June 10, 2025
Cybersecurity – past, present, and a little into the future: a reality check.
People often ask me what I talk about these days at the numerous conferences I speak at around the world.
Most of my talks aren’t deep technical dives or analyses of specific cyberattacks. For those, our experts give detailed presentations at specialized events, and publish articles in cybersecurity media. I usually provide a broad overview: discussing what’s happening in the world of cybersecurity, the pressing issues, and where everything’s headed. I almost always have a basis, or template, which I generally adapt for a particular audience or event…
For example, in this post let me share what I discussed at a recent conference of ours in St. Petersburg.
Since the conference was called “Cybersecurity of the Future”, I gave cybersecurity forecasts: what threats we’ll face, and how we’ll tackle them. But before that, as is customary for me, I first gave a brief historical overview of IT-villainy – “from Adam to… Telegram”.
Cybercrime: how did it all start?
So why do we need to dive into the archaeological past and the relics of various malware? Well, because if you don’t know the past, you can’t predict the future. So we look back to events of the past so we can analyze what’s happening here and now and why. Moreover, we’ve been known to be rather good at accurately predicting future cyber-scenarios (more on this below). So let’s roll back around 20-25 years, and remember how the computer mischief of the late 20th century turned into a whole industry of international crime – and a serious problem for humanity on a whole.
The 90s – the early 2000s
While connecting to the internet was done through those strange-sounding dial-up modems, early malware was mostly enthusiasts’ fun and games. Nevertheless, a few colleagues and I, working then at a small, struggling company (I guess it could be called a startup), were observing with great interest how the landscape was changing.
I remember some time in the mid-90s how I asked those colleagues an innocent question: “Is it possible for someone to create an internet worm?” That is, malicious code that would spread itself across the internet, jumping from device to device, clogging traffic to the point of total blockage. “Theoretically, it’s possible,” came the reply. And that was that: we all agreed that, if it’s possible in theory, it would actually happen one day. Yikes…
And sure enough, it did happen – in 1999 and the early 2000s. It came in the form of large-scale epidemics caused by worms like Nimda, Melissa, and ILOVEYOU. But since we’d been expecting such worms for several years already, they came as no surprise: we were ready for them. And of course our products quickly learned how to catch these nasty creatures automatically.
As time went on, the number of folks online multiplied exponentially, and that’s when real “internet money” appeared online for the first time. Sure – back then there was no online banking, no online payments whatsoever (let alone mobile payments), but cybercrime still started taking its first baby steps – setting up websites, starting newsletters, creating viruses – and eventually forming its early business model.
Later came the mobile phone revolution, and then smartphone one ushering in mobile malware – the kind the world’s still afflicted by today (though that’s closer to the 2010s – coming up next…).
