December 22, 2016
Uh-Oh Cyber-News: Infect a Friend, Rebooting Boeings, No-Authentication Holes, and More.
Hi folks!
Herewith, the next installment in my ‘Uh-oh Cyber-News’ column – the one in which I keep you up to date with all that’s scarily fragile and frailly scary in the digital world.
Since the last ‘Uh-oh’ a lot has piled up that really needs bringing to your attention. Yep, the flow of ‘Uh-ohs’ has indeed turned from mere mountain-stream trickle to full-on Niagara levels. And that flow just keeps on getting faster and faster…
As a veteran of cyber-defense, I can tell you that in times past cataclysms of a planetary scale were discussed for maybe half a year. While now the stream of messages is like salmon in spawning season: overload! So many they’re hardly worth mentioning as they’re already yesterday’s news before you can say ‘digital over-DDoSe’. “I heard how they hacked Mega-Corporation X the other day and stole everything; even the boss’s hamster was whisked away by a drone!”…
Anyway, since the stream of consciousness cyber-scandals is rapidly on the up and up, accordingly, the number of such scandals I’ll be writing about has also gone up. In the past there were three of four per blogpost. Today: seven!
Popcorn/coffee/beer at the ready? Off we go…
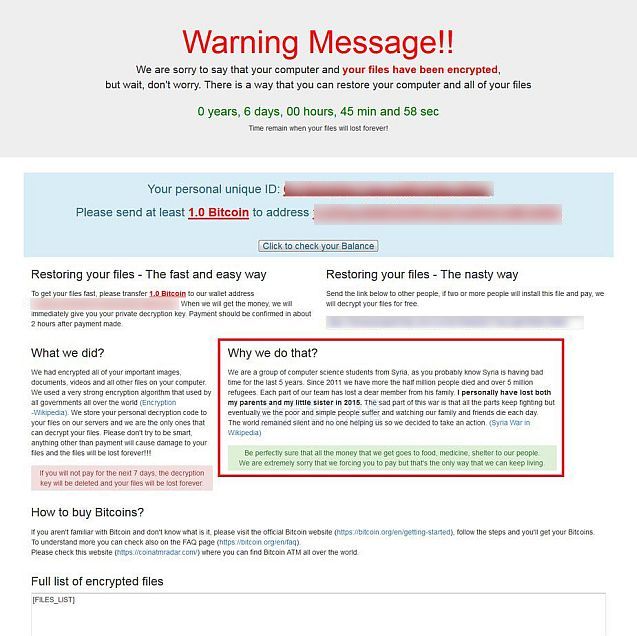
1) Infect a Friend and Get Your Own Files Unlocked for Free.
Cybercriminals have long been carrying out their unlawful activities as a business. And we recently heard about a new way in which they now resemble legal business – they had a ‘partner conference’ where they all got together to discuss cooperation and strategy. I bet they’re reading marketing and management textbooks too. Still, it’s all fairly logical: How do you build up a business? You think about products, services, improvements, organizational structure, channels and the rest of it.
So I guess it was logical to see this novelty appearing too. Someone’s come up with a new market-expansion tool for ransomware: “Infect two people you know with the malware that we’ve infected you with, and we’ll give you the key to open your own files for free!” They’re just too kind.
Each victim of such ransomware will be wondering: ‘Did I click on or open something I shouldn’t have? Is it me who doesn’t have sufficient protection? Or could it be some friend slimeball who’s to blame?
Mercifully, this ransomware didn’t occur in the wild (at least – no instances have been found); for now it’s a mere research project found deep within the murky cyber-waters of the Dark Web.
2) Effective Hacker Headhunting.
An serious problem for any organization: how do you find the right people and motivate them to work effectively? In line with modern business trends, certain organizers of DDoS attacks from Turkey have built a gamification platform for DDoS attacks in which participants compete with one another to earn points. The points can later be converted to hacker tools and click fraud software.
The platform is patriotic, suggesting as DDoS victims ‘enemies of Turkey’ from the PKK to Angela Merkel. Participants are enrolled on underground forums on the Dark Web. Politically-motivated crowdsource DDoS’s have already occurred of course, but now here enterprising hackers have migrated them to a convenient platform with an established participant motivation system. I have an image of an MBA graduate as the one who’s thought all this up…
3) The Return of Shamoon, and the Difficulties in Attributing Cyberattacks.
It’s been reported that hackers have attacked the Saudi central bank, plus a slew of other official bodies and other organizations in Saudi Arabia with the help of the bad-old wiper Shamoon. Apparently, the Saudi civil aviation agency ground to a halt for several days, though the airports remained open.
Let me remind you how this malware has already caused trouble before in Saudi Arabia. In 2012 with its help certain cyber-scumbags wiped all the data and all the backups of Saudi Aramco – the largest oil company in the country world. Obviously you can imagine the damage done to have been colossal. And here it is again – four years later in the very same country. Again fingers are pointing to Iran as the likely organizer of the attack.
But. The thing is, fingers may point wherever; they don’t prove anything. And this is typical of most if not all cyberattacks, be they advanced or real basic: there’s rarely 100% proof of who’s behind them. In this case – no evidence at all, just a lot of conjecture. Well, there may be proof, but it sure hasn’t been made public for whatever reason.
