March 5, 2013
The sysadmin: the controller, the gatekeeper, the security-police, and more. Don’t mess.
The system administrator – also sometimes affectionately known as the computer guy/girl – is a fairly well known figure at any company with more than a handful of employees. Stereotypes abound for sysadmins, and even sitcoms are made about the genre. But a lot of those are out-of-date and silly generalizations (my sysadmin @ HQ is neat and well-groomed – verging on the Hipster, with long blond fringe and side parting!)
So, really, just who is the sysadmin?
Right. All of us – computer users – are divided into three categories in terms of the answer to this question. To the first category, a sysadmin is an angry bearded devil, a computer whiz(ard), and a shaman – all rolled into one. The second category also attributes to sysadmins certain otherworldly traits, but strictly positive ones worthy of repeated bows plus a small gift on every worthy holiday (especially Sysadmin Day). Then there’s the third category of computer users – who don’t take either of these two views of sysadmins; these folks understand they’re just normal folks like the rest of us. And this third category includes the sysadmins themselves!
The shamanic work of sysadmins is eternally interesting: assembling brand new shiny kit, connecting it up with cables (or without them), and also commanding control over mice and keyboards – sometimes from thousands of miles away – and installing or reconfiguring software on a comp from the comfort of their own workplace. However, at the same time the work is hard, incredibly accountable, and, alas, in part thankless.
First of all there are the hundreds or thousands of users who all need to be kept happy – most of them clever-Dicks! Then there are the ever-increasing numbers and types of computers and other newfangled devices – all of which need attention and care. And of course there’s the jungle of software, cables and routers, problems with security… And to top it all off there are the ever-present budgetary constraints and dissatisfaction of the management and users. So it should come as no surprise that only sysadmins with iron psyches and healthy, cynical attitudes to life are the only ones who can cope with the job!
Perhaps the biggest headache for sysadmins is how to physically manage all the tasks under their remit. Installing Office here, correcting a setting in Outlook there, connecting a new comp in the neighboring building, and then getting through another 48 tasks scattered all over the office(s) is all going to result in nothing other than sysadmin burnout! Enter systems management to ease the burden…
The majority of routine operations for controlling a network can either be fully automated, or at least performed remotely, without excessive movement about the office. Upgrade an OS on a comp? Install an application? Check what software is installed on the chief accountant’s laptop? Update antivirus and scan a computer for vulnerabilities? Prolong a license? Correct some pesky setting that’s preventing a program from working as it should? All that and a lot more the sysadmin can do today without leaving his/her room with the help of the same systems management. And just think of the improved productivity of labor and lowering of costs! And how much simpler the life of the sysadmin becomes!
In the early 2000s a control system for the security of a network appeared in our products. It formed a teeny-weeny (but oh-so important) part of systems management, responsible for the monitoring of protected workstations, installation and updating of antivirus, and so on.
Returning to the problems of the sysadmin – it turns out that he/she may have several if not dozens of such control systems for each of his/her tasks. Again – disorder! Each system needs studying and getting used to in order to facilitate automation processes, and of course each one costs money, demands extra hardware resources, and extra bums on seats. And budgetary pockets aren’t bottomless!
So are there such control systems that do everything? Yes – there are. However, they cost an arm and a leg, it’s impossible to understand how they work “without downing a bottle of vodka” (as the saying goes in Russia), and they dictate strict set lists of compatible software.
So, is there another option – a compromise?