The 2010s
While in the early 2000s only a few company executives and high-level government officials seriously thought about the dark side of scientific and technological progress – and at the same time were completely unaware and uninterested in cybersecurity issues, in the 2010s cybersecurity turned into one of the hottest topics on the planet.
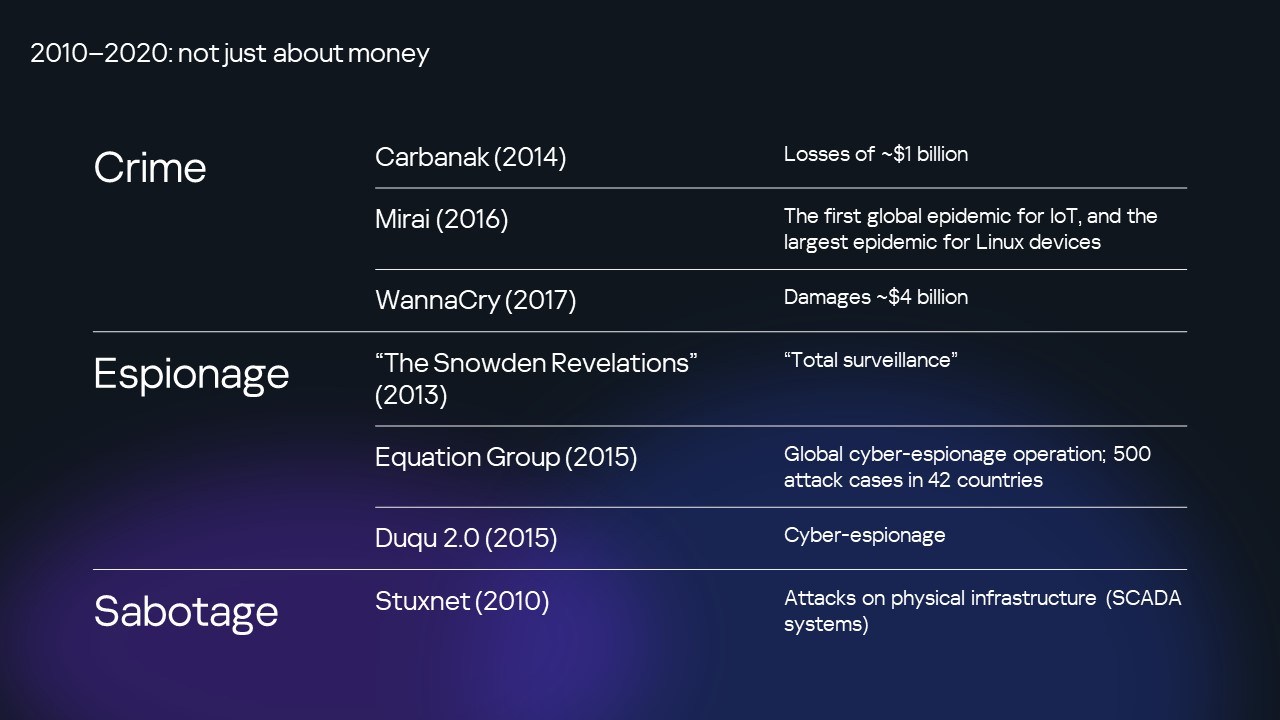
Just as before, we were always closely monitoring the development of the cyberthreat landscape and discussing where everything was heading. Alas, almost all our forecasts came true. To list just a few: attacks electronically robbing banks, attacks on industrial infrastructure (cyber-sabotage), ransomware as a mass cybercriminal business, and also hacks of the Internet of Things.
Carbanak stole a billion dollars from banks. Stuxnet attacked the Iranian nuclear program with a trojan targeting physical equipment – uranium enrichment centrifuges. There were countless spy attacks (e.g., Equation and Duqu, to name just two). Then there was Wannacry – a ransomware worm that caused a global epidemic in 2017 (I recall I was at the airport in Dubai and wondering: “Is it even safe to fly? Turned out it was; phew!)
The roaring 20s
So what about now?…
In this decade, cybercrime is causing hundreds of billions of dollars’ worth of annual damage to the global economy (some say more than a trillion). Sophisticated attacks become ever more refined, and these malicious technological innovations are then used for attacks of a much larger scale.
On an average day, we process around 15 million files; that’s seven times more than 10 years ago! Naturally, not all of that is done manually, and our automation and machine-learning (aka artificial intelligence) have been helping out immensely for… decades already (really!). But the bad guys are always mastering such new tech too…
For instance, last year deepfake phone calls became popular, where fraudsters, imitating a voice, would demand money transfers on behalf of a company executive. The source of such fraud unexpectedly turned out to be Latin America, but the technology then quickly spread. Also, AI-based frameworks are emerging that can create malicious code with the required specific characteristics to order. It’s not a mass phenomenon yet, but its proliferation is just a matter of time.
Two years ago, one of the most complex cyber-espionage operations in history, Triangulation, showed that even iOS – with its famously closed ecosystem and reputed security (actually…) – isn’t immune to vulnerabilities inside the operating system’s architecture. Our experts discovered that the processor on iPhones was practically in debug mode, which provided full access to the device’s memory to anyone with knowledge of (i) the respective undocumented calling protocols, and (ii) the undocumented system functions. It’s such an astonishing story…
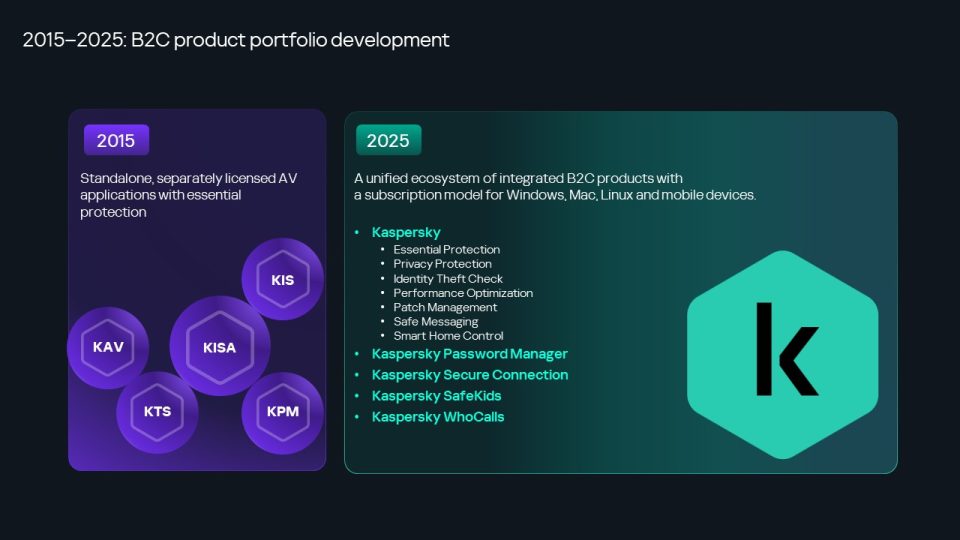
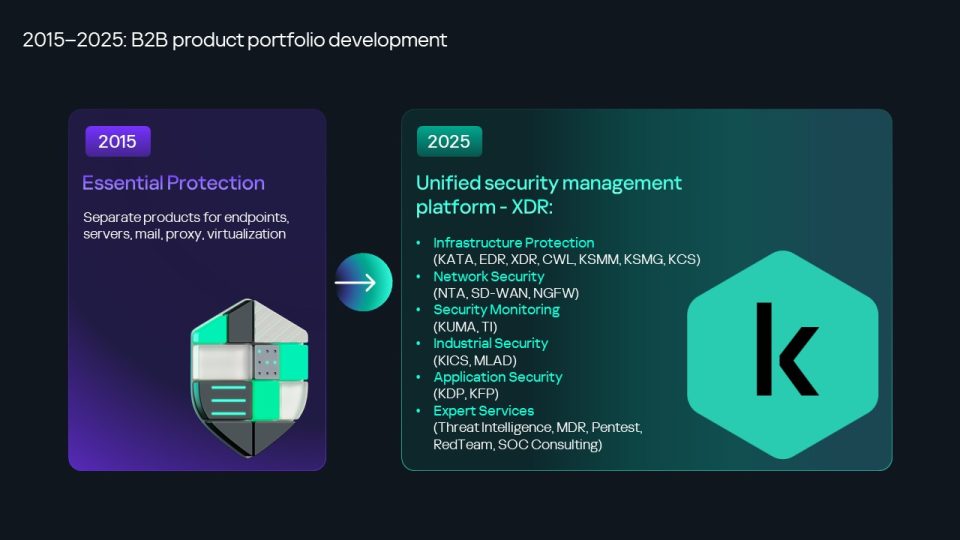
