July 21, 2022
Cyber-tales from the dark (and light) side: audacious crypto hack, K goes neuromorphic, and how to enter a data-center via a… toilet!
Hi folks!
For those still sweating it out in the office, not lucky enough to have left for some serious digital detox vacationing, herewith, to keep your mind off the heat, some juicy iNews, aka Dark (and Light) Tales from the Cyber Side – yet more extraordinary, hard-to-believe stories from the world of cybersecurity.
Crypto-decrepito
The gaming community will no doubt recall how, this spring, Axie Infinity, the online crypto-game (perhaps most notable for permitting virtual winnings to be exchanged into real money), suffered one of the largest robberies of all time. It appears highly likely that North Korean hackers broke into the Ronin blockchain that controls the game, and proceeded to steal around $625 million (the exact figure varies depending on the source) from users’ accounts! The incident went unannounced for a time, highlighting the vulnerability of the game’s security system, and putting the reputation of its developer behind – Sky Mavis – on the line too.
Oh my gigantic sum! But wait – that’s not all; there’s more!…
Earlier this month it was revealed precisely how the hackers managed to break into the blockchain. Are you sitting down?!…
Several months ago fake employees of a fake company on LinkedIn sent info about fake job vacancies to employees of Sky Mavis. A senior Axie Infinity developer decided to apply. He even got through several rounds of (fake) interviews, after which he was offered an extremely attractive (fake) salary and benefits package. Basically, he was made an offer he couldn’t refuse.
Said offer eventually arrived in the developer’s inbox in the form of a pdf document, which he had no qualms about downloading and opening on his work computer. And that was that – the bad guys were in. Henceforth it was all just a matter of technique: an espionage program infiltrated Ronin, via which they were able to seize four of the nine validators that protect the network. Access to the fifth validator (needed to complete the hack and then steal all the money) was gained by the hackers via the Axie Decentralized Autonomous Organization – a group set up to support the gaming ecosystem. Result – bingo; jackpot!
Though the hack didn’t lead to a direct theft of tokens, Sky Mavis still had to temporarily freeze all gamers’ accounts, and the company worked with law enforcement agencies, cryptographs and investors, to make sure that all losses were fully reimbursed. Ah yes – one other thing: remember the developer who applied for the fake job? He was fired. Shocker!
This tale shows how even the most experienced techies can get caught out by phishing – with grave consequences. Alas, it’s clear that this incident won’t stay unique or even rare – more like it are bound to be on the way; perhaps the main reason: blockchain-based gaming is attracting some seeeerious investment of late. And this, in turn, is bound to attract cybercriminals of all stripes – from low-skilled amateurs to professional APT groups.
A new – neuromorphiK – direction
Our experts are currently actively involved in the development of neural processing units. In line with this, just recently we invested in the start-up Motive Neuromorphic Technologies.
This business direction is a wholly promising one. The architecture of neuromorphic processors is based on the principle of the human brain; they’re much quicker than traditional processors, while consuming much less energy. Basically, they’re just what are needed for processing huge volumes of data, which are getting huger by the day. They’re also just what machine learning technologies are screaming out for. Solutions with neuromorphic chips will be used in the manufacture of drones, face recognition systems, in robotics, for the Internet of Things, in industry, and so on and so forth. You can find details about why we firmly believe neuromorphic processors are the future here.
Btw: we’re also looking for partners to launch pilot schemes using the “Altai” neurochip. Interested? Let us know!
A literal, physical, backdoor vulnerability!