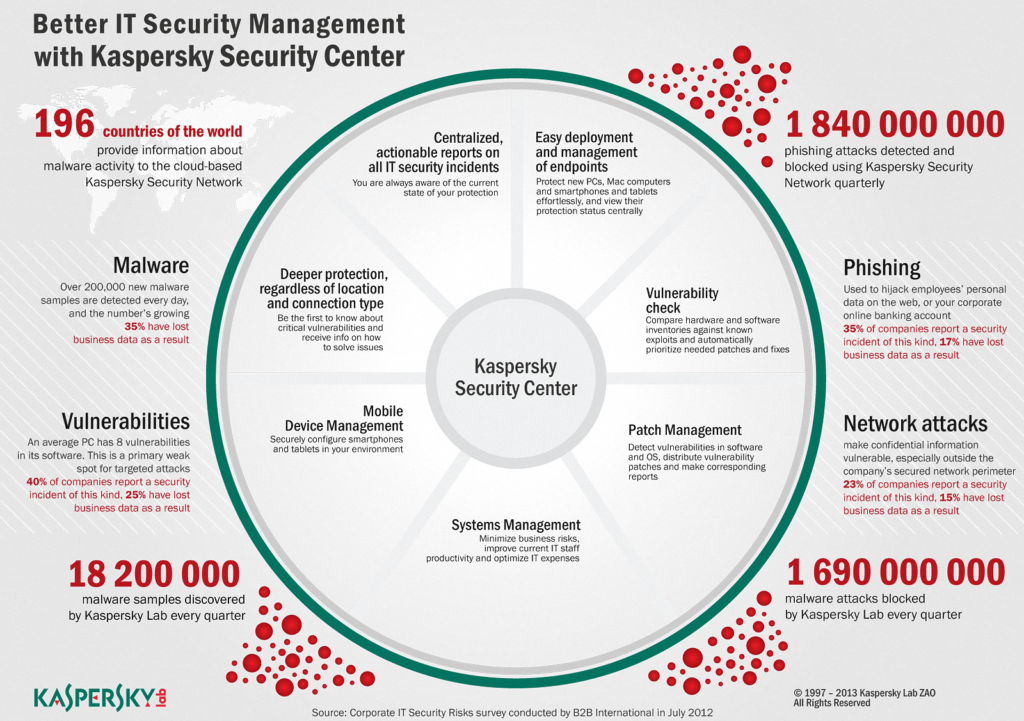
And this is what brought us to coming up with another interesting feature of our new corporate product… yes, now we have our own fully-featured systems management, which goes much further than simply controlling the antivirus protection of the network. Here we also have a multitude of levers for centralized control (see below) in a single console, and all for a realistic, accessible price.
The features of our systems management can be split into three groups:
Deployment & Maintenance
- Centralized, remote installation of OS and software on workstations and servers, and, in combination with MDM – on mobile devices. For example, it’s poss to create images of OS with optimal settings and launch an upgrade project for the whole network, segment, or separate workstations on Windows 8 – all scheduled to take place in non-working hours (including via Wake-on-LAN), and with accompanying traffic economies should such an upgrade project be carried out for external offices through the use of local update agents;
- Remote inventorization of both software and hardware with automatic discovery of new devices and applications;
- Remote license management;
- Remote blocking of pirated software;
- And if a user gets into some bother of some sort, it’s possible to connect to his/her computer on a secure channel and conduct diagnostics and if needed carry out some “surgical” intervention.