But it’s not all bad news. The good is that cybersecurity doesn’t stand still. Technologies evolve – bringing new solutions and methods of protection. Regarding us, what was once a small antivirus company has grown into a whole ecosystem. Ten years ago, our B2C and B2B products were a disparate set of separate applications. Today, firstly there are significantly more products – but just as importantly they’re also integrated into a single platform. For example, we’re actively working on our open XDR platform (which includes at a minimum EDR, TI, and SIEM…), to counter the most complex and professional cyberattack methods – protecting both office and industrial networks. Automation, threat intelligence, anomaly detection, anti-fraud, and the processing of millions of suspicious files a day – it’s not all just marketing, but real working tools. And even open-source code can now be checked; for instance, by the end of last year, our experts had found over 14,000 infected open-source projects. No joke!
We’re also developing our own microkernel-based cyber-immune operating system, on the basis of which solutions secured by default are already being created. The approach to creating IT systems with constructive security (security-by-design) is slowly but surely making its way to the masses – especially in the field of critical infrastructure. Yes, it’s a difficult process that requires a mindset shift and stepping out of the comfort zone, but without it humanity is going to hit a dead-end in its development – instead of spending resources on developing new technologies, they’re spent on patching holes in last century’s architecture.
What lies ahead?
Overall, we’re continuing to live with thoroughly flawed IT infrastructure, and each year the number of discovered vulnerabilities grows, attacks become all the more sophisticated, and their vectors expand. Cybercrime will become more professional, with cybercrooks developing increasingly cunning penetration technologies. Alas – that’s human nature. There’ll be more sabotage and terrorism, espionage, new vulnerabilities, attack automation, maybe even cyber wars (I really do hope not – especially on a large scale). Critical infrastructure objects will be at risk, and attack damage will be so significant… let’s just say it won’t be measured just in money. The good news though is that all that is the worst-case scenario. Curiously, in the past we were able to come up with a progression of one scary scenario after the other, whereas today we’re running out of scenarios: it seems almost impossible now to imagine anything more terrifying than what we already fear.
But back to the positive…
Like I say, the cybersecurity industry is also developing, and in general information technologies are becoming safer. Compare mass-manufactured operating systems today to 15-20 years ago! Progress in terms of security is enormous! But it’s still sorely lacking.
In today’s world, where literally everything depends on “digital”, the stakes (and the price of error) have long been scarily high, and they’re likely to continue rising. That’s why it’s necessary to take cybersecurity as seriously as possible, rely on deep expert knowledge, and implement innovative techniques and best practices.
I personally remain optimistic, but understand that many devastating attacks lie ahead. One could say c’est la vie and… merde happens, and leave it there. But no! Absolutely not! Never give up!
Our nearly 30 years of experience have shown us that fighting the cyber-enemy is not only possible but vital. And the experience of our clients shows that applying best practices and technologies really does allow us to stay one step ahead of the threats and be ready for those yet to come…