To finish – some irony…
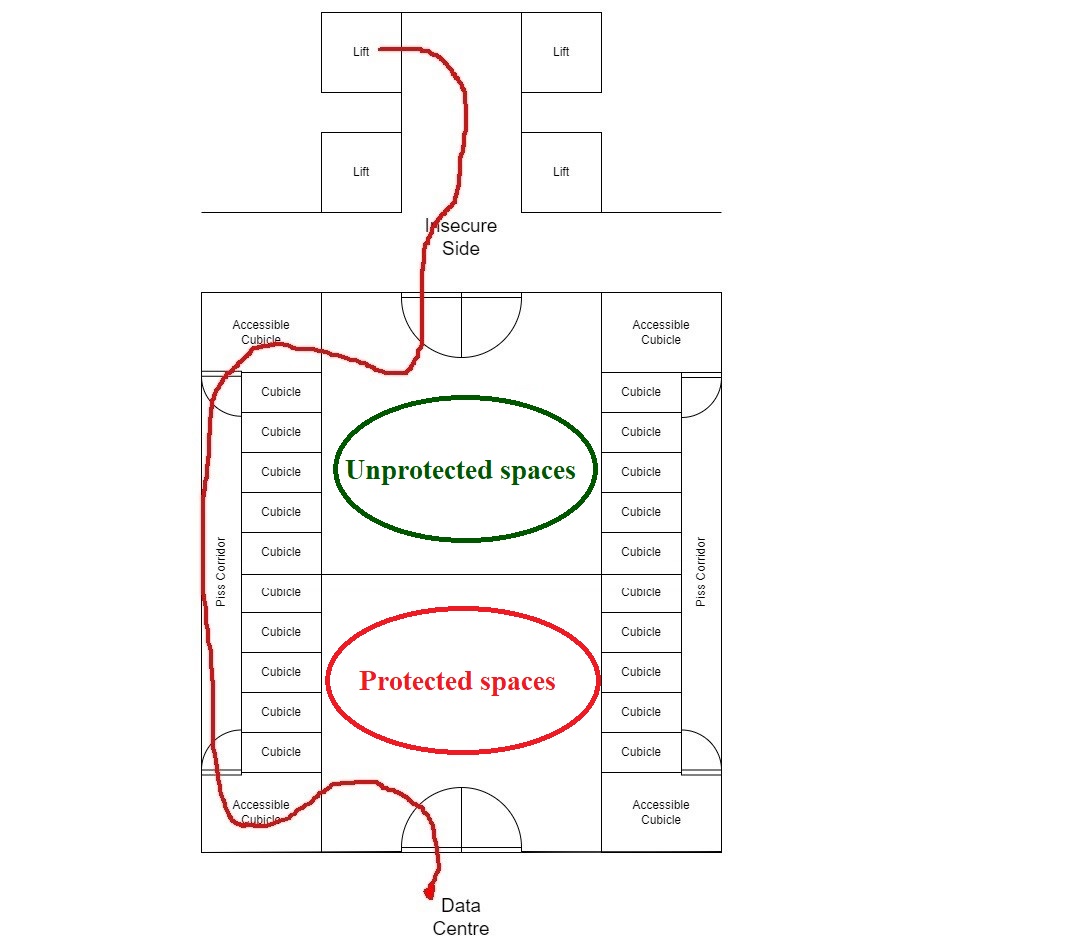
I’m referring to the seemingly funny (at first glance) story of a resourceful pentester who managed to penetrate a data storage and processing center via… a toilet!
Having studied the floorplans of the data-center building during a penetration test, the InfoSec specialist found that along – behind – the back wall of a floor’s gents’ restrooms there’s a narrow service corridor for plumbers (“only”!) to use for access to the toilets in the cubicles that line that wall. All would be as per the norm but… it turned out that this workman’s corridor connected unprotected spaces of the data center with (extremely highly!) protected ones.
Thus, the pentester was able to enter, unhindered, through into the “secure” area via a door at the back of the disabled cubicle that backed out onto to the passage. He bypassed cylinder man-trap gates that included surrendering all digital devices too. And this gaping hole in security in a “high-security” facility is/was viewable in publicly accessible planning documents! Alas – again, I can’t say such absurd security lapses are rare; they just seem to be rarely reported. That doesn’t make the tale any less juicy (thus, its inclusion here:).
And that all for today folks. Now I’m headed out on a lengthy vacation (pics and text, afterward!). And I hope you’ll be doing something similar soon too. Just… try not let the heat go to your head ).