security world I’ll be writing about today has been at the back of my mind for a long time already. This Darwinism talk seemed the perfect opportunity to finally let rip. You’ll see what I mean…
Today folks: parasites. But not those we’re fighting against (the ‘very’ bad guys); those who claim are also fighting the very bad guys (philosophical question: who’s worse?).
The IT industry today is developing at a galloping pace. Just 10-15 years ago its main themes were desktop antiviruses, firewalls and backups; today there’s a mass of new different security solutions, approaches and ideas. Sometimes we manage to stay ahead of the curve; sometimes we have some catch-up to do. And there are other times we fall into a stupor from astonishment – not from new technologies, innovations or fresh ideas, but from the barefaced brazenness and utter unscrupulousness of our colleagues in the security industry.
But first, let me explain how events have been developing.
There’s a very useful service called the VirusTotal multiscanner. It aggregates around 60 antivirus engines, which it uses to scan files and URLs folks send it for malware checking, and then it returns the verdict.
Example: Joe Bloggs finds a suspicious application or office document on a hard drive/USB stick/the Internet. Joe’s own antivirus software doesn’t flag it as containing a malware, but Joe is the paranoid type; he wants to make really sure it’s not infected. So he heads over to the VirusTotal site, which doesn’t have just one antivirus solution like he does, but ~60. It’s free too, so it’s a no brainer. So Joe uploads the file to VirusTotal and gets instant info on what all the different AVs think about it.
First of all, to clarify: both the folks at VirusTotal and those at VirusTotal’s owners Google are firmly on the ‘good guys’ side. They have no connection with parasites whatsoever. VirusTotal is run by a very professional team, which has for years been fulfilling the task at hand extremely effectively. (Still need convincing? How about VirusTotal winning the MVP award last year at the Security Analyst Summit (SAS)?) Today VirusTotal is one of the most important sources of new malware samples and malicious URLs; and also a very cool archeological tool for researching targeted attacks.
Recognizing VirusTotal for enduring contribution to security research #SaveTheWorldMVP #TheSAS2015 pic.twitter.com/lZTjN30Xwg
— J. A. Guerrero-Saade (@juanandres_gs) February 16, 2015
The problem lies with a handful of shady users of the multiscanner who, alas, are becoming more and more unblushingly unabashed in how they conduct themselves.
Besides the free, open, public service, VirusTotal has a paid subscription service to a turbo-charged private API, which allows for real-time automatic checks of unlimited quantities of files. And here is where things get interesting – for all the wrong reasons: it’s where IT-security parasites tend to hang out.
They have one look at everyone’s verdict and then adopt it as their own – aka copying – even going so far as also using the unique names of verdicts too! So what we get is one set of companies does all the work, while the other set gets the fruit of those labors, dresses it up in impressive scientific-sounding marketing buzzwords, slaps their brand on it, and sells it.
‘Detection theft adoption’ isn’t new. As far back as in 2009 we conducted an open experiment that showed the scale of the problem catastrophe. Since then the situation’s only gotten worse: start-ups have appeared whose whole business model is based on a constant free-ride via VirusTotal. Invest in development of technologies and infrastructure and pay (top whack) salaries to (top notch) experts? Naah. We’ll just recycle other professionals’ work, re-brand it and resell it, thank you. Sure it’s a rum do; but it’s legal.
At times the audacity of the parasites is off-the-scale; some even openly admit to using VirusTotal’s multiscanner as the basis for ‘their’ detection. Here, for example, is some jaw-droppingly shameless marketing drivel (here’s a copy of the document) to demonstrate this:
I mean, practically every sentence in the above paragraph causes involuntary facepalm – sometimes double facepalm. But the triple facepalm comes in the underlined sentence, which basically says ‘we use Virus Total [sic] for our detection’.
Here’s another example (here’s a copy of the document, just in case):
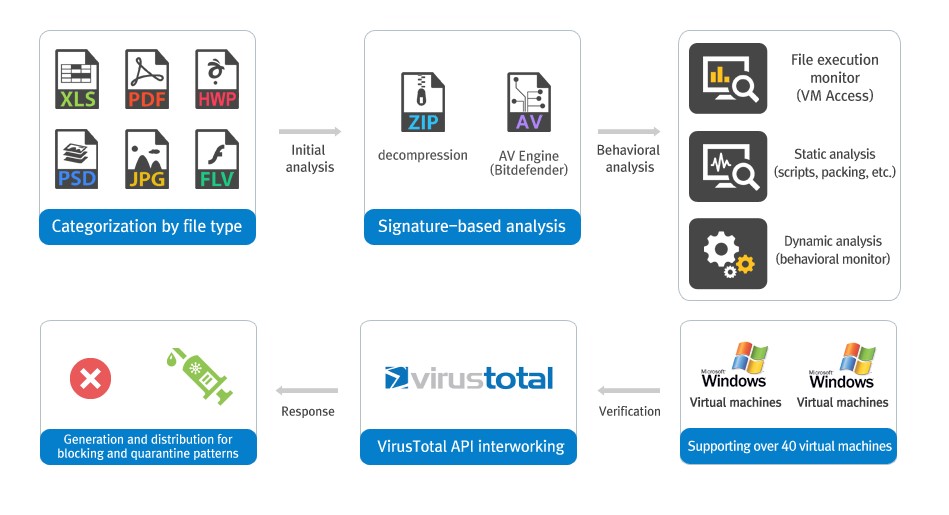
Here we get something similar to the first example. First the product conducts some opaque analysis wrapped up in the suitably fashionable white-coaty words behavioral analysis, then it turns to the VirusTotal API – for a spot of ‘interworking’ – then it returns the verdict to the user. In other words, no matter how super-duper the result of the intelligent analysis is, their verdict all the same depends on the opinion of other scanners. What’s the point of all their intelligent analysis, then? Good question.
There are a lot more examples like those above, and they all testify to the fact that detection adoption has become the norm in the IT-security industry; and based on that, a whole ecosystem of parasites now successfully bullshits (successfully – i.e., keeps getting away with it!) the public. No, I am not making this up.
What all parasites agree on is their opposition to ‘traditional methods’ (the very same scanning methods they adopt via VirusTotal) and their love of all things ‘next generation’ (though what exactly is new about detection copy-and-pasting – and also AI – they don’t point out).
Conclusion: if you get approached by folks from an unknown company bandying about words like ‘next-gen’, ‘behavioral analysis’, ‘artificial intelligence’, etc., with no results of independent tests to make those words mean something real, watch out. The marketing materials of such companies show that the only artificial intelligence they use is that for peaking on real IT-security companies via the cloud.
VirusTotal knows about the problem and is doing its best to solve it. On May 4 new policies for using its system were published; main points: all users of the private API need to “integrate their detection scanner in the public VT interface“, and “new scanners joining the community will need to prove a certification and/or independent reviews from security testers according to best practices of Anti-Malware Testing Standards Organization (AMTSO)“. Experts reckon (don’t forget to read the comments) that these rules will clean up the situation at VirusTotal and see the parasites off.
"Cylance, Palo Alto Networks, Crowdstrike, Carbon Black and Sentinel One are the ones I might be concerned about" https://t.co/6SXTbXIrzQ
— codelancer (@codelancer) May 6, 2016
These new rules – it’s the right move to make, albeit an overdue one. But I don’t think VirusTotal should stop there. Now is the right time to continue similar reforms at VirusTotal. Why? Because the parasites still have a few tricks up their sleeve – ways to get round the new requirements and continue to suck expertise from the multiscanner.
IMHO, the things that need doing first:
- The public version of the multiscanner needs to be improved in order to make automated queries with anonymizing techniques as difficult as possible;
- The participants themselves should decide who gets access to the results of their scanners.
That's one small step for @virustotal, one giant leap for security industry https://t.co/rMKH0LgS7T by @alexeck
— Eugene Kaspersky (@e_kaspersky) May 6, 2016
We’re not the only ones unhappy with the abuse of VirusTotal, and I’m certain that further changes to the service will be supported by many of our colleagues – in particular from those who also make genuine contributions to the VirusTotal community. No one wants parasites getting the fruits of their hard toil, but everyone is ready to share expertise with respectable colleagues, CERTs, law enforcement, and other anti-criminal organizations; put another way – any organization that cooperates instead of copies. Detection adoption is killing the IT-security industry and indirectly assists cybercrime.
PS: VirusTotal is the most well-known, popular and advanced – but not the only multiscanner available. There are also Jotti, VirSCAN, Metadefender and similar services, though they too each have drawbacks. Each needs to do some… housekeeping in order to eliminate continued abuse. And yes, I hope VirusTotal will be the example to follow by all of them.
.@e_kaspersky slams #ai_oil parasites that abuse VirusTotal by copying other vendors’ detectionTweet