Extra Security
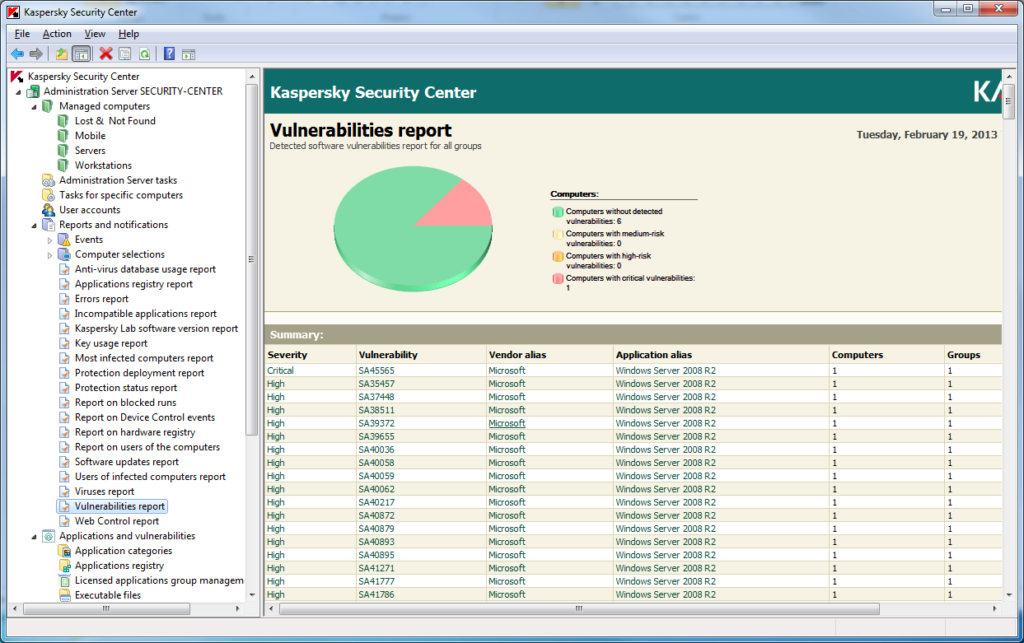
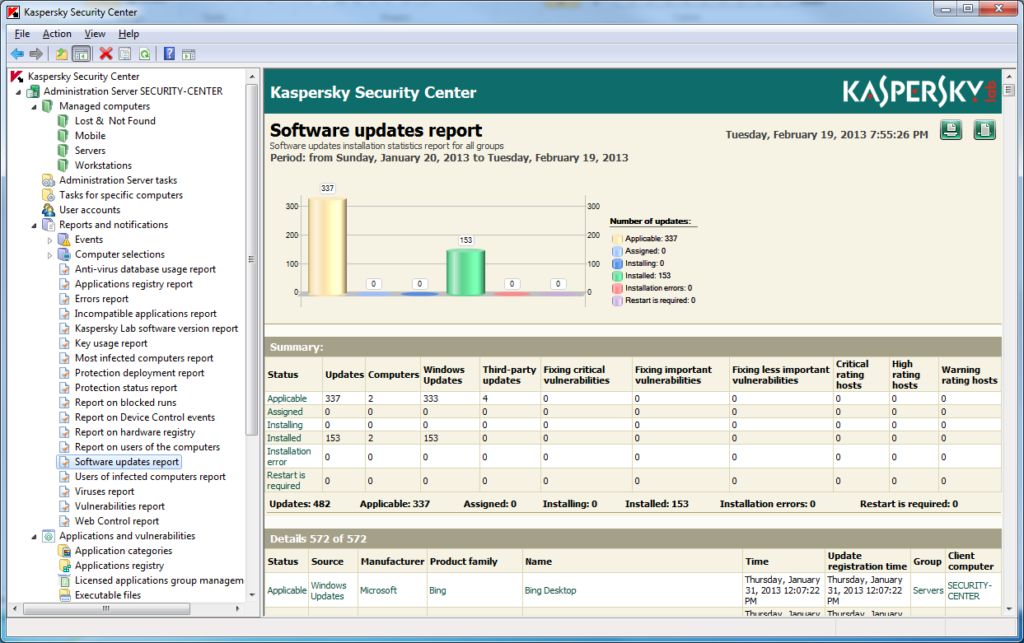
Besides the long-ago introduced centralized installation, settings and management of protection, it’s now possible to scan networked computers for vulnerabilities (vulnerability assessment) and install patches (patch management). And I don’t mean a common database of Windows vulnerabilities: our system combines Microsoft WSUS for centralized downloading and installation of MS updates, data from the respected research company Secunia, and our own expertise in the field of discovering vulnerabilities, which supports a large number of products of third-party companies. The latter is a particularly important element. Thanks to this homegrown expertise, powered by our cloud-based KSN, we not only track the development of emergency situations on the Internet 24/7 and quickly release patches, we also cover a much broader spectrum of different types of software.