The same went for the cyberattack against Sony Pictures: not everyone believes the ‘official’ version that North Korea was behind it, and there are quite a few serious alternative versions. It’s just the same today: by far not everyone believes it was Iran behind the latest Shamoon sortie. A certain Middle Eastern publication, for example, has put forward the idea that it might have been the Israelis who were behind it, so as to spoil relations between Iran and Saudi Arabia, which is in Israel’s interest, not Iran’s. All very intriguing and spy-novel, but we’ll probably never find out who actually was responsible.
Attribution. Kinda a fancy word but a very necessary one in cybersecurity. For it’s extremely difficult to be able to accurately attribute a cyberattack, i.e., to determine who’s really behind it. Evidence left behind after an attack is normally scant, plus relatively easy to falsify. It means only guesses can be made as to attribution. Nothing concrete. And this is precisely why we never point any fingers as to who is might be to blame. This stance doesn’t go down well with journalists of course who want their scoop, but that’s only natural. We’d only ever attribute if we were 100% certain we could, and that is never.
Below, the news is mostly on cyber-uh-ohs related to hardware…
4) Don’t Forget to Reboot… Your Boeing!
What happens if you don’t reboot your computer for weeks? The usual answer: it’ll start going slow. But what happens if you don’t reboot a Boeing 787 Dreamliner? Turns out it can for a short time become uncontrollable! This is the reason the US Federal Aviation Administration now requires that all Dreamliners be rebooted every three weeks. If they aren’t, “all three flight control modules on the 787 might simultaneously reset if continuously powered on for 22 days … and pilots could lose control of a Dreamliner”.
Well, I’ve flown on one of these huge birds – and safely landed, so I guess it must have been rebooted in time.
It’s interesting how computer magic is replacing traditional mechanics. In the past the first measures to fix, say, a broken-down car were mechanical – check the fluid levels and top up as necessary, and tighten this and that car part that may have come loose. These days it’s ‘turn it off then turn it back on again to reboot it’ to fix things – including airliners! It’s the new cyber-physical reality – where the physical safety of a lot of people depends on the stability of computers. Eek. Welcome to the brave new world folks!
5) German Blast Furnace Cyber-blasted.
It’s a sad fact that news like this is starting to be taken less and less seriously, as it occurs so often: hackers from the Winnti group hacked German giant ThyssenKrupp to steal secrets of its engineering division. So this is yet another large company to join the long ‘hacked’ list. “It isn’t the first, and it sure won’t be the last, so it’s no big deal really,” the reader sighs. However!…
It is a big deal. When they start stealing secrets of large industrial companies – this should cause alarm, for it’s possible that preparations are being made for other, more destructive cyberattacks in the same vein.
Besides, in this case rumors circulated in the media that this hack was the one anonymously referred to in 2015 in which a large blast furnace had been hacked and wrecked. ThyssenKrupp refutes this. I’m not sure the details of the story will ever be made public. But what can be said of what happened is that it was a very serious cyberattack – in fact the second one to cause confirmed physical damage. And it shouldn’t be just blast furnace operators that are worried…
6) Not-so Smart Meters.
Once again, this one’s about hardware and its vulnerabilities. A manufacturer of solar panels issued a patch for its power meters. Without it, cyber-villains could seize control of the system and manipulate it, for example by communicating incorrect data about supplied energy to the general network. Oh, plus (of course, these days), they could use the solar panels for a botnet to take part in DDoS attacks. The script entitled ‘solar panels DDoS security cameras, which fire back from home routers‘ is edging nearer and nearer reality by the day…
And what was the vulnerability? The default admin password on all devices is the same, and you can find it out by watching the video instructions for the solar panels on YouTube. Real smart.
Don’t forget to reboot your power meter after running the update!
7) More Internet of Harmful Things: But This One’s Just Silly.
The sadly famous story of the infamous Mirai botnet continues, after already earning itself the title of the most powerful DDoS attack in history. Mirai’s most distinguishing factor is that it generally doesn’t infect personal computers, servers, tablets and the like. It isn’t interested one bit in that section of the computer world. It’s like a good startup: oriented at a new reality; in its case – the Internet of Things.
The latest Mirai scandal caused nearly a million Deutsche Telekom customers to go without Internet for a time after it ‘bricked’ their routers. Then it did the same thing with ~100,000 users in the UK. The worm uses the Internet-connected WAN port, through which it’s possible to remotely control the device – WITH NO NEED FOR A LOG-IN OR PASSWORD! How many models have been affected around the world? Hmmm, at a minimum – scores. It makes you want to pinch yourself to check you’re not dreaming it. Just HOW is that possible? NO AUTHENTICATION??? Not even the trusty ‘12345678’ password is needed!!!
Such scandalously poor absent security gets you thinking: how much effort is it going to take for all these gaping holes to be bunged up? You get to think a bit more…: but then there’s all the less-obvious, less gaping holes – the hidden, stealthy ones, which are equally if not more serious. How much effort will it take to bung those all up? Short answer: a lot. So, incidentally, if you’re at that stage in life when you’re thinking of which career to follow, go for cybersecurity: you’ll never be out of a job :).
There you go folks, there’s your last uh-ohs of the year. Hope you enjoyed them, or rather, were shaken up by them. Not that I like worrying folks with uh-oh news, but, you know… someone’s got to do it.
Stay tuned – more uh-ohs coming up in the New Year, you can count on it…