Policies
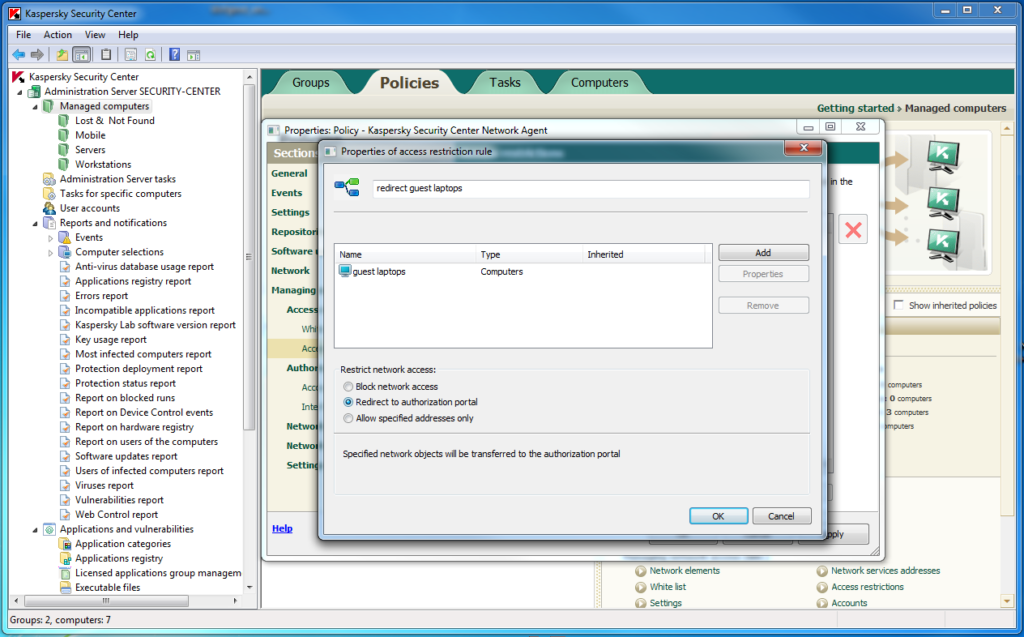
Our systems management allows for various automatic actions depending on the given circumstances (known as policy enforcement). Examples: rules can be established limiting access to corporate resources for “guest” devices (Network Access Control, NAC); corporate software standards can be fully supported – as can new device policies; and with MDM, mobile devices can also be managed automatically. In fact, theoretically it’s possible for a sysadmin to establish security/network rules to prevail over practically any action of users!
All these controls are managed centrally from a single console – the Security Center. It’s here where reports and warnings from all around the network come to, the overall state of the network is monitored, and incident tracking, early warning and prevention takes place – kinda like an all-seeing eye – or science fiction super computer :).
What’s more, the system’s fully scalable – one control server is able to control up to 50,000 computers and mobile devices, a hierarchy of administrators can be set up apportioning access rights, and there’s integration with Active Directory.
What can we expect in future versions?
Well, the plans are positively prodigious. In our systems management we see real potential for strengthening what’s already featured and furthering our competitive offset. We’ll be introducing new management features and extending the list of supported third-party software. Also on the horizon are a SaaS version and support of heterogeneous networks (management of Linux and Mac computers).
Automation is, of course, good for all, but there is one potential downside… personal contact all but disappears and folks forget what other folks looks like. Intranets/corporate sites with profiles of everyone in the company of course help, but still… Well, we’ll have to wait and see how it all pans out in the future: remote automation creating an impersonal, dystopian workplace, or progress being flexible enough to come up with new solutions to old problems (like putting names to faces :).
That’s the tall and short of it. More details about our systems management you can read here (pdf) or on